Windows Previous Versions against ransomware
One of the cool features that Microsoft actually added in Windows Vista is the ability to recover previous versions of files and folders. This is part of the VSS (Volume Shadow Copy Service) which allows automatic creation of backup copies on the system. Most users ‚??virtually meet‚?Ě this service when they are installing new software, when a restore point is created that allows a user to easily revert the operating system back to the original state, if something goes wrong.
However, the ‚??Previous Versions‚?Ě feature can be very handy when other mistakes or incidents happen as well. For example, if a user deleted a file in a folder, and the ‚??Previous Version‚?Ě feature is active, it is very easy to restore a deleted file by clicking the appropriate button in the Properties menu of the drive/folder that contained the deleted file. The user can then simply browse through previous versions and restore the deleted file, as shown in the figure below:
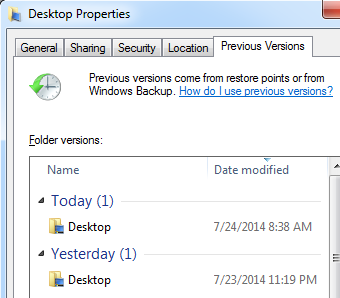
You can see in the figure above that there are actually multiple versions of the Desktop folder that were saved by the ‚??Previous Versions‚?Ě feature. A user can now simply click on any version he/she desires and browse through previous files.
How can this help against Cryptolocker and similar ransomware? Well simply ‚?? when such ransomware infects a machine, it typically encrypts all document files such as Word and PDF files or pictures (JPG, PNG ‚?¶). If the ‚??Previous Versions‚?Ě feature is running, depending on several factors such as allocated disk space for it as well as the time of last snapshot (since ‚??Previous Versions‚?Ě saves files comparing to the last snapshot, which would normally take place every day), you just might be lucky enough that *some* of the encrypted files are available in ‚??Previous Versions‚?Ě.
Monitoring ‚??Previous Versions‚?Ě activities
As we can see, by using this feature it is very simple to restore previous files. This is one of the reasons why I see many companies using this feature on shared disks ‚?? it can be very handy in case a user accidentally deleted a file.
However, there are also security implications here. For example, a user can restore a file that was previously deleted and that you thought is gone. Of course, the user still needs access rights on that file ‚?? if the ACL does not allow him to access the file he won‚??t be able to restore it, but in case an administrator set ACL‚??s on a directory, which is typically the case, and everything else below it is inherited, the user might potentially be able to access a file that was thought to be deleted.
This cannot be prevented (except by changing ACL‚??s, of course), so all we can do in this case is to try to monitor file restoration activities. Unfortunately, Windows is pretty (very?) limited in this. The best you can do is to enable Object Access Audit to see file accesses and then see what a particular user accessed. That being said, I have not been able to stably reproduce logs that could tell me exactly what version the user accessed ‚?? in some cases Windows created a log such as the following:
Share Information:
Share Name: \\*\TEST
Share Path: \??\C:\TEST
Relative Target Name: @GMT-2014.07.02-11.56.38\eula.1028.txt
This is event 5145 (‚??A network share object was checked to see whether client can be granted desired access‚?Ě), and it is visible which copy was accessed but, as I said, I was not able to have this event generated by this constantly.
Conclusion
The ‚??Previous Versions‚?Ě feature is very handy in cases when you need to restore a file that was accidentally deleted or modified and can sometimes even help when a bigger incident such as a ransomware infection happened. Make sure that you use this feature if you need it, but also be aware of security implications ‚?? such as the fact that it automatically preserves deleted files and their modified copies.
Finally, for some reason Microsoft decided to remove, actually modify this feature in Windows 8. The ‚??Previous Versions‚?Ě tab does not any more exist in Explorer (actually it does, but you need to access files over a network share). For saving local files Windows 8 now use a feature called ‚??File History‚?Ě. It needs to be manually setup and it needs to have an external HDD which will be used to save copies of files. This is definitely better since, if your main HDD dies, you can restore files off the external one, but keep in mind that it needs to be setup manually. Finally, if you use EFS to encrypt files, the ‚??File History‚?Ě feature will not work on them.
| Web App Penetration Testing and Ethical Hacking | Amsterdam | May 18th - May 23rd 2026 |


Comments
"In newer variants of Cryptolocker the VSS is almost always deleted at deployment."
JH
Anonymous
Jul 24th 2014
1 decade ago
Guess it can still help, depending on the version of ransomware that infected the end user's machine.
Anonymous
Jul 24th 2014
1 decade ago
Thinking maybe regex searches on common fileshares perhaps to find changes in filenames en masse or alerting on change/deletion in Windows Previous Versions client config.
Anonymous
Jul 25th 2014
1 decade ago
I've used this forensically to bring down registry hives from systems which I could access admin shares, but not remote registry services. Mapping whole "snapshots" of user's browser cache, documents, and the like.
Anonymous
Jul 25th 2014
1 decade ago
Anonymous
Jul 28th 2014
1 decade ago