Increased Traffic on Port 3389
A few weeks ago a diary [1] posted by Dr. J pointed out a spike in port 3389 [2] traffic.
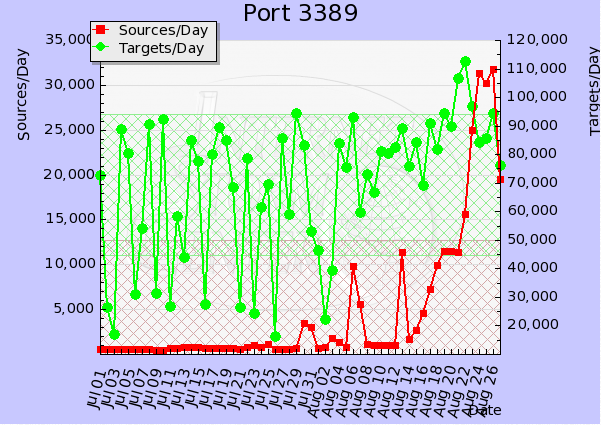
Since then the sources have spiked ten fold. This is a key indicator that there is an increase of infected hosts that are looking to exploit open RDP services.
We're interested to know if any of our readers have come across infected hosts that could be contributing to this port knocking out in the wild.
Tell us what you're seeing and please share with us what you can.
UPDATE:
There is some buzz going around today and many readers have sent in a about a posting on f-secure's website. [3] Where there is a quick write-up describing "Morto" a new Internet worm.
If anyone has a copy of it, then please drop it off through our contact us form. If you have anything to share about worm, then please write a comment about it.
[1] http://isc.sans.edu/diary.html?storyid=11299
[2] http://isc.sans.edu/port.html?port=3389
[3] http://www.f-secure.com/weblog/archives/00002227.html
-Kevin Shortt
--
ISC Handler on Duty


Comments
On my home computer, I have enabled RDP, but only allowing connections from computers running with Network Level Authentication.
In Event View I can find entries under "Applications and Service logs - Microsoft - Windows - TerminalServices RemoteConnectionManager - Operational.
But the entries are only "Listener RDP-Tcp received a connection".
I would like to know: From where did the connection come from, which username were supplied, etc
Anyone?
E
Aug 29th 2011
1 decade ago