HTTP/2 Packet Analysis with Wireshark
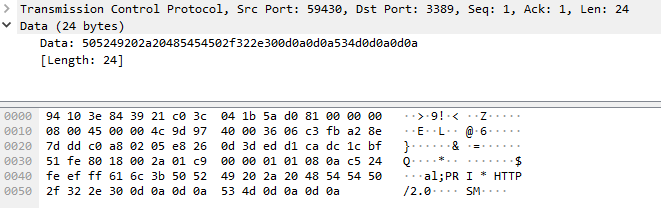
I have been getting these queries in my honeypot logs since end of December 2021 and decided to a diary on some of these packets using some basic analysis with Wireshark. Handlers have published a few diaries over the years [1][2][3] regarding this protocol. These packets are from censys.io[4] which is a site that provides internet discovery and inventory like Shodan. In my logs, the activity looked like this:
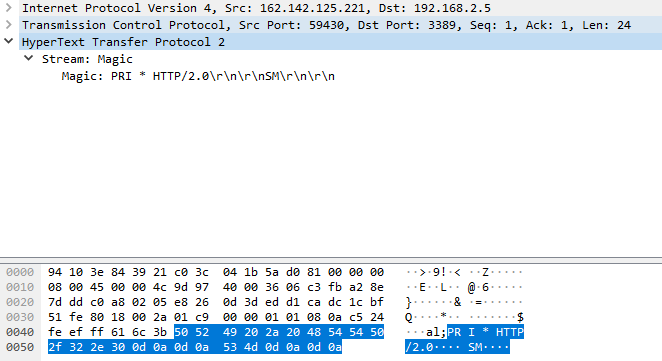
20220822-014547: 192.168.25.9:3389-162.142.125.221:59430 data
PRI * HTTP/2.0
SM
\x00\x00\x18\x04\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x00\x00\x04\x00\x00Bh\x00\x06\x00\x04\x00\x00\x00\x03\x00\x00\x00
Before I update my Wireshark filter, select HTTP2 and add port TCP/3389, the data looked like some kind of HTTP traffic. The payload appears to indicate it is HTTP/2.0 and the protocol need to be updated with port TCP/3389 in order to parse the packet properly.
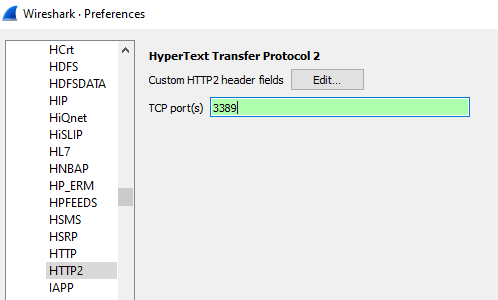
Lets update the configuration preferences to view the activity as HTTP/2. To change the preferences select Edit, Preferences, Protocols, HTTP2 and add port 3389 and apply the change:
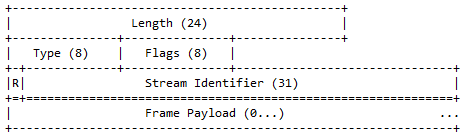
According to RFC 7540, "All frames begin with a fixed 9-octet header followed by a variable- length payload."[6]
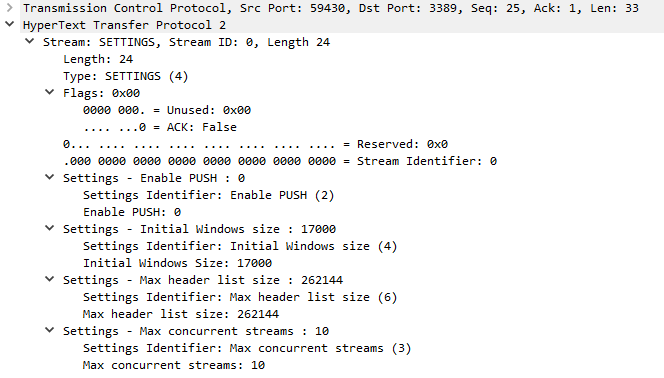
After applying the http2 change to Wireshark, we can now see HTTP2 header corretly decoded as per RFC7540:
This last picture shows the HTTP2 payload decoded as per RFC 7540 above picture with a Stream length of 24 and its 31 bits (all 0) identifier:
[1] https://isc.sans.edu/diary/Explicit+Trusted+Proxy+in+HTTP2.0+or...not+so+much/17708
[2] https://isc.sans.edu/diary/RFC+7540+-+HTTP2+protocol/19799
[3] https://isc.sans.edu/diary/Apache+Update%3A+TLS+Certificate+Authentication+Bypass+with+HTTP2+%28CVE-2016-4979%29/21223
[4] https://isc.sans.edu/diary/An+Alternative+to+Shodan%2C+Censys+with+User-Agent+CensysInspect1.1/26718
[5] https://isc.sans.edu/ipinfo.html?ip=162.142.125.221
[6] https://www.rfc-editor.org/rfc/rfc7540.html
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
Paypal Phishing/Coinbase in One Image
There is a current wave of Paypal phishing emails ongoing. I already received a few of them. This time, the spam is based on a simple JPEG image. The subject has always this format (with the date changing):
Your PayPal Order Receipt from Aug 25, 2022
The mail body contains the following image:
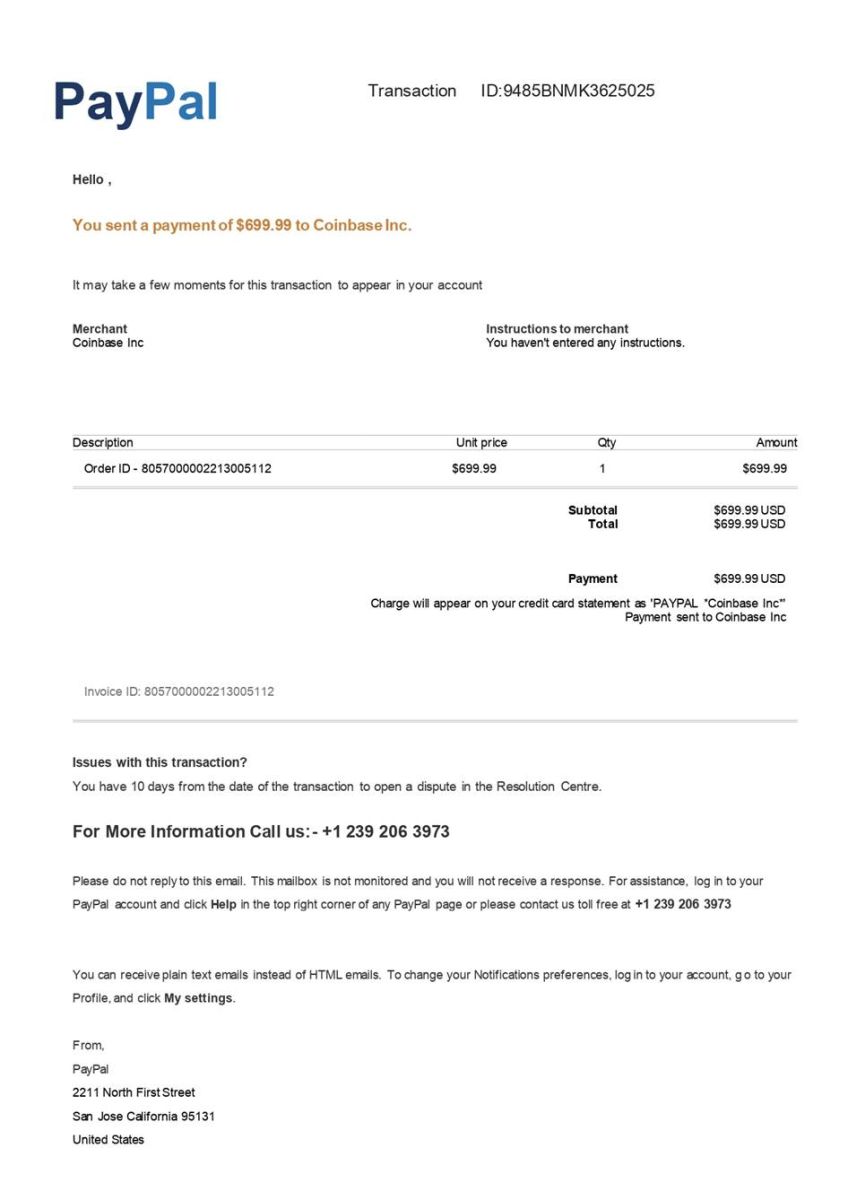
As you can read, they mention no mail e-mail them but there is phone number. This number was always the same across the samples I received. When you have a phone number, you call it! So I tried...
I called multiple times, at different hours (I'm based in the CET timezone so I tried to call in the morning, afternoon and evening) but no luck! Nobody picked up the phone. It keeps ringing forever... Some people already reported this number is suspicious[1][2]. If you prepare a phishing attack you expect that victims will call! I'm disappointed by the lack of reactivity! Maybe they filter incoming calls based on the international code? (In my case, I called from a Belgian SIP line, international code +32)
[1] https://whocallsme.com/Phone-Number.aspx/2392063973
[2] https://spamcalls.net/en/number/12392063973
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments