Limiting Exploit Capabilities by Using Windows Integrity Levels
Windows Vista, 7 and Server 2008 includes a feature called integrity levels, which is arguably the most under-appreciated security mechanism built into the operating system. Yet, it provides powerful ways for mitigating the risks of computer attacks and malware infections. For instance, integrity levels can shield processes from keyloggers; they can also protect files from being accessed by malware running on an infected system.
Another potent benefit of integrity levels is the ability to limit the capabilities of an exploit that manages to compromise an application. This is what I'd like to discuss in the note below.
What Are Windows Integrity Levels?
Microsoft designed Windows integrity levels as a mechanism for enforcing mandatory access controls, which apply even when access would be granted according to the traditional discretionary controls that we're accustomed to. According to Microsoft:
"The integrity level is a representation of the trustworthiness of running application processes and objects, such as files created by the application. The integrity mechanism provides the ability for resource managers, such as the file system, to use pre-defined policies that block processes of lower integrity, or lower trustworthiness, from reading or modifying objects of higher integrity. The integrity mechanism allows the Windows security model to enforce new access control restrictions that cannot be defined by granting user or group permissions in access control lists (ACLs)."
This means that integrity levels can restrict one process from interacting with another process even if both processes are running under the same user account and even if the user has administrative privileges.
Protecting Higher Integrity Objects from Malware
A process running under the Low integrity level will be prevented by the OS from modifying the process running under the Medium integrity process or from modifying a file assigned the Medium integrity level. (By default, Windows assigns the Medium label to objects.)
This is why it's advantageous to run the processes that are likely to be targeted by exploits under the Low integrity level. For instance, if a browser running under the Low integrity level gets exploited, the attacker's payload will have a hard time injecting itself into the majority of other processes or modifying critical files.
Didier Stevens illustrated the effectiveness of integrity levels for mitigating DLL injection risks by showing how the OS blocked the injection attempt from a Low integrity level process to a Medium one. He concluded that integrity levels may be a "good security feature to sandbox vulnerable, Internet facing applications."
Applications Designed to Run Under the Low Integrity Level
Though it may be possible to force an application to run under the Low integrity level if it wasn't designed for it, this will likely cause issues, such as the application not being able to load its configuration settings. Fortunately, some end-user applications are designed with Low integrity level in mind when they run on Windows Vista, 7 or Server 2008:
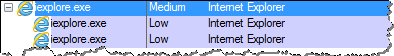
Internet Explorer's parent process runs under the Medium integrity level, while the process that represents each tab runs under the Low integrity level, thanks to the browser's Protected Mode feature:
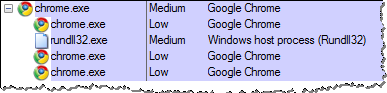
Similarly, Google Chrome runs its tabs under the Low integrity level on Windows as part of its sandboxing capabilities:
Acrobat Reader 9 and lower runs under the Medium integrity level, like most processes in Windows:
![]()
Fortunately, most of the code of Acrobat Reader X runs under the Low integrity level. This is one of the security features built into this version of Acrobat to limit the capabilities of exploits delivered to the application's users through malicious PDF files:
![]()
Running a process under the Low integrity level helps minimize the damage it can do when exploited by malicious code. Hopefully, more programs will be build to take advantage of this feature of Microsoft Windows (ahem.. Firefox?).
-- Lenny Zeltser
Lenny Zeltser leads a security consulting team and teaches how to analyze and combat malware. He is active on Twitter and writes a daily security blog.


Comments