E-ZPass phishing scam
Over the last couple of days, we have been seeing a number of quite credibly looking phishing emails that impersonate toll-road providers in the US. The agency affected by the current wave is E-ZPass, a toll charging system used mainly in the Northeast. Adapting the template to match the colors and fonts of other organizations, like Florida's SunPass, would be easy to accomplish for the scammers though, so chances are that we will see more of this.
Since toll road agencies can impose stiff fines for violations or if road and bridge charges are not paid in time, people might fall for it and click on the link just to make sure. In the samples at hand, the link was pointing to www . ruckon . pl (spaces added to de-fang), and returned a ZIP with an EXE or directly an EXE. Hat tip to ISC reader Wayne for providing the latest sample.
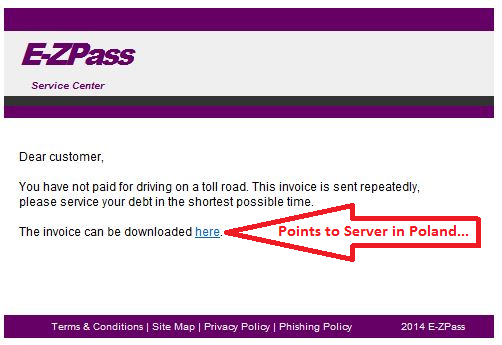
If you receive similar emails that impersonate other toll road providers, please let us know.


Comments
hxxp:// www. poseidwn. gr /tmp/api/X2xAyQ8C9A4[...]LXW1JMDrl+JJADKc=/toll
Mail originated at a server hosted by a company called hostable. I'll email you the full header.
Anonymous
Jul 14th 2014
1 decade ago
http://garwarner.blogspot.com/2014/07/e-zpass-spam-leads-to-location-aware.html
Anonymous
Jul 14th 2014
1 decade ago
Email came from: 188.40.94.66 (hostup.ru)
After the user clicked the link it downloaded an .exe from the viverssantamaria domain above, the machine then started Posting to the following IPs:
207.210.106.58
151.3.8.106
76.74.184.127
88.255.149.11
113.53.247.147
203.157.142.2
91.121.70.14
142.4.60.242
At first glance appears to be some sort of new Kuluoz variant of the ASProx botnet:
http: //www.scmagazine.com/asprox-botnet-campaign-shifts-tactics-evades-detection/article/357472/1/
Snort flags it as "Kuluz/Asprox Activity".
Anonymous
Jul 14th 2014
1 decade ago
The result of the whole event was nontechnical folks sucked it on the initial phishing and us tech paranoids didn't open the legit email because it was packaged in a goofy way. Duh!
Anonymous
Jul 14th 2014
1 decade ago
Anonymous
Jul 15th 2014
1 decade ago
Might be a case of sample bias :). Only people who know what EZPass is are going to recognize the phish as such and report it. Everyone else who opens the email just sees an ugly pink-mauve color scheme, and likely moves on to the next email in their inbox without wasting another thought on this. From the samples that I have seen so far, it didn't look correlated to a specific common source of address information.
Anonymous
Jul 15th 2014
1 decade ago
Anonymous
Jul 16th 2014
1 decade ago
Anonymous
Jul 16th 2014
1 decade ago
Anonymous
Jul 22nd 2014
1 decade ago