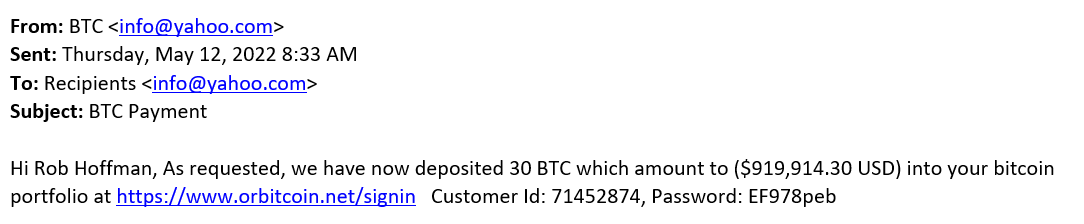
Do you want 30 BTC? Nothing is easier (or cheaper) in this phishing campaign...
Cryptocurrency scams have become ubiquitous over the past few years, but from time to time, one still comes over an interesting or unusual one. And the one that recently made its way to us at the ISC certainly was interesting, as it was much more sophisticated than usual... Though, as you may see, one would not have guessed it from the less than believable initial e-mail message.
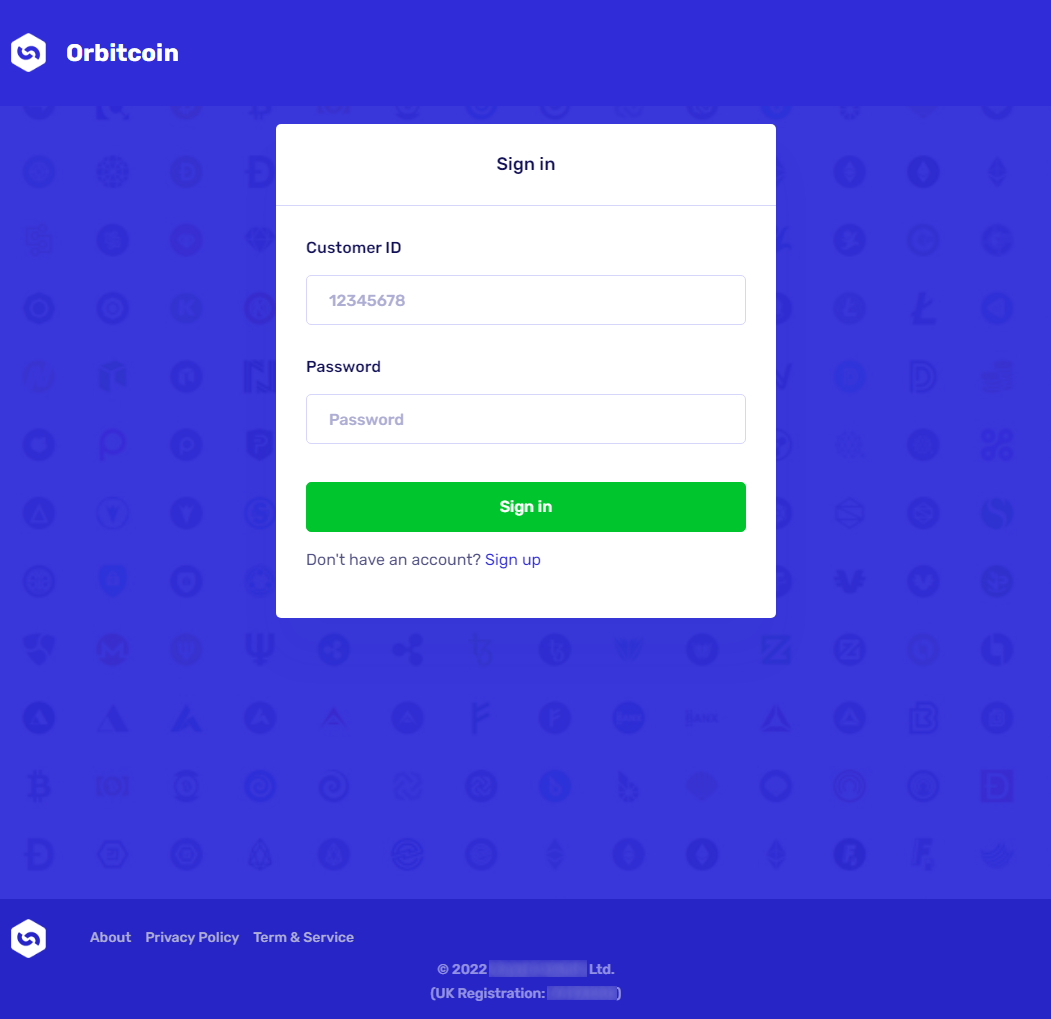
If a victim were to open the link, they would be greeted with a login screen where the provided credentials could be entered. That is, if the victim decided that getting their hands on 30 BTC belonging to someone named Rob Hoffman would be worth it to cross the proverbial ethical line.
This was a “nice touch” on the part of the scammers, as even if the victim did send them money, they would hardly go to the police afterwards and start the conversation with “Well, I accessed the account of this guy called Rob, whom I don’t know, and I wanted to get my hands on his 30 BTC…”, but we’ll get to the specifics of the scam later.
If the correct credentials from the phishing message were provided, the victim would be redirected to a page simulating a cryptocurrency investment platform, and indicating in the upper right corner that the account truly holds 30 BTC. It would, however, require that a 2FA using SMS or an automated call be set up and the password be changed, before any other actions would be allowed. After this was done, the victim would finally be directed to a page where they would be able to transfer the money… Or, so it would have seemed.
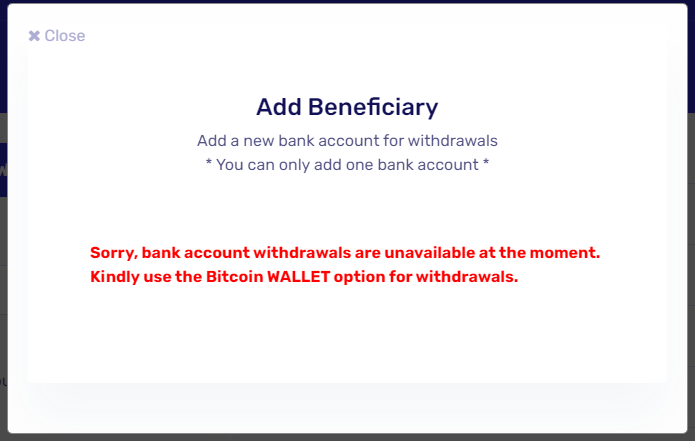
If they did try to initiate a transfer to a bank account, they would be greeted by a message claiming that bank account withdrawals were currently unavailable…
And if they tried to initiate a transfer to a “Bitcoin wallet”, they would be informed that the first transfer has to be no more than 0.0001 BTC for security reasons.
“So where is the scam?”, you might ask.
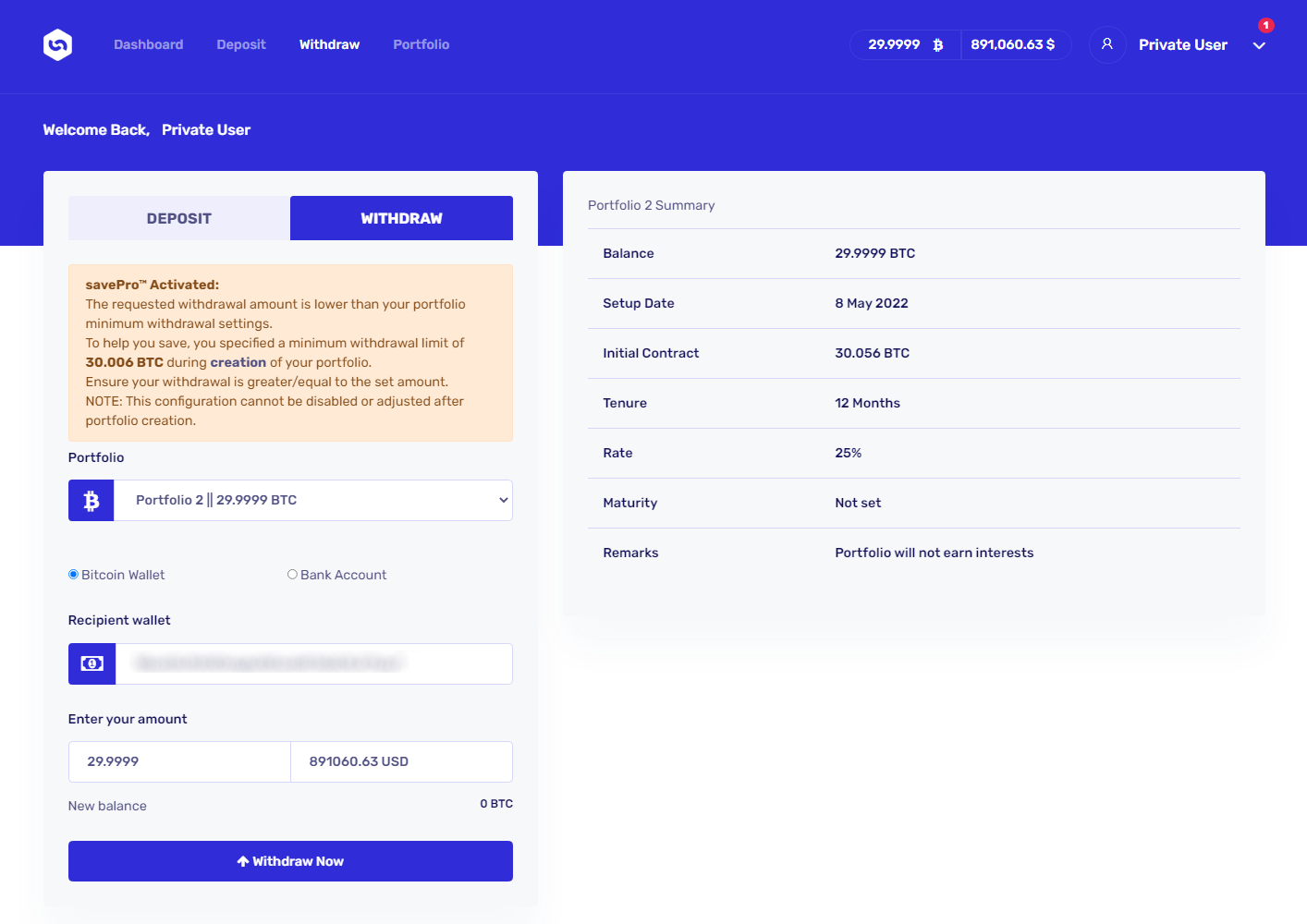
Well, once this initial 0.0001 BTC transfer was seemingly done (in reality, no money would be transferred, of course) and the victim tried to “withdraw” the remaining balance, they would be greeted with a message informing them that the minimum amount for withdrawal, which was supposedly set by the account owner when the account was created, is 30.006 BTC…
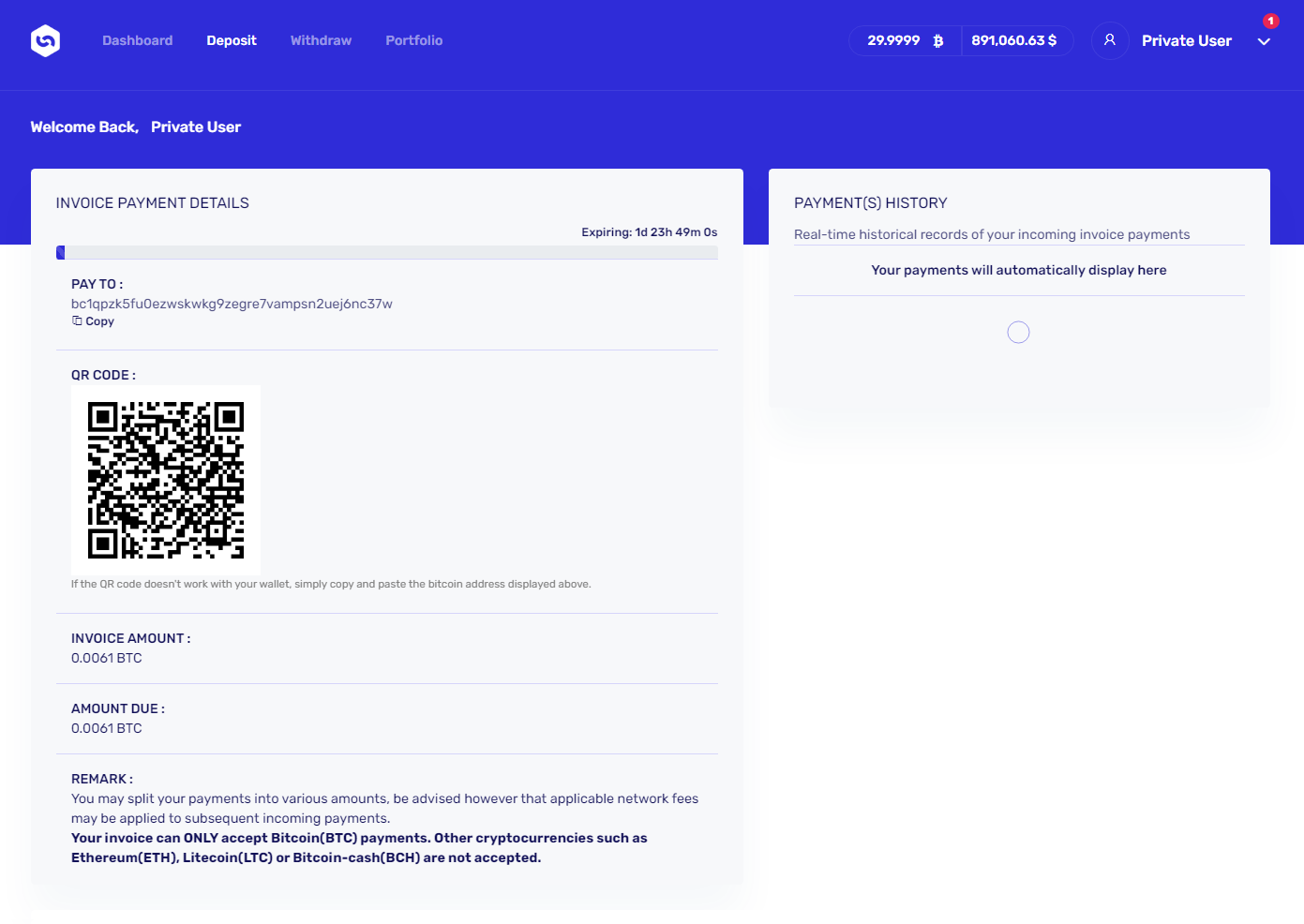
This means that the victim would have to transfer at least 0.0061 BTC to the platform in order to get to this minimum amount. Although this isn’t that much (little less than $200 at the time of writing), it would certainly be a worthwhile payout for the scammers, especially when one considers that there might be multiple victims willing to transfer this amount… Which, given that there is seemingly an opportunity to get 30 BTC (almost $895k at the time of writing), there might well be.
Luckily, it seems that so far, the scammers have not been successful, at least not with the “deposit” Bitcoin address (bc1qpzk5fu0ezwskwkg9zegre7vampsn2uej6nc37w) that was displayed for “Rob’s” account, as it was still empty at the time of writing.
It appears that at least two versions of the scam messages with different amounts and credentials were sent out – the one “offering” 30 BTC and another one mentioning 20 BTC[1]. And although it is certainly possible that the scammers used different BTC address for the second one, the fact that this one was still empty is certainly positive.
It should be mentioned that although the scam as a whole was quite well thought out, and the website was/is certainly among the more sophisticated phishing pages out there, it seems that the scammers either didn’t care enough to “personalize” the user accounts or they decided to reuse the same credentials for multiple phishing messages that contained different names of account holders, which prevented them from personalizing the user accounts. Whatever the reason, as you may see in the last two images of the platform, although account was supposed to belong to the aforementioned Rob Hoffman, rather than his name, the page showed the name “Private User” (yes, that was supposed to be a “full name” of the user and it could have been changed in the settings… and although it doesn’t matter much on a phishing site, in order to end on a positive note, it is worth mentioning that the input wasn’t filtered or encoded to prevent XSS, so we can see that even in sophisticated scams, the scammers don’t necessarily care much about the quality and security of their code).
IoCs
hxxps://www[.]orbitcoin[.]net/
bc1qpzk5fu0ezwskwkg9zegre7vampsn2uej6nc37w
[1] https://scammer.info/t/bitcoin-deposit/97475
-----------
Jan Kopriva
@jk0pr
Nettles Consulting



Comments