Microsoft Word document with malicious macro pushes IcedID (Bokbot)
Introduction
Every so often, I run across a sample of IcedID, also known as Bokbot. The infection characteristics have changed a little since my previous diary about IcedID. An in-depth write-up has already been published by IBM Security Intelligence about recent changes in IcedID this year, so today's diary is a quick review from a recent infection in my lab on Tuesday 2020-05-19.
The chain of events for this infection:
- Microsoft Office document, either a Word document or Excel spreadsheet, likely sent through malspam
- Open document and enable macros
- Word doc drops and runs initial EXE
- HTTPS traffic to non-malicious URLs
- HTTPS traffic to .xyz domain
- PNG file with encoded data used to create follow-up IcedID EXE
- Follow-up IcedID EXE made persistent through scheduled task
- HTTPS post-infection traffic caused by IcedID (.club and .top TLDs)
The Word document
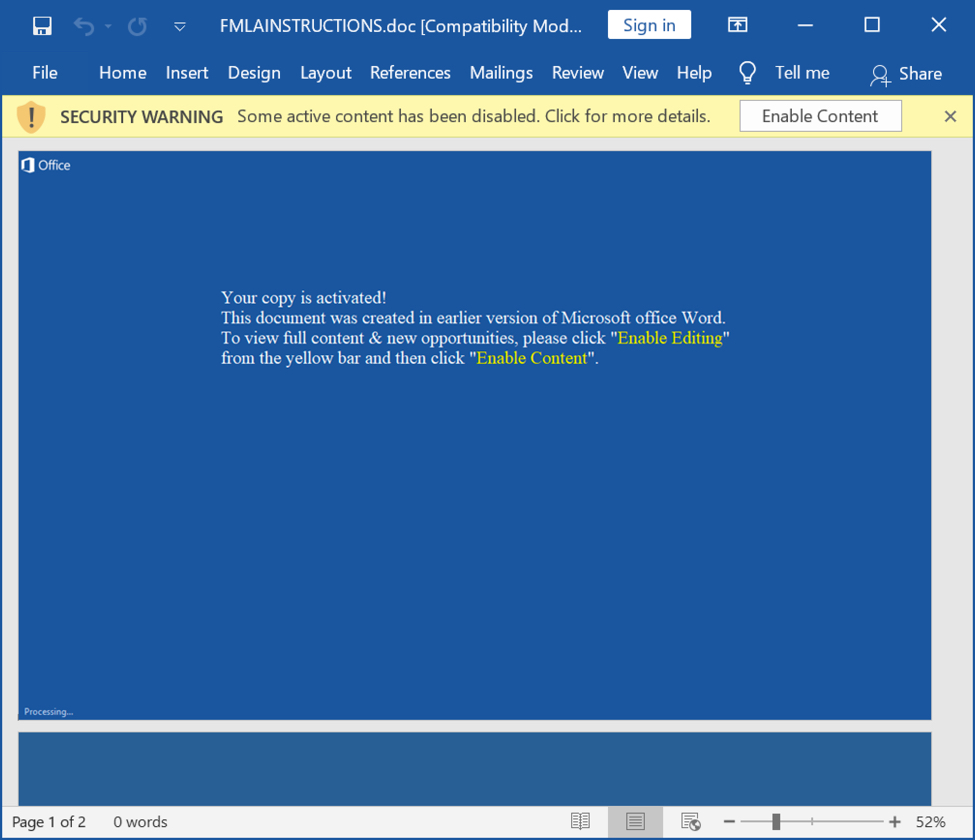
Shown above: Screenshot of a Word document with malicious macros for IcedID.
Artifacts from an infected Windows host
The following are screenshots from reviewing artifacts from an infected Windows host in my lab.
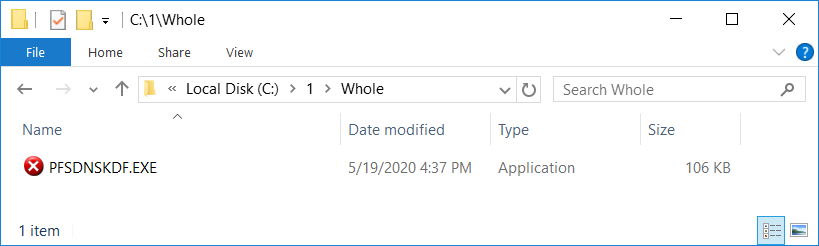
Shown above: The initial EXE dropped after enabling macros on the Word document.
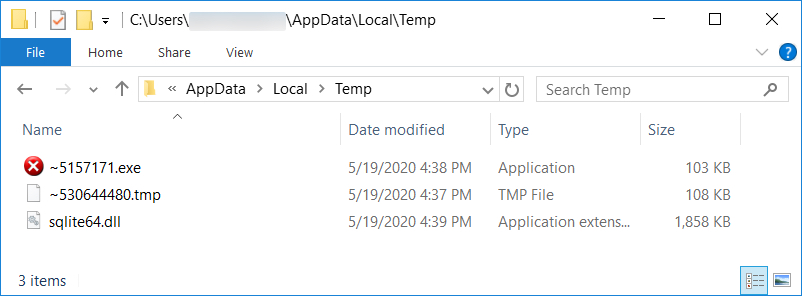
Shown above: Additional artifacts after the initial EXE was dropped. This includes the follow-up EXE for IcedID.
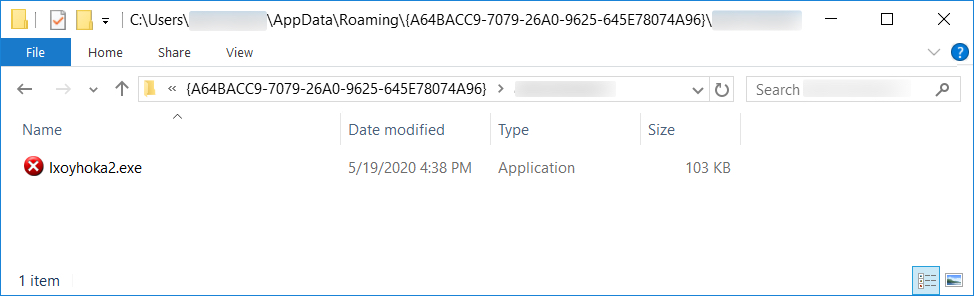
Shown above: The follow-up EXE for IcedID persistent on an infected Windows host.
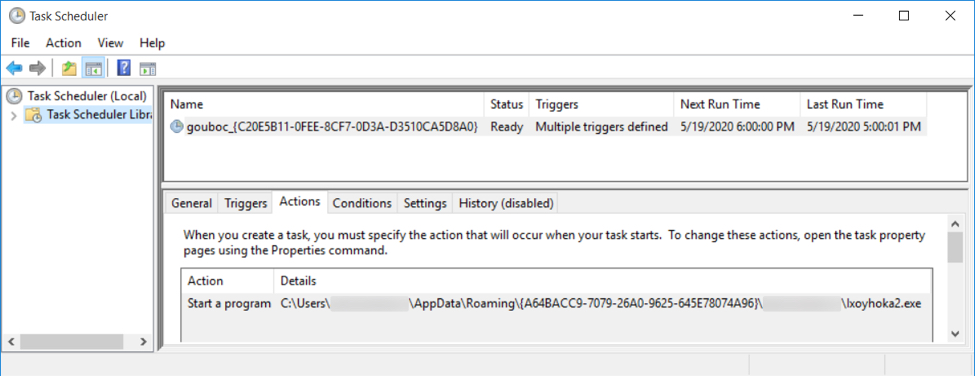
Shown above: Scheduled task to keep the IcedID infection persistent.
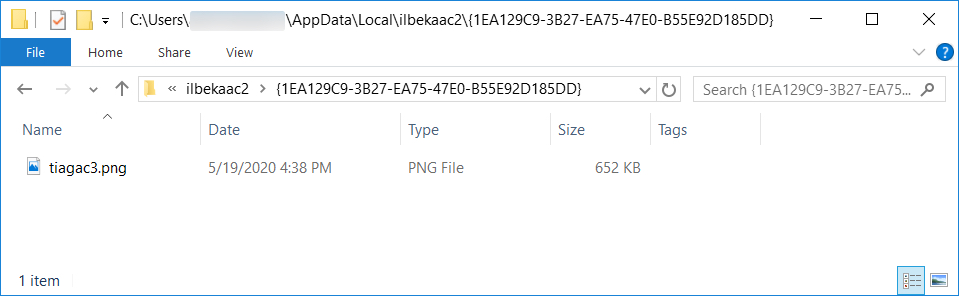
Shown above: Another artifact created after the IcedID infection became persistent.
Infection traffic
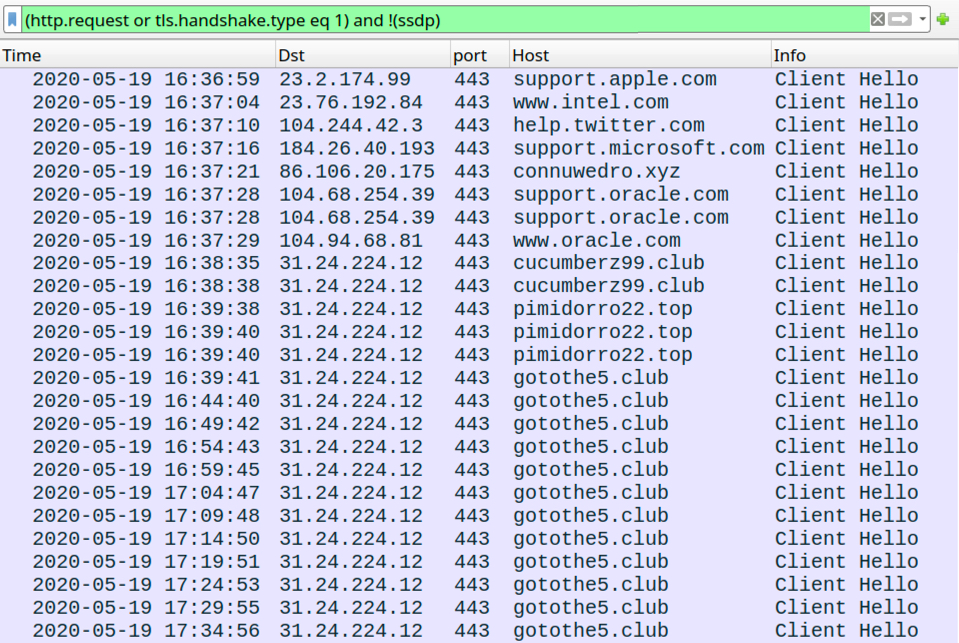
Shown above: Traffic from the infection filtered in Wireshark.
Indicators of Compromise (IoCs)
Non-malicious traffic caused by the initial IcedID binary during this infection:
- port 443 - support.apple.com - HTTPS traffic
- port 443 - www.intel.com - HTTPS traffic
- port 443 - help.twitter.com - HTTPS traffic
- port 443 - support.microsoft.com - HTTPS traffic
- port 443 - support.oracle.com - HTTPS traffic
- port 443 - www.oracle.com - HTTPS traffic
Malicious traffic during this IcedID infection:
- 86.106.20[.]175 port 443 - connuwedro[.]xyz - HTTPS traffic
- 31.24.224[.]12 port 443 - cucumberz99[.]club - HTTPS traffic
- 31.24.224[.]12 port 443 - pimidorro22[.]top - HTTPS traffic
- 31.24.224[.]12 port 443 - gotothe5[.]club - HTTPS traffic
Files recovered from an infected Windows host:
SHA256 hash: 822a8e3dfa14cd7aaac749dc0515c35cf20632717e191568ba5daf137db7ec17
- File size: 127,278 bytes
- File name: FMLAINSTRUCTIONS.doc
- File description: Word doc (DOCX file) with macro for IcedID (Bokbot)
SHA256 hash: ee9fd78107cdcaffc274cf2484d6c74c56c7f3be39b1896894d9525506118d1e
- File size: 108,032 bytes
- File location: C:\1\Whole\PFSDNSKDF.EXE
- File description: Initial EXE for IcedID infection dropped after enabling Word macros
SHA256 hash: d40566808aead4fecec53813d38df4fbe26958281a529baf5b6689f0163d613f
- File size: 109,895 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\~530644480.tmp
- File type: PNG image data, 525 x 539, 8-bit/color RGB, non-interlaced
- File description: PNG image containing encoded data for follow-up IcedID executable
SHA256 hash: c35dd2a034376c5f0f22f0e708dc773af8ee5baf83e2a4749f6f9d374338cd8e
- File size: 105,472 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\~5157171.exe
- File location: C:\Users\[username]\AppData\Roaming\{A64BACC9-7079-26A0-9625-645E78074A96}\[username]\Ixoyhoka2.exe
- File description: IcedID executable extracted from the above PNG and made persistent on the infected Windows host
SHA256 hash: 45520a22cdf580f091ae46c45be318c3bb4d3e41d161ba8326a2e29f30c025d4
- File size: 667,077 bytes
- File location: C:\Users\[username]\AppData\Local\ilbekaac2\{1EA129C9-3B27-EA75-47E0-B55E92D185DD}\tiagac3.png
- File description: Artifact dropped during IcedID infection, probably contains encoded data
- File type: PNG image data, 643 x 283, 8-bit/color RGB, non-interlaced
Final words
Word documents pushing IcedID reliably generate infections on vulnerable hosts in my lab environment. However, Windows 10 computers that are fully patched, up-to-date, and following best security practices are not likely to get infected.
Email examples, malware samples, and a pcap from an infected Windows host used in today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments