Show me All Your Windows!
It's a key point for attackers to implement anti-debugging and anti-analysis techniques. Anti-debugging means the malware will try to detect if it's being debugged (executed in a debugger or its execution is slower than expected). Anti-analysis refers to techniques to detect if the malware is detonated in a sandbox or by a malware analyst. In such cases, tools run in parallel with the malware to collect live data (packets, API calls, files, or registry activity).
The Microsoft API set is fantastic because it contains many helpful API calls for attackers. Today I found a malicious Python script that (ab)uses one of them: GetWindowText()[1]. This API call is very powerful when used in combination with EnumWindows()[2]. EnumWindows() will list all top-level windows opened on the screen and pass the handle to each window to a callback function that will check the window title via GetWindowText().
That's what has been implemented in the Python script:
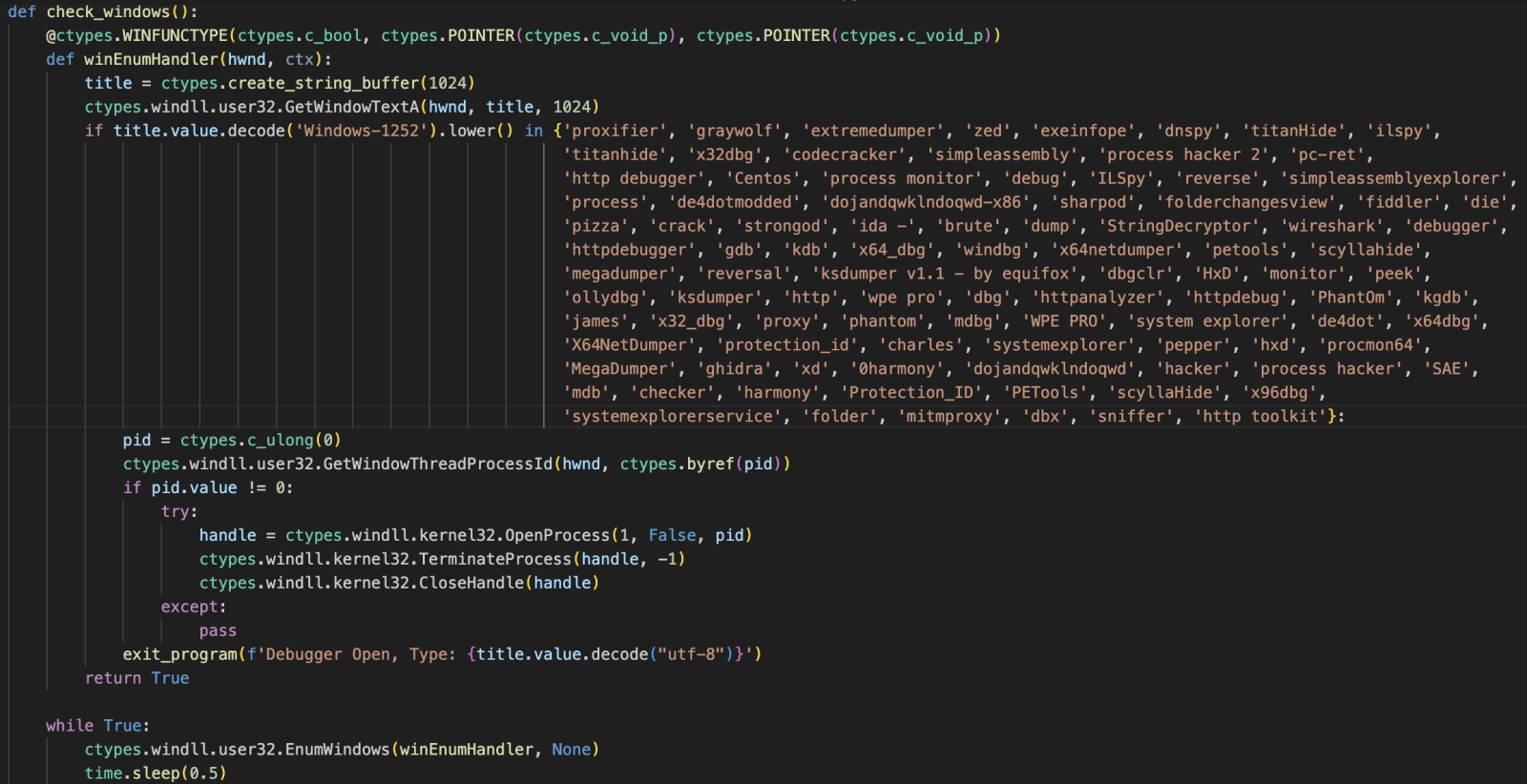
The script used the ctype library to use Windows API calls. EnumWindows() is called in a loop; for each window found, the callback function winEnumHandler() is called. The window title is extracted and compared to a nice list of well-known tools used by malware analysts.
The malware will not silently exit if a suspicious window is found. Instead, it will link the process to the window and try to kill it using GetWindowThreatProcessId()[3]!
Another good example of API calls group that reveals a specific technique used by attackers! The script (SHA256:c8a5262e89751f231060a6740447062e34c5393a17f67d0c4eb52c7f911f3bd2) has a VT score of 6/60[4].
[1] https://learn.microsoft.com/en-us/windows/win32/api/winuser/nf-winuser-getwindowtexta
[2] https://learn.microsoft.com/en-us/windows/win32/api/winuser/nf-winuser-enumwindows
[3] https://learn.microsoft.com/en-us/windows/win32/api/winuser/nf-winuser-getwindowthreadprocessid
[4] https://www.virustotal.com/gui/file/c8a5262e89751f231060a6740447062e34c5393a17f67d0c4eb52c7f911f3bd2
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments