Agent Tesla delivered by the same phishing campaign for over a year
While going over malicious e-mails caught by our company gateway in March, I noticed that several of those, that carried ACE file attachments, appeared to be from the same sender. That would not be that unusual, but and after going through the historical logs, I found that e-mails from the same address with similar attachments were blocked by the gateway as early as March 2019.
The e-mails in question all appeared to come from the address diamond@tnt.com. The sender address was quite interesting in its own way, since, although the messages most certainly didn’t come from TNT, they didn't fail the SPF checks either. The reason for them not being stopped by the Sender Policy Framework checks was not a lack of an SPF record for the domain tnt.com, but the fact that the record in question was set incorrectly, in such a way that it allowed any server to send email for the domain tnt.com.
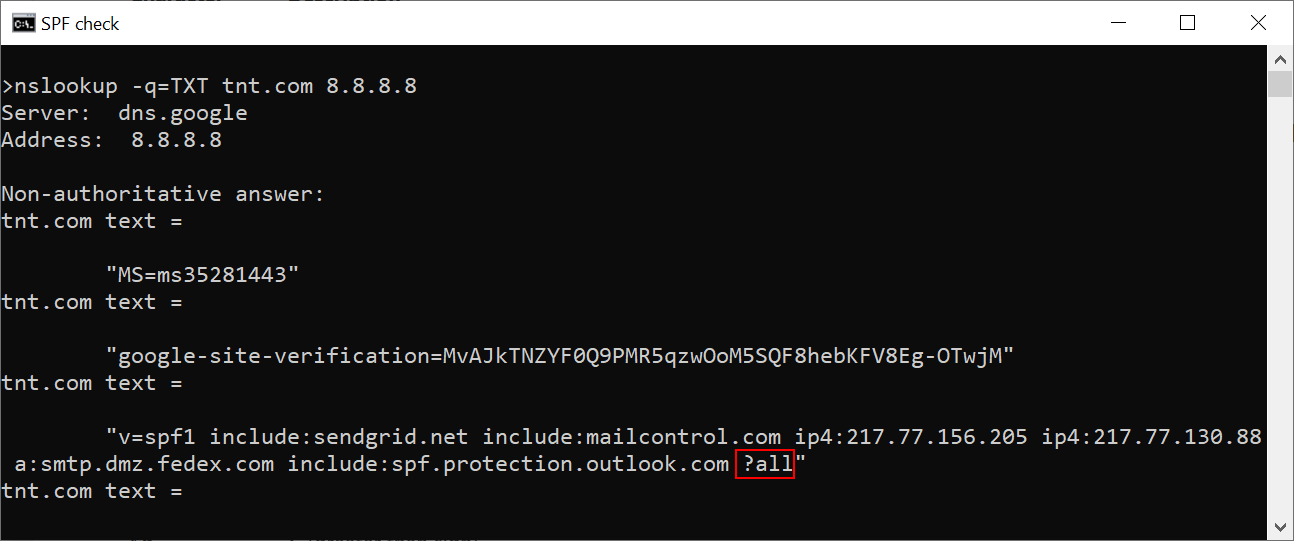
As you may see, the record ends in “?all” – this means that the record doesn’t specify whether any IP address, which is not listed, may or may not send messages for tnt.com[1]. I have informed TNT of both the problem with the SPF record (which they said they will fix soon) as well as the fact that their domain was misused in this was to send malicious messages.
I originally didn't plan to dig any deeper into it, however after our e-mail gateway caught another e-mail from diamond@tnt.com just yesterday, I decided to take a closer look at these messages and their attachments.
After a while of going through my e-mail quarantine backups, I managed to find 54 e-mails from the last 6 months that appeared to have originated from the same address, all of them with an ACE attachment. The messages were fairly similar to each other – most were variations on the theme of “tomorrow we will deliver your package please find the attached invoice”. You may see that there hasn’t been much of a change in them during the past 6 months from the following two examples – the first one is from August 2019 and the second one was "caught" just yesterday.
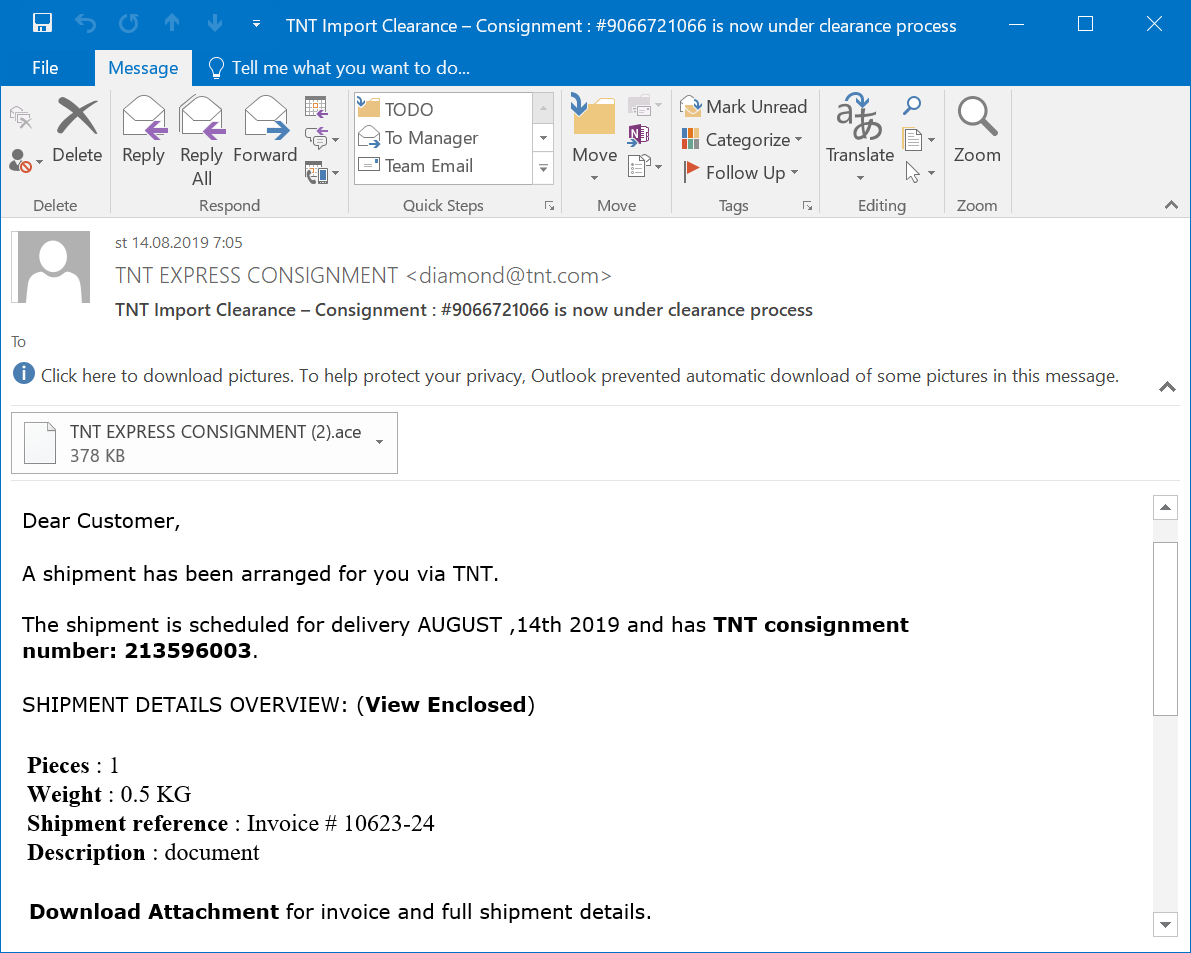
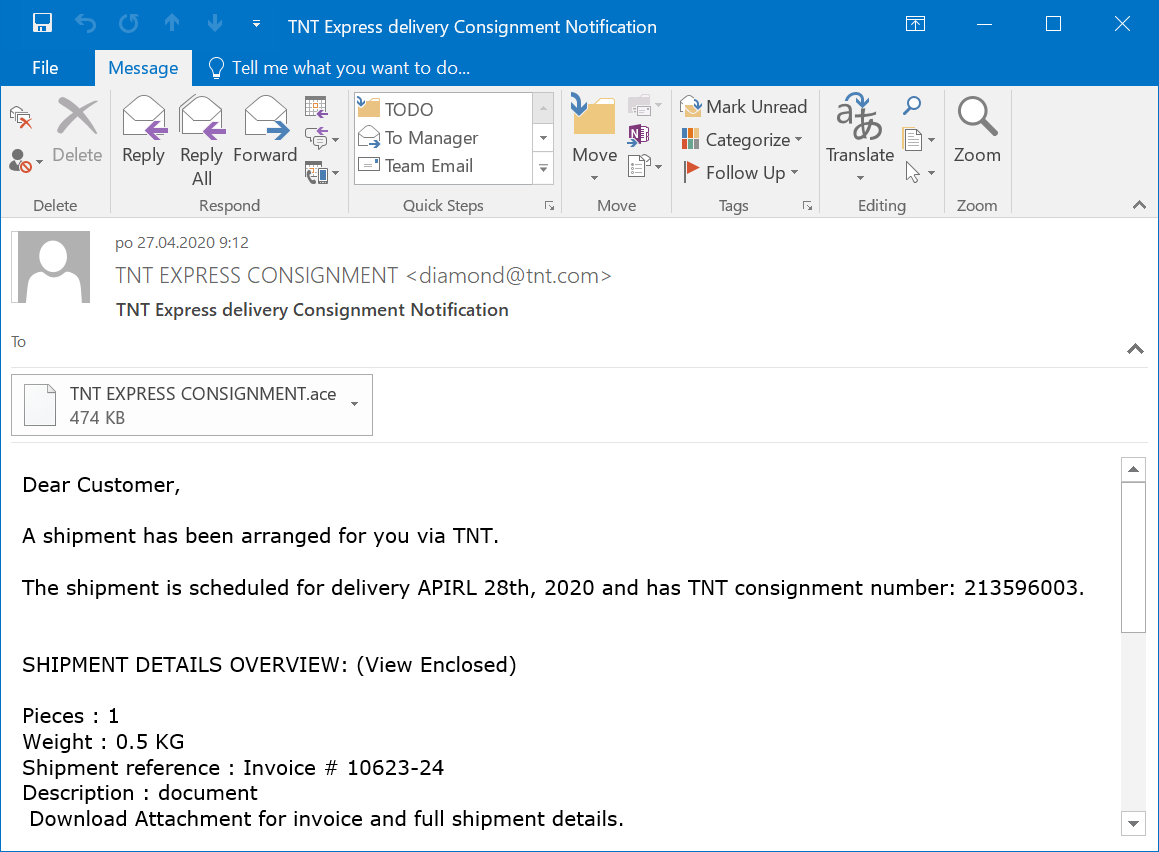
A quick search of the logs for diamond@tnt.com showed that from March 15, 2019, the e-mail gateway stopped 94 similar messages. In all these cases, the messages had an ACE attachment and all their subjects were variations on the same theme.
I didn't manage to get the earliest e-mails but I extracted the attachments of all the ones I had access to and after eliminating all of the duplicates I was left with 14 malicious executables (some of them with a fake SCR extension).
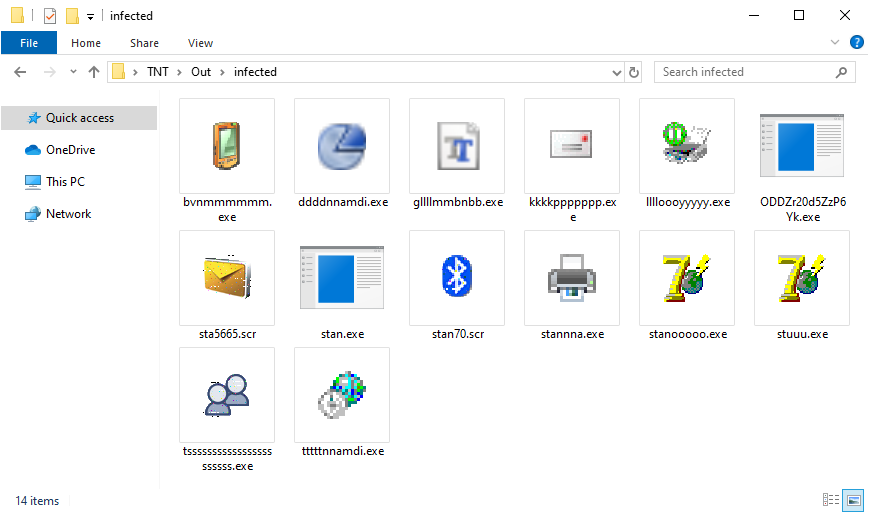
Since I didn't have much time to spend on analyzing the files, I upload several of them to Any.Run and to the Intezer Analyze platform and the results were pretty much always the same – the malicious files were droppers or injectors for Agent Tesla (you may find hashes for all of the executables below).
Since I don’t have access to the earliest attachments, I can’t be sure that the actors behind this campaign used it to spread only Agent Tesla for the entire time, however from the available data it seems to be the case. It appears that the same group has been using nearly the same e-mail template and exactly the same simple trick to bypass SPF checks for more than a year.
In my last diary[2], I mentioned that a group behind phishing campaign, that ran for over three months with minimal changes, seemed to go by the old adage “if it ain't broke don't fix it”. After looking at this campaign, it seems that that the first group definitely wasn't alone in adopting this philosophy.
Indicators of Compromise (IoCs)
|
MD5 |
SHA-1 |
|
|
bvnmmmmmm.exe |
26765d4965893825b65b7fd029fe4da7 |
69dda78ca8714e7b35fa06c17cceec93f150f50c |
|
sta5665.scr |
8cb501944a7e3afd7f641940834c42d0 |
f8048f1b072fd0a2ce155f2297b9c4ae0b920056 |
|
stan.exe |
9c43b1f13e9584a315b1ca6133e52d1d |
c6ed0a356bafd83b15f2377aadaa50610ade75ea |
|
stan70.scr |
2e9ce406373eb8dff8a4c65b211ade25 |
cab446082a47f2c860a06aa33f1f8bf927762a43 |
|
stannna.exe |
f90c78f41aeaf4ee729d9d01af3b4c5b |
37b5002429d2122eef4edb86a1dd6f6ccb450b2c |
|
stanooooo.exe |
89e3c0ff0b33ca29864a9e92e1f11bee |
d85ce6583bdade094716e75fae827258f25656e8 |
|
stuuu.exe |
f1aae5198131803697199c6f1a58fddc |
a19e7a0aeb82dbadbf46bcd1641e41b66b09343a |
|
tsssssssssssssssssssssss.exe |
c45551244a11e446b80ae3657091e8fb |
07654a0dd309f70e94b2d0c83a50ff886678a00d |
|
tttttnnamdi.exe |
35bf4bb31fdf79d238e142130c782190 |
3cab3b9761f0e7469fce39470a86c2152664b6c3 |
|
ddddnnamdi.exe |
b13e9c6593b3861653f13016523e0591 |
9d9c6310aef1a68d0f2f47e35645c945bfba7d04 |
|
gllllmmbnbb.exe |
be4a72b6df954561c5ce592596fda595 |
b1a225852b886cae58214847ffdb6de222bc589d |
|
kkkkppppppp.exe |
1ad593307367d2855480f77af3cec459 |
98f8cc243cff4da0f7ac4a1bca745d341c3c8946 |
|
lllloooyyyyy.exe |
a4f787dc35c4e7ab2fd827cd94174cbf |
453aaa4be9476c105fa2d17d3888e35fe427a726 |
|
ODDZr20d5ZzP6Yk.exe |
ecdedada37ce7ef4c31fd6be32e7ebc7 |
9bb32473c7f3f0a85a7f6bbf9e74d2505d3ca8d9 |
[1] https://isc.sans.edu/forums/diary/Phishing+email+spoofing+SPFenabled+domain/25426/
[2] https://isc.sans.edu/forums/diary/Look+at+the+same+phishing+campaign+3+months+apart/26018/


Comments