Numeric obfuscation: another example
I favor static analysis, because I want to understand, step by step, what a malicious script is doing. But I will often also perform dynamic analysis of the same sample, to build a complete picture.
A Twitter follower asked about a more complex example of numeric obfuscation in malicious scripts. It's an arms race: obfuscation can be so complex, that you don't have enough time to perform static analysis. Dynamic analysis (or emulation) is the alternative.
The example of our Twitter follower however, is not too complex for static analysis + emulation: I will extract the algebraic expressions, and since they are identical in the VBA and Python language, I will evaluate them in Python.
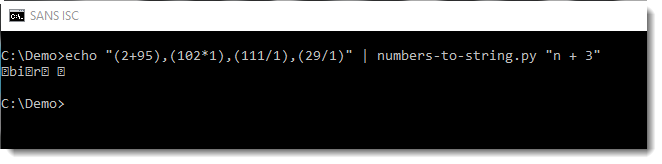
As can be observed, numbers-to-string.py does not yield the desired result in this example:
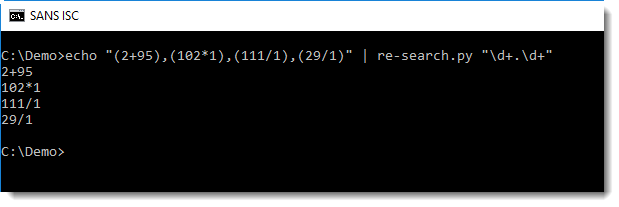
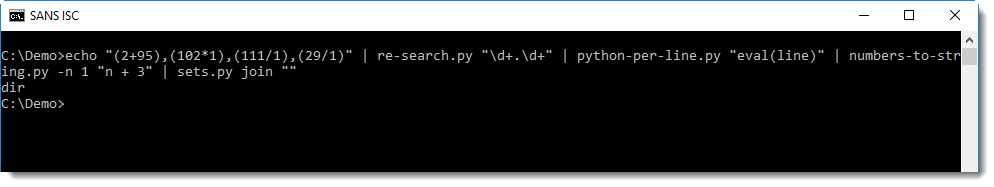
First with re-search.py and regular expression \d+.\d+ I extract all expressions composed of two numbers and an operator:
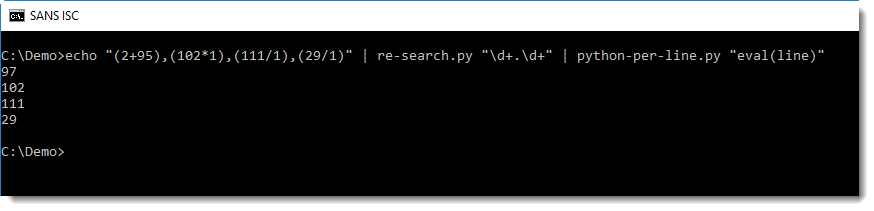
Then I pass this on to python-per-line.py, to evaluate these algebraic expressions in Python (using Python expression eval(line)):
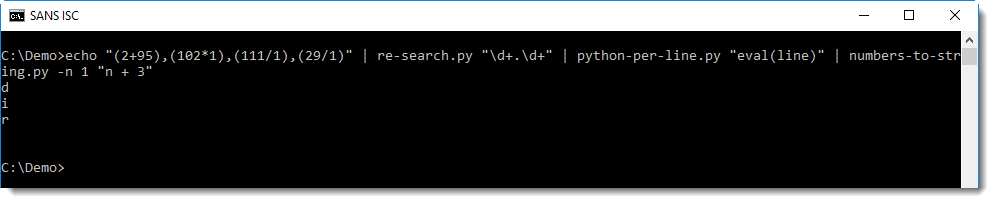
And then I can use numbers-to-string.py, but with option -n 1, because this tool looks for lines with 3 numbers at least (by default):
Finally, each line (e.g. character) is joined into a single line with sets.py:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments