Preying on Users After Major Security Incidents
As most of our readers already know, there has been some major publicized password breaches involving LinkedIn, eHarmony, and others. Scam artists have taken notice of these breaches and are using these incidents to prey on confused or unsuspecting users.
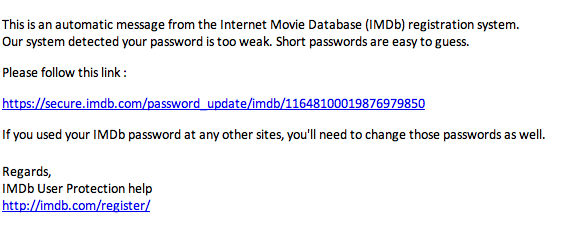
For example, one of our readers received a scam message claiming to be from IMDb. The scam message (see below) claims that there are problems with the security of the user's password which can be corrected by clicking on the link. Anyone who clicks on the link are redirected to a pharmaceutical advertisement site. Similar messages have been seen elsewhere which purported to be from LinkedIn or eHarmony.
Unfortunately, this type of activity happens with almost any major incident, no matter if it is a data breach, natural disaster, or other major crisis. Within the InfoSec community, we need to find effective ways to communicate to our respective user communities about well publicized issues, as well as the scam possibility in the aftermath of the real incident.
Example Scam:
---
Scott Fendley
ISC Handler on Duty


Comments
Louis
Jun 10th 2012
1 decade ago