How I made a qwerty ?keyboard walk? password generator with ChatGPT [Guest Diary]
[This is a Guest Diary by John Grant, an ISC intern as part of the SANS.edu BACS program]
Introduction
I have noticed default passwords and keyboard walks are some of the most popular passwords found in the SSH/Telnet logs on my dshield honeypot. It is a known issue in the Cybersecurity industry and often found throughout compromised password dumps. Users believe long keyboard walks are secure however, it can be is easily guessed by attackers even when the password includes numbers and shift to create special characters.
Password spraying attack background
Password spraying is a common password attack in enterprise networks where the attacker takes a small amount of passwords and spray them against all users with the hope of finding a user using a weak or guessable password. Once the attacker compromises one user they can query Active Directory with the Powershell command “Get-ADDefaultDomainPasswordPolicy” which will allow the attacker to enumerate the lockout policy and how to continue spraying passwords on the enterprise network without the risk of locking out accounts.
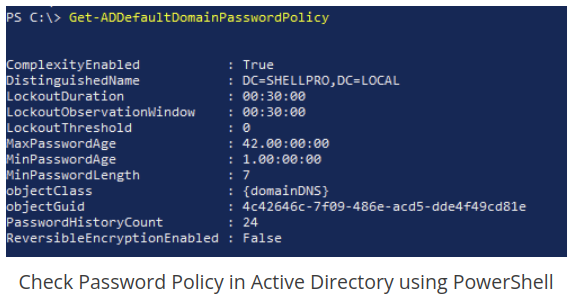
During penetration tests I like to run password spraying attacks after enumerating the lockout policy as noted above and use a tool like “spraycharles” found on GitHub to automate the password spray attack while I work on other testing items that require more manual interactions. One of the input requirements of spraycharles is a password list or single password to test. I normally create a list of passwords to try using common qwerty keyboard walks and spray them throughout the test. If the client Active Directory policy is not following best practices of LockoutDuration and LockoutThreshold settings it possible to exhaust a password spray list quickly so I wanted to create a python script I could use during a test to quickly create qwerty style passwords that use numbers and special characters.
Using ChatGPT to generate some code as a starting point
I have found creating python scripts from scratch to be challenging to know where to begin. For this assignment I wanted to experiment with an AI tool like ChatGPT to generate some code quickly and get started. I also planned to use ChatGPT to help me add features to the code as I came up with ideas on how to add features. Additionally, I wanted to use ChatGPT to help me work through any errors in the code along the way by just copying the error output and pasting it in the next message to ChatGPT.
During this assignment, as with coding a script from scratch it helps to start with a basic request or task for ChatGPT and iterate slowly adding more features once you having working code vice posing a huge task in case you have errors in the ChatGPT output. Starting with a small amount of code will make it easier to figure out the error(s). If you cannot figure out the error you can always send a new message to ChatGPT with the error and ask it to fix the error however, this process has mixed success in my experience.
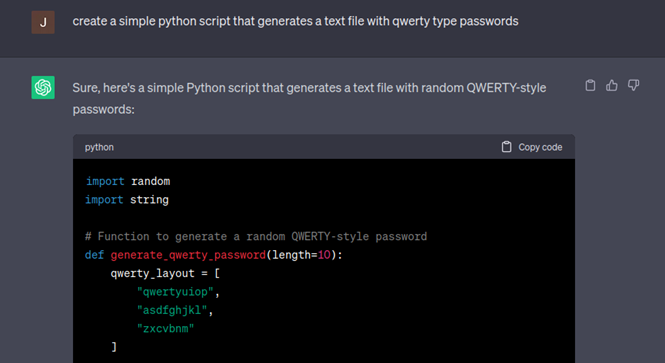
Next I add a prompt for the user to input the desired length of the passwords generated:
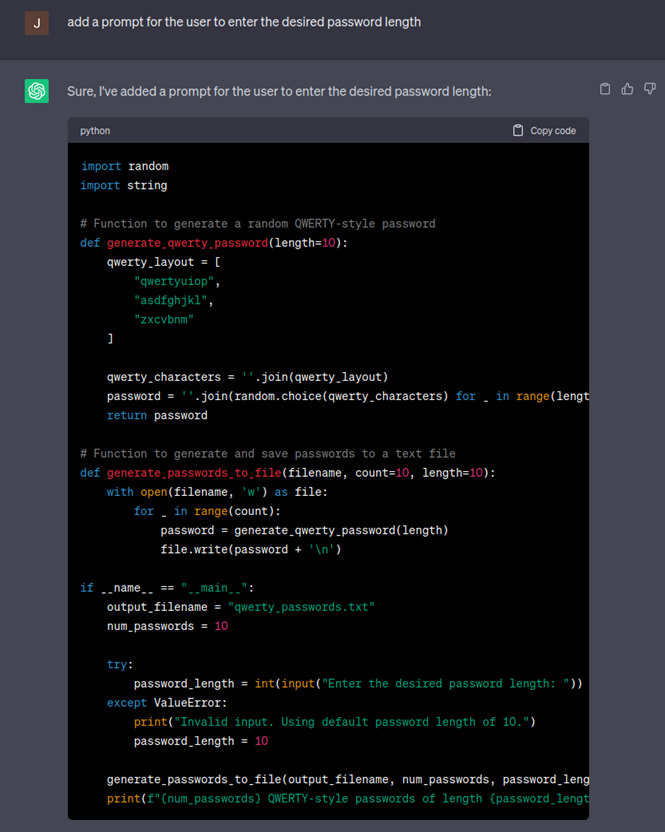
You may have noticed ChatGPT hard coded the amount of passwords generated to 10 so next I will ask ChatGPT to add a prompt to allow the user to decide how many passwords to generate.
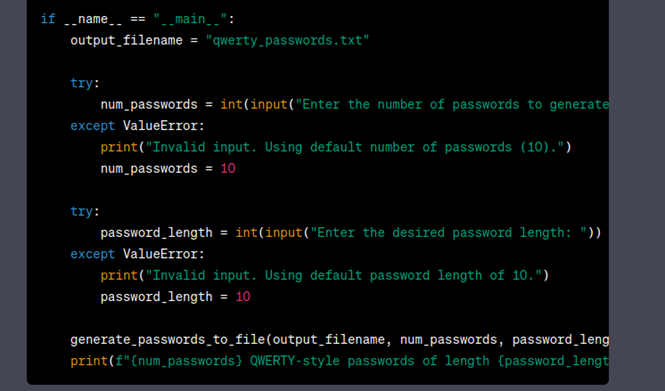
Oops it looks like the ChatGPT generated a random password list and does not follow the qwerty keyboard walk like we hoped so we will try to ask it to fix the script:
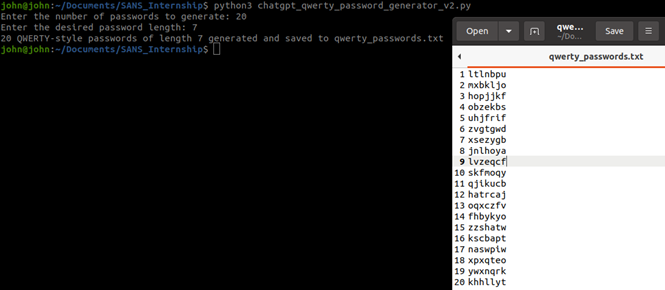
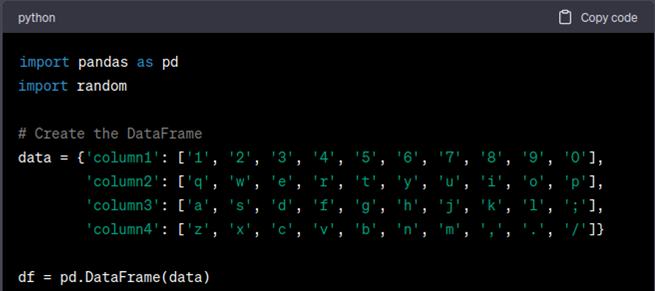
Looking at the code and output, I realized ChatGPT was struggling to accurately reference the keyboard layout in the way I was telling it to generate qwerty style passwords and after numerous iterations to the code, I finally got it to output a simple keyboard walk from the top row of keyboard to the bottom using a Pandas DataFrame format to be able to reference columns and rows.
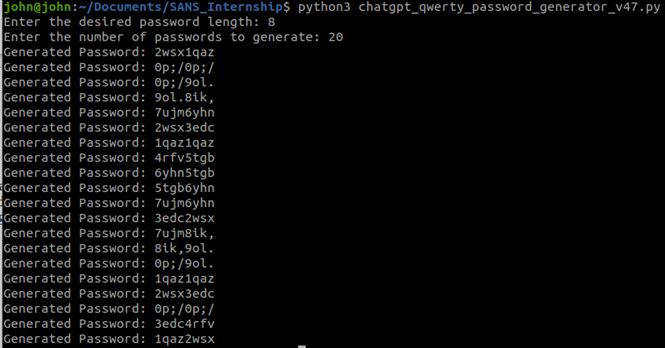
Now using the example Active Directory setting above we created 20 passwords with the length of 8 characters:
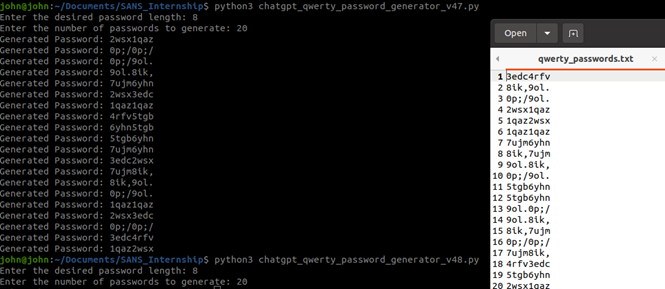
Now that have some working code we can add back in the feature of sending the output to a text file and removing the "Generated Password":
Conclusion
This project showed me that ChatGPT needs clear parameters and sometimes lots of trial and error to create the python code you are trying to create. Also, it is best to start with a simple core function and slowly build complexity, which will make it easier to troubleshoot any errors in the code. This project reminded me of to the “tire swing analogy” except it is was between me and AI, trying to get it to generate code to automate a tedious task of generating qwerty style passwords.
Disclaimer: This project used the free version of ChatGPT so in all fairness the paid version of ChatGPT may cause less errors, more user friendly and reduce the amount of trial and error.
[1] https://github.com/Tw1sm/spraycharles
[2] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
More Exotic Excel Files Dropping AgentTesla
Excel is an excellent target for attackers. The Microsoft Office suite is installed on millions of computers, and people trust these files. If we have the classic xls, xls, xlsm file extensions, Excel supports many others! Just check your local registry:
Attackers like to use more “exotic” extensions to increase chances of evading simple and stupid rules at mail gateways. This time, the extension used was “.xlam”. I spotted several emails (probably from the same campaign) that delivered .xlam files to potential victims.
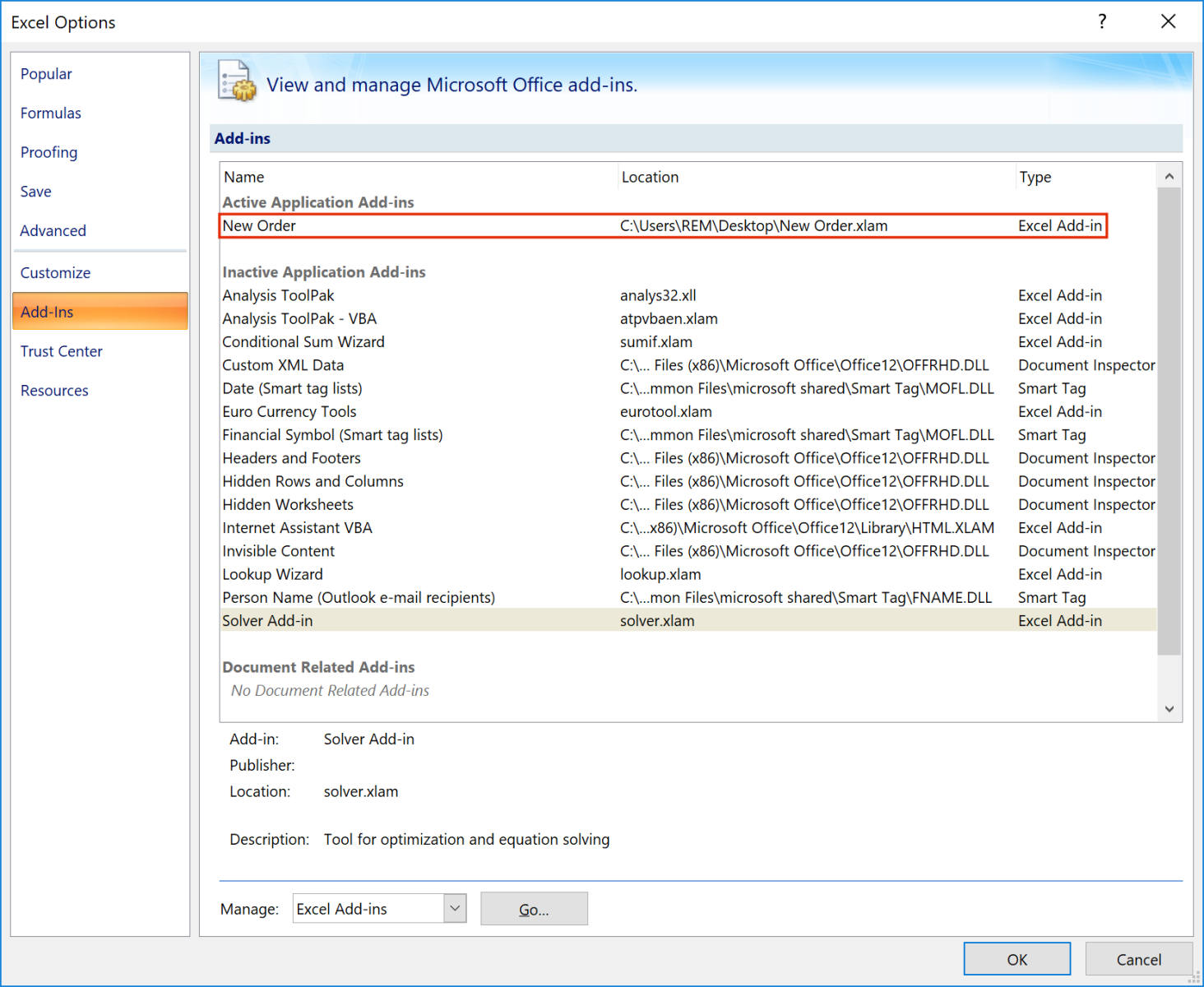
An XLAM file is a macro-enabled add-in used to add new features to Excel. The icon looks like Excel and should make the user confident to open it:

Once loaded, you can see the add-on in Excel:
The add-on has the following SHA256: 72006dfd34f5b043e6763b16ff8399382e69ad356e8c6b9e71ec908674dab55c and a VT score of 30/56[1].
If you read “macro-enabled”, it’s not classic VBA macro, but this add-on contains an exploit for the good old Equation Editor (CVE-:2017-1182). If successfully exploited, the add-on will download a malicious VBS script and execute it:
C:\Windows\System32\WScript.exe" "C:\Users\user01\AppData\Roaming\oldgyyudi.vbs"
The URL from where the script is downloaded is http://80[.]76[.]51[.]248/afk.vbs
The script has the following SHA256: d93c28f9ceeac993f652f976e12eba842716d571370bcdb2dd912965aa6274fb (unknown on VT at this time) and is pretty well obfuscated. Here is an example of a function that reverses a string:
Escola = drRgvLwPScMUPVCgWhShgMSmjRqaWCUXzUCPCcDqXCNWRLWXvdWLpQmrjqdvCWZzRcUiWUrawWCsywwLLVsoBPeWDkNtPrWMEMEPZlGYBLWZMhMmMMZVWgeCwhgXq
Escola = eKRiX(eKRiX(eKRiX(Escola)))
[...]
Function eKRiX(iNcPxLbcdBdHlsOAcdpbduplKWscQhRhriWZpuxAGtjteLbDKxgbQjArhOoIuccrMKcNHRiJWiuBxLOUbKyUuLcboDKKbzuhLJCTwrTtcOspGRMunLiIoOogKuiencc)
qArcGzUDayYkTOOcTWLZccaLRrsnUkODDkkHOcpTDMaUNzsXrXTnHUTYLCqrOfyGNJkRLUQnMLOQNWUnKOGkMWUTNJYZLiUZfNzHyccKMKwINzNLYNINsrKBWzsDi =
Chr(83)&Chr(116)&Chr(114)&Chr(82)&Chr(101)&Chr(118)&Chr(101)&Chr(114)&Chr(115)&Chr(101)
nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr =
"eKRiX = "
nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr = nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr +
qArcGzUDayYkTOOcTWLZccaLRrsnUkODDkkHOcpTDMaUNzsXrXTnHUTYLCqrOfyGNJkRLUQnMLOQNWUnKOGkMWUTNJYZLiUZfNzHyccKMKwINzNLYNINsrKBWzsDi
nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr = nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr + "(iNcPxLbcdBdHlsOAcdpbduplKWscQhRhriWZpuxAGtjteLbDKxgbQjArhOoIuccrMKcNHRiJWiuBxLOUbKyUuLcboDKKbzuhLJCTwrTtcOspGRMunLiIoOogKuiencc)"
execute(nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr)
End Function
The variable Escola will contain the string "Startup".
The next payload is downloaded from http://80[.]76[.]515.]248/afrique.txt, which returns a Base64-encoded string (reversed) that is decoded as a PE file (SHA256: e45d91008eb19ecc3c9e6aab13339bc327c2c61b97215b0d2cc98c23b0db057a). This is an AgenTesla with the following config:
{
"rule": "AgentTeslaV4",
"family": "agenttesla",
"credentials": [
{
"host": "mail.worlorderbillions.top",
"port": 587,
"email_to": "absach@worlorderbillions[.]top",
"password": “xxxxxxxxxxxxxxxxx”,
"protocol": "smtp",
"username": "absach@worlorderbillions[.]top"
}
]
}
[1] https://www.virustotal.com/gui/file/72006dfd34f5b043e6763b16ff8399382e69ad356e8c6b9e71ec908674dab55c
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments