Analysis of a Malicious HTML File (QBot)
Reader Eric submitted a malicious HTML page that contains BASE64 images with malware.
Let's take a look. With my tool base64dump.py I search for long BASE64 strings inside the HTML code:
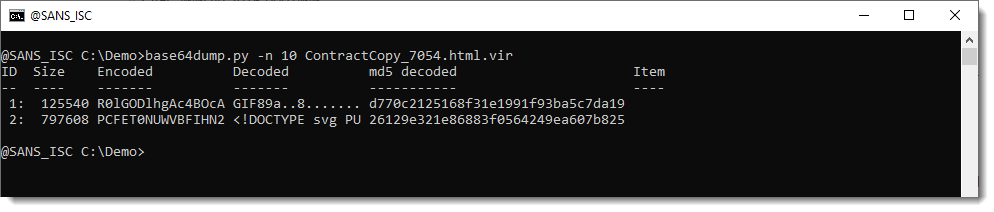
Looks like there are indeed 2 images. A GIF and a SVG file.
Let's take a closer look:
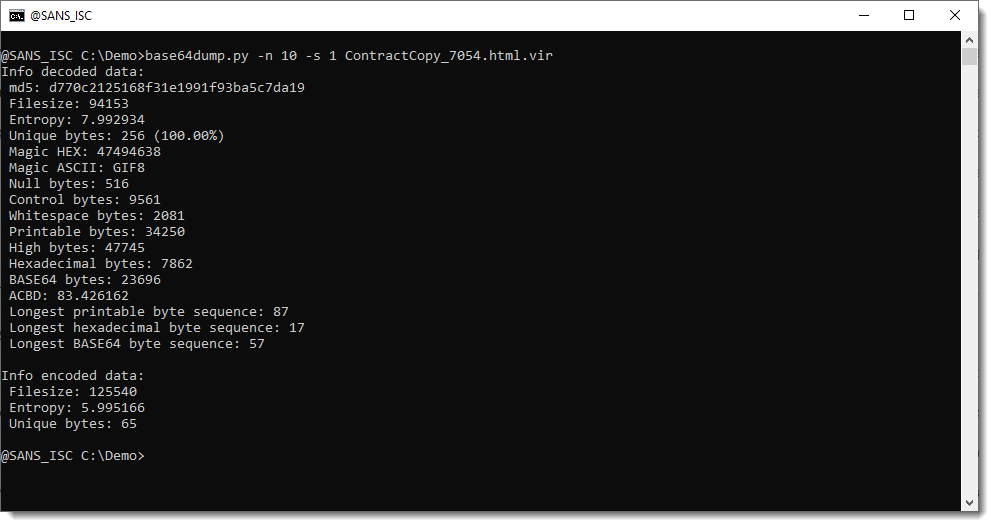
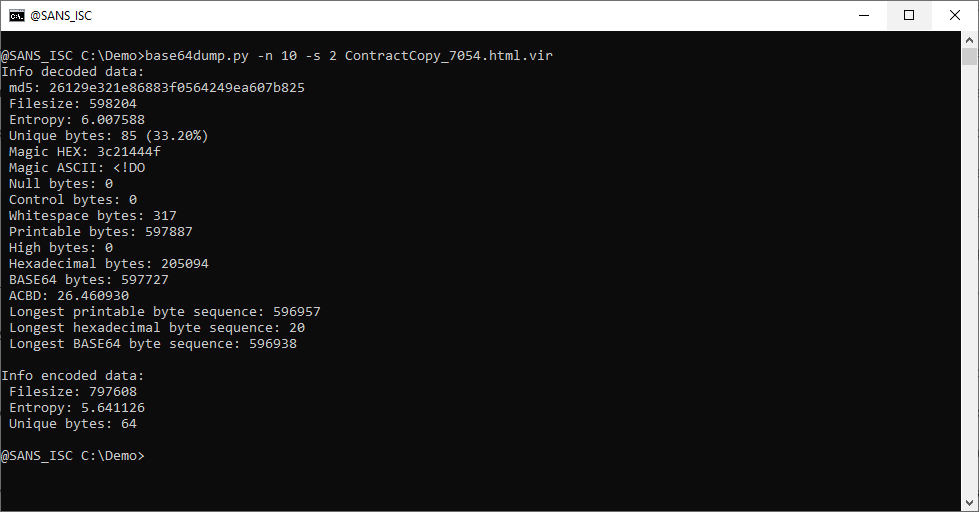
The GIF file has very high entropy, and no long strings. While the SVG file contains a byte sequence of BASE64 digits that's 596938 bytes long.
So it's very likely that something is hidden in the SVG file.
Let's try a second level of base64 decoding:
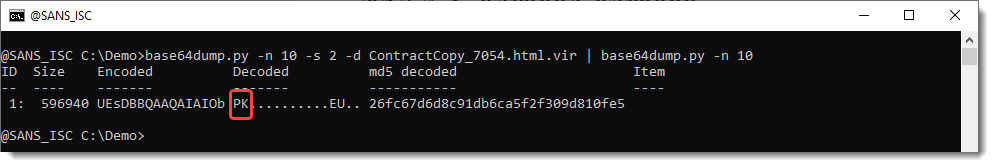
PK: that's probably a ZIP file. Let's try with zipdump.py:
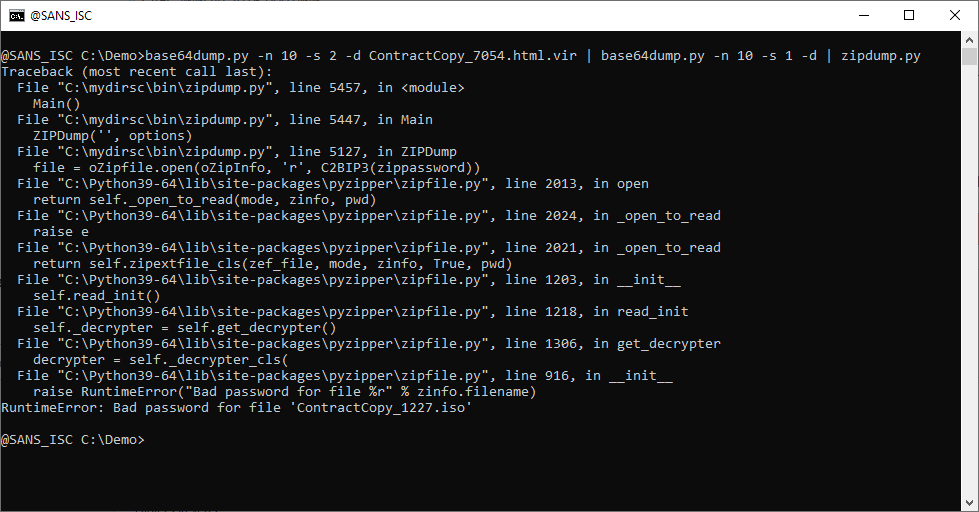
It's indeed a ZIP file, but it is password protected. Let's grep for the password in the HTML file:
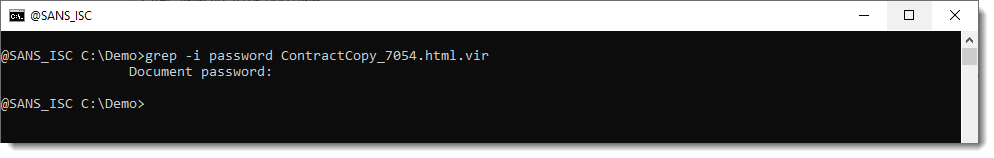
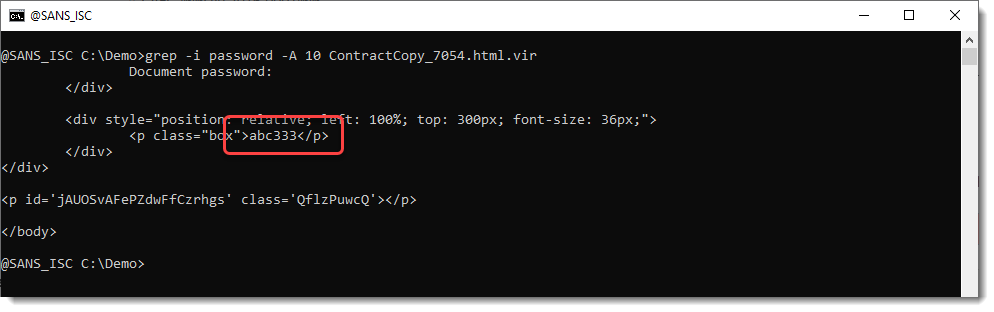
Looks like abc333 is the password. Let's try:
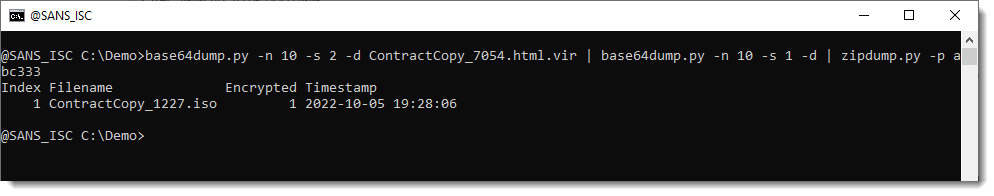
The ZIP file contains an ISO file.
Let's take a look with isodump.py:
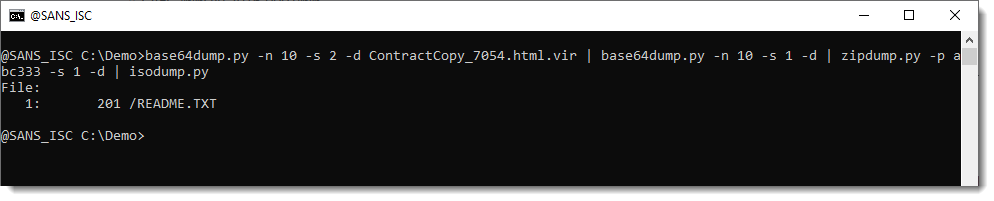
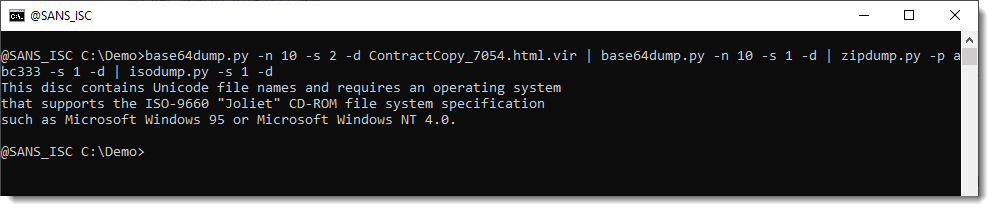
isodump.py only sees one text file. That's very unlickely that a malicious document (it's clear that this is malicious, by now) just contains a text file. What is going on, is that there's a seconday volume decriptor, but the pathlab module that isodump uses, is not capable of recognizing that secondary volume.
As I now expect a Windows executable inside that ISO file, I use pecheck.py to carve out PE files:
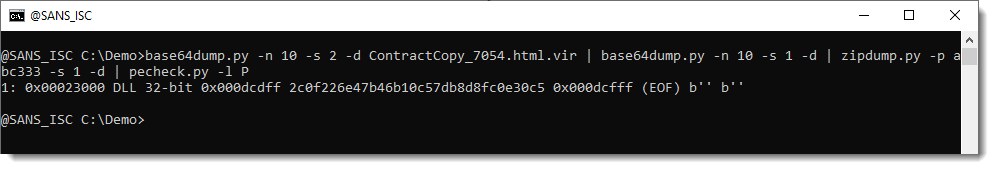
And indeed, we have a 32-bit DLL, that turns out to be QBot.
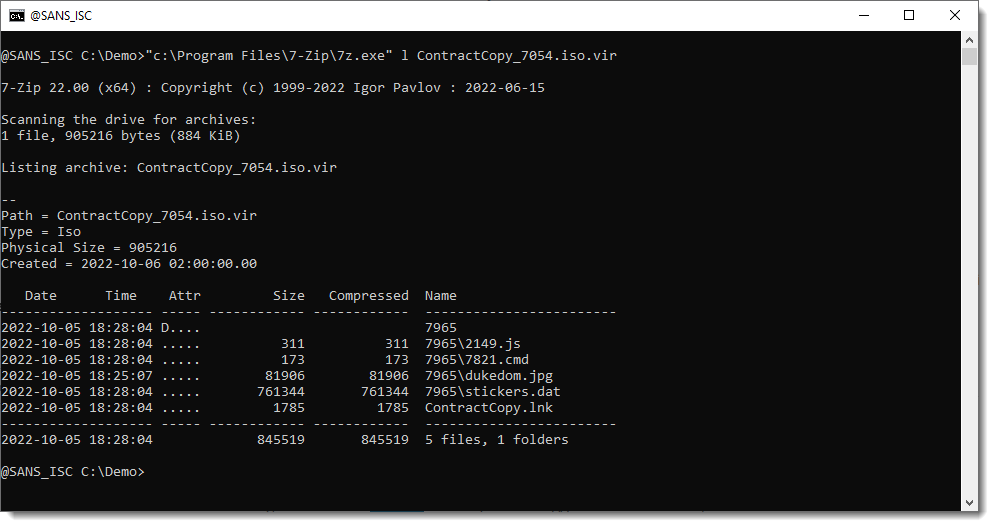
The 7-zip utility can help us look inside ISO files, but it does not accept an ISO file as input via stdin.
So I first must write the file to disk, and then have 7-zip analyze it:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments