Retrieving Second Stage Payload with Ncat
In diary entry "Analyzing First Stage Shellcode", I show how to analyze first stage shellcode when you have no access to the server with the second stage payload.
If you do have access, you have the option to connect to that server and retrieve the second stage payload for further analysis.
In this example, I'm using Ncat to connect to the server:
.png)
I use following options:
- -vv to increase verbosity
- --recv-only to receive data only, without sending any data
- -o dump.bin.vir to save the retrieved payload to a file
- redirect to NUL to avoid cluthering verbose output with payload data
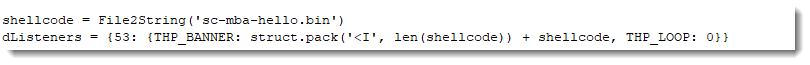
My TCP honeypot tcp-honeypot.py is configured to send data, and wait for input. That's why Ncat exits after the TCP timeout occurs. I can configure my honeypot to close the connection immediately after sending the payload, by setting the read loop to 0 iterations (THP_LOOP 0):
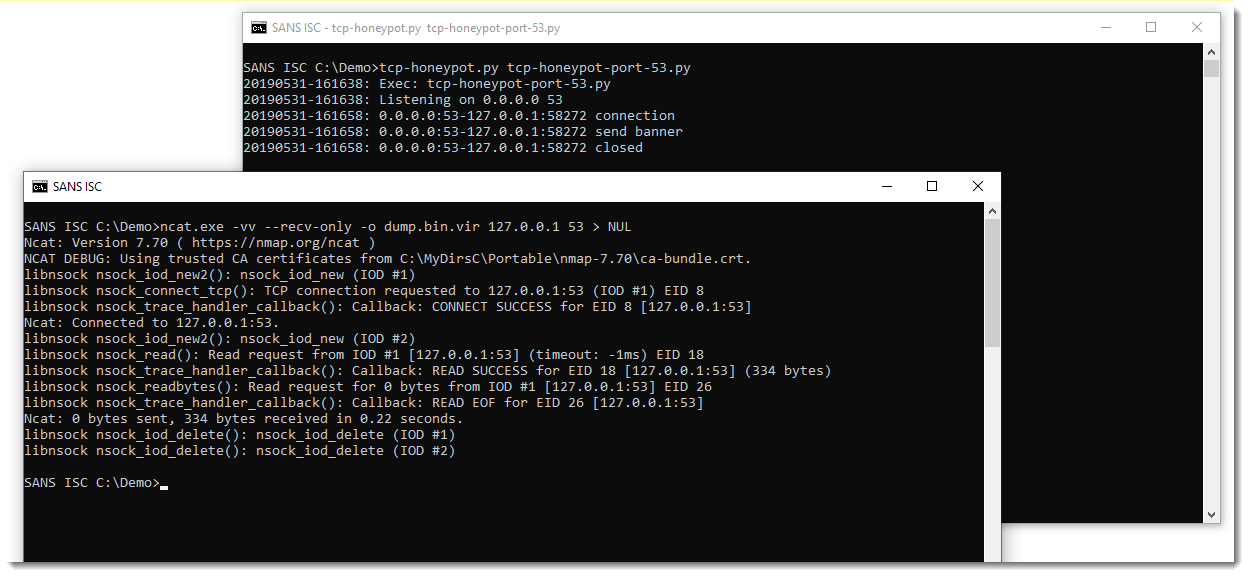
Then Ncat exits immediately after receiving the payload:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments