DeepBlueCLI: Powershell Threat Hunting
Happy New Year! Those among you who participated in the SANS Holiday Hack Challenge, also known as Kringlecon 2, this holiday season may have found themselves exposed to new tools or the opportunity to utilize one or two that had not hit your radar prior. Such was the case for me with DeepBlueCLI, a PowerShell module for threat hunting via Windows Event Logs.
While others such as EQL and stoQ (an automation framework that helps to simplify the mundane and repetitive tasks an analyst is required to do) come to light, I also reveled in a chance to use RITA for Zeek logs analysis. I covered RITA in 2015 for toolsmith #111, and have really enjoyed its evolution. I found the answer to the related Kringlecon challenge with the current iteration of RITA in two steps. Alas, this is an opportunity to highlight the benefits of yet another cool SANS-related offering in DeepBlueCLI. While the wild man and SANS veteran we all know and love as John Strand is party to RITA, the cool and collected Eric Conrad and the SANS Blue Team bring us DeepBlueCLI.
DeepBlueCLI, in concert with Sysmon, enables fast discovery of specific events detected in Windows Security, System, Application, PowerShell, and Sysmon logs. And I do mean fast, DeepBlueCLI is quick against saved or archived EVTX files. It does take a bit more time to query the running event log service, but no less effective.
You can expect specific command-line logs to be processed including process creation via Windows Security Event ID 4688, as well as Windows PowerShell Event IDs 4103 and 4104, and Sysmon Event ID 1, amonst others. Be sure to read all the GitHub documentation but note the following detection categories, with multiple detections per:
- Suspicious account behaviors
- Command line/Sysmon/PowerShell auditing
- Service auditing
- Mimikatz
- EMET & Applocker Blocks
I'll run through a number of the examples via the sample EVTX files provided via the project download and share with you a variety of results. We'll also crank out some output options based on said results. Note: Run PowerShell as admin for best the required effect. Also be sure to review the Set-ExecutionPolicy Readme if you receive a running scripts is disabled on this system error. Also read the project documentation to ensure proper logging configurations for your target systems, this is quite important to ensure effective coverage and positive results.
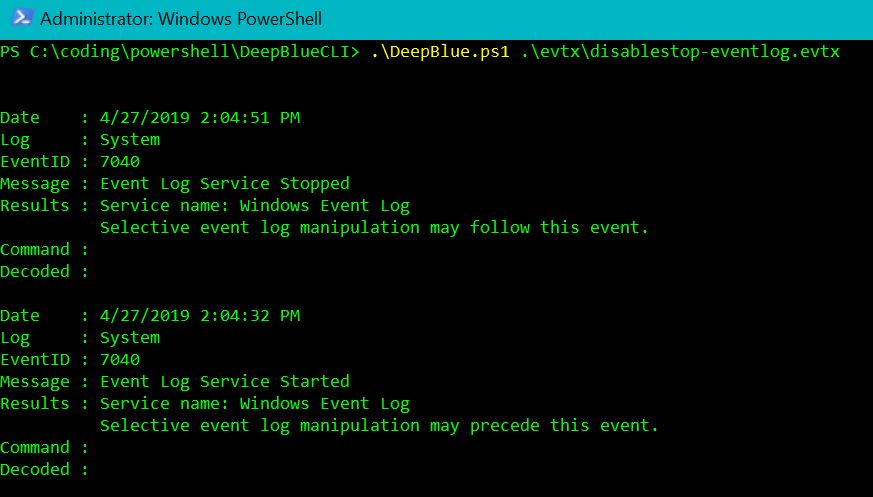
Let's begin with a check for Event log manipulation:
Figure 1: Event log manipulation
Clearly Figure 1 shows a stop and start of the Event Log Service.
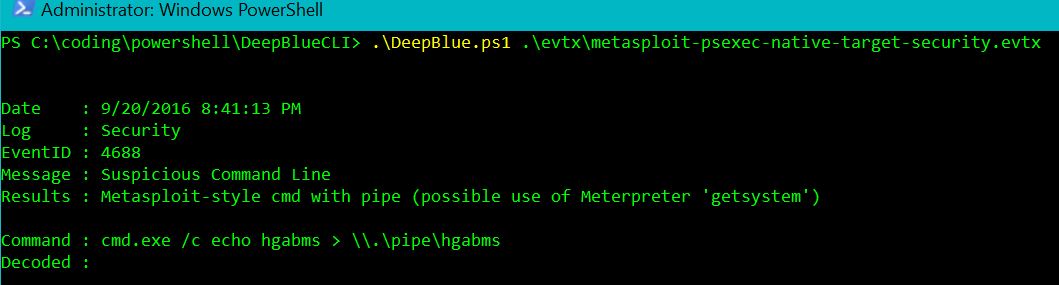
Next, the Metasploit native target (security) check:
Figure 2: Metasploit native target (security)
Someone has definitely run Metasploit on this system, per Figure 2. Note that when “cmd.exe connects to Meterpreter's named pipe, Meterpreter has the opportunity to impersonate that security context.” A Metasploit target (system) check clearly makes sense next:
Figure 3: Metasploit native target (system)
Sure enough, we yield Event IDs 7036 (Service Control Manager) and 7045 (A new service was installed in the system), the commands for which are clearly “Metasploit-style”.
Metasploit PowerShell target (security) and (system) return both the encoded and decoded PowerShell commands where .\DeepBlue.ps1 .\evtx\metasploit-psexec-powershell-target-security.evtx parses Event ID 4688 (a new process has been created, and not a good one) specifically, and .\DeepBlue.ps1 .\evtx\metasploit-psexec-powershell-target-system.evtx provides full context for the above mentioned 7036 and 7045 events.
.\DeepBlue.ps1 .\evtx\mimikatz-privesc-hashdump.evtx for Mimikatz lsadump::sam will return findings for Event ID 4673 (a privileged service was called) where Message: Sensititive Privilege Use Exceeds Threshold and Results: Potentially indicative of Mimikatz, multiple sensitive privilege calls have been made are indicated.
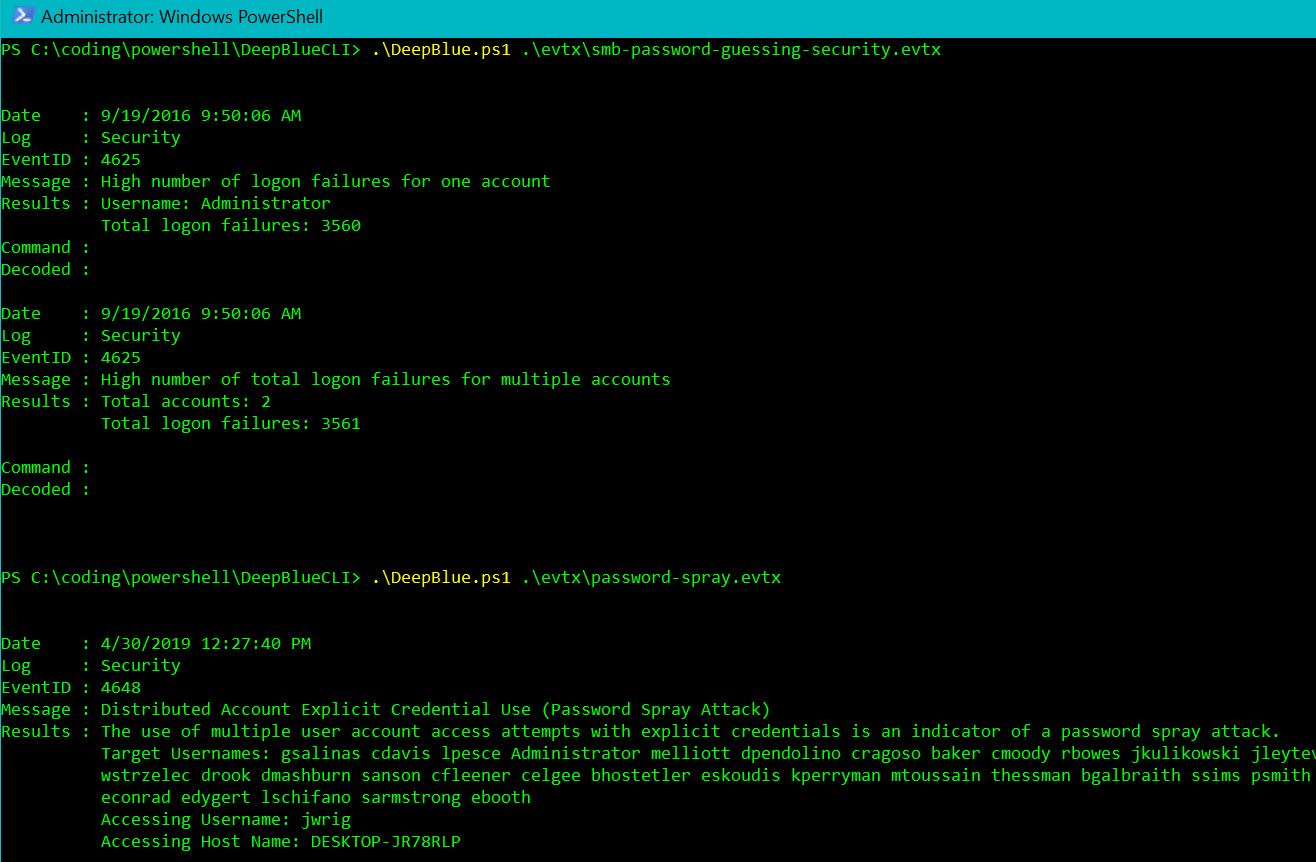
The New user creation check for Event IDs 4720 (new user created) and 4732 (user added to local Administrators group), and the Obfusation (encoding) and (string) checks for Event ID 4104 (script block), work precisely as expected, as do the Password guessing (Event ID 4625 - failed logon attempt) and Password spraying checks (Event ID 4648 - a logon was attempted using explicit credentials), per Figure 4.
Figure 4: Password guessing and spray
As a fond PowerSploit user, I appreciate the PowerSploit (security) and (system) checks, again decoding related 4688 events, as does the PSAttack check. For User added to administrator group .\DeepBlue.ps1 .\evtx\new-user-security.evtx returns the same results as part of New user creation.
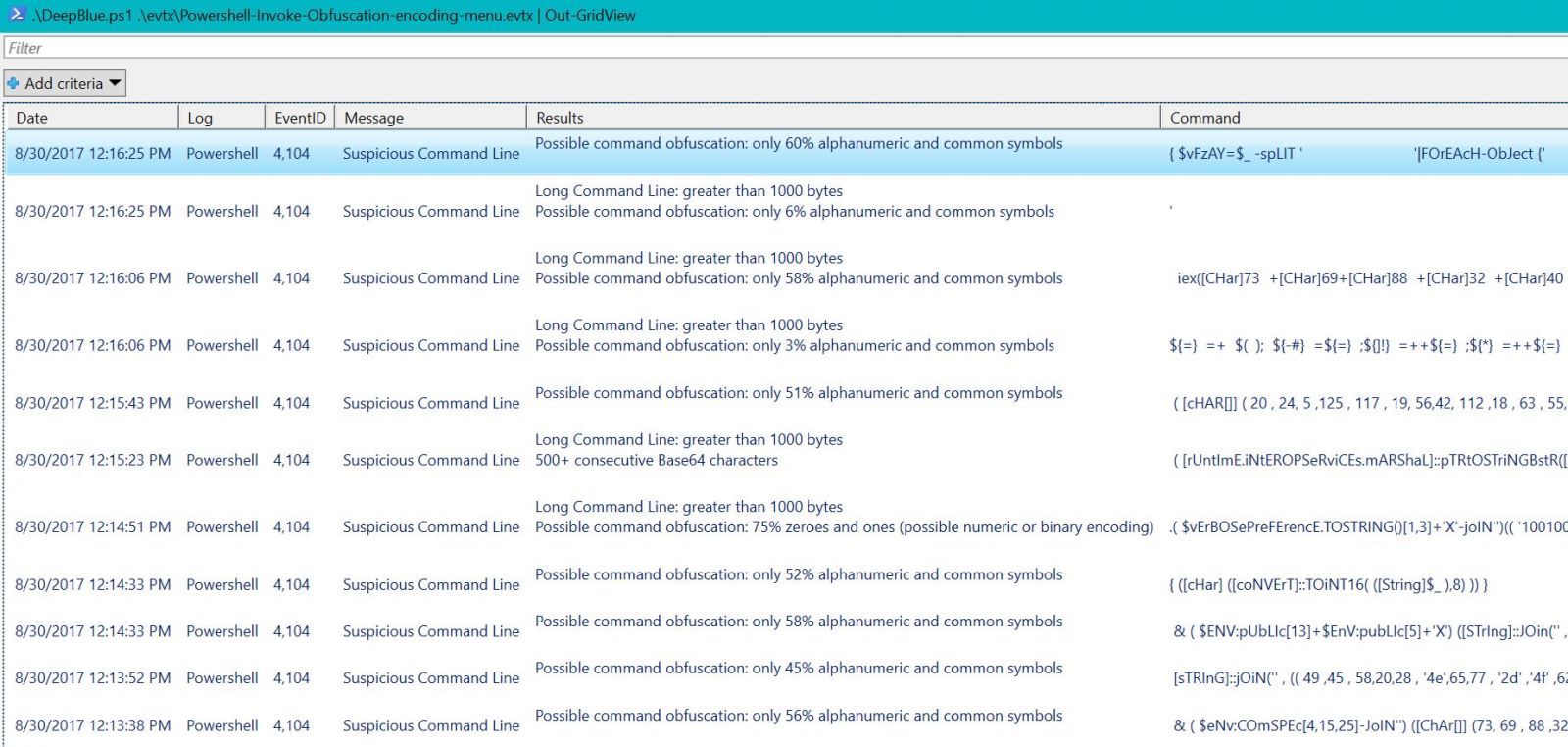
Finally, let's generate a bit of proper output. You can expect CSV, Format list, Format table, GridView, HTML, JSON, and XML as output options, but I'm particularly fond of GridView when you're in the midst of a down and dirty firefight. .\DeepBlue.ps1 .\evtx\Powershell-Invoke-Obfuscation-encoding-menu.evtx | Out-GridView serves us well as an exemplar, as seen in Figure 5.
Figure 5: GridView output
DeepBlueCLI is DFIR smoke jumper must-have. Eric and team really have built a useful and efficent framework that has been added to my preferred arsenal thanks to Kringlecon.
Obviously, you'll want to give DeepBlueCLI a good look, as well as the others mentioned in the intro, and above all else, even if only a best effort, give Kringlecon 3 a go next year. It really is a blast, you'll learn a ton.
Cheers…until next time.



Comments