Analyzing XPS files
Lorna analyzed a reader submitted XPS file: a phishing attempt. I would like to provide some pointers for the static analysis of XPS files.
XPS files are like OOXML files (MS Office files): mainly XML files inside a ZIP container, e.g. a file according to the Open Packaging Conventions specification.
Here you can see the content with zipdump.py:
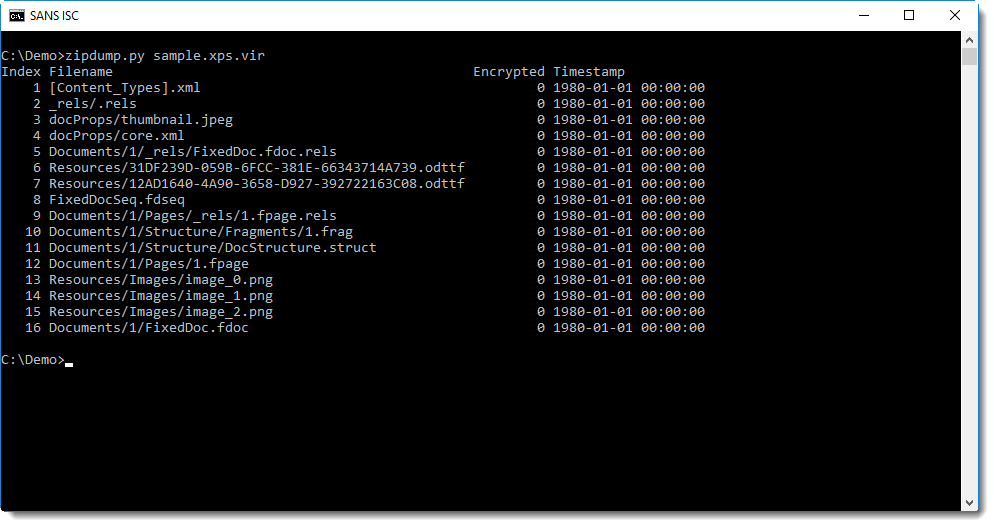
The presence of files with extensions .fpage and .fdoc is an indicator that this is a XPS file. We can also look inside the first file [Content_Types].xml, it defines all the MIME media types present in this archive:
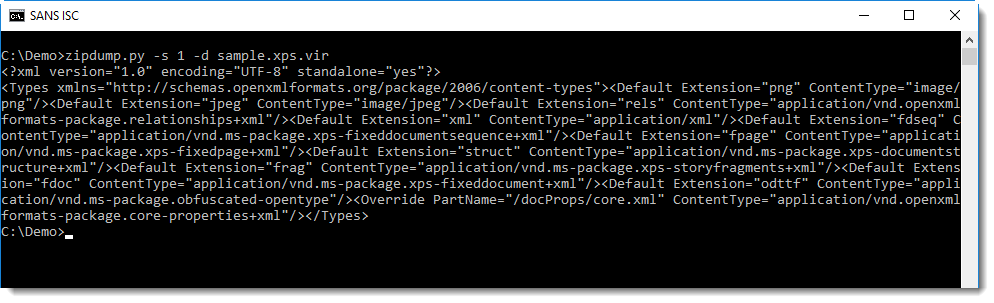
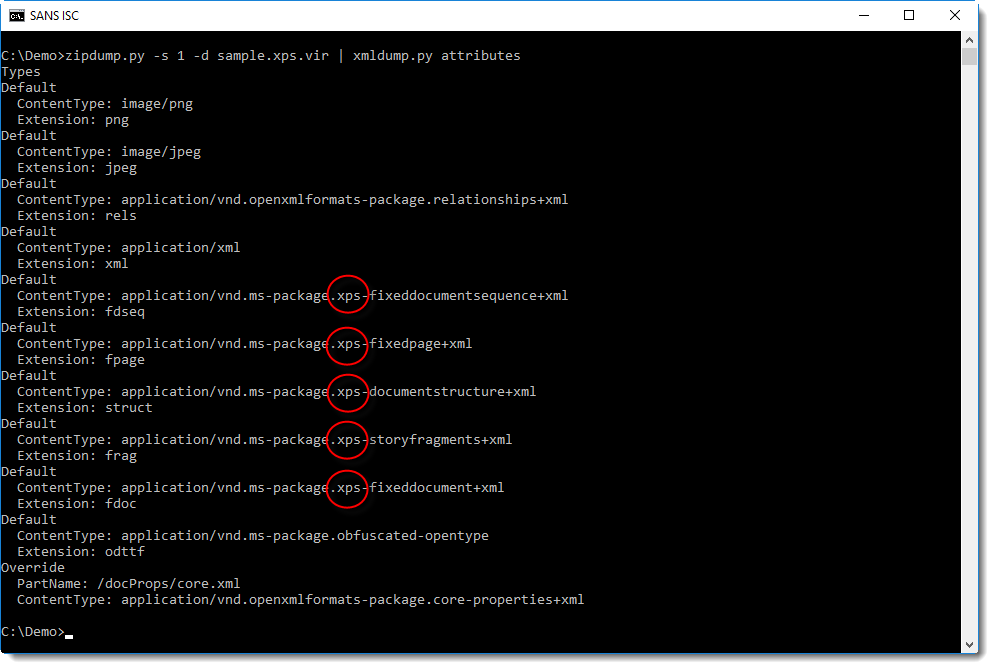
You might notice some XPS MIME media types in this XML document. Extracting the attributes with xmldump.py will make this more obvious:
File 12 (1.fpage) is an XML file describing the content of a page:
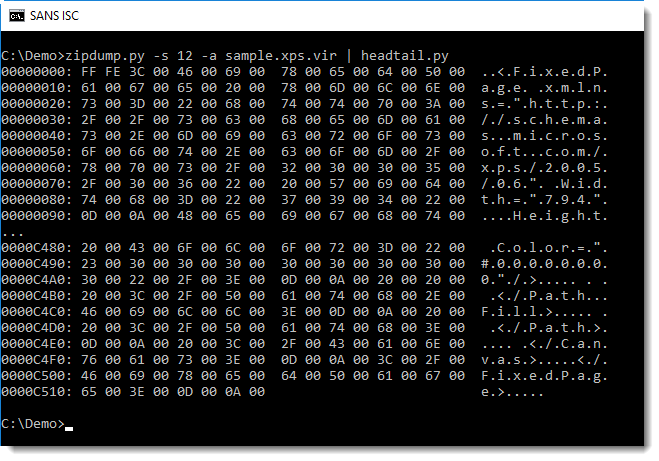
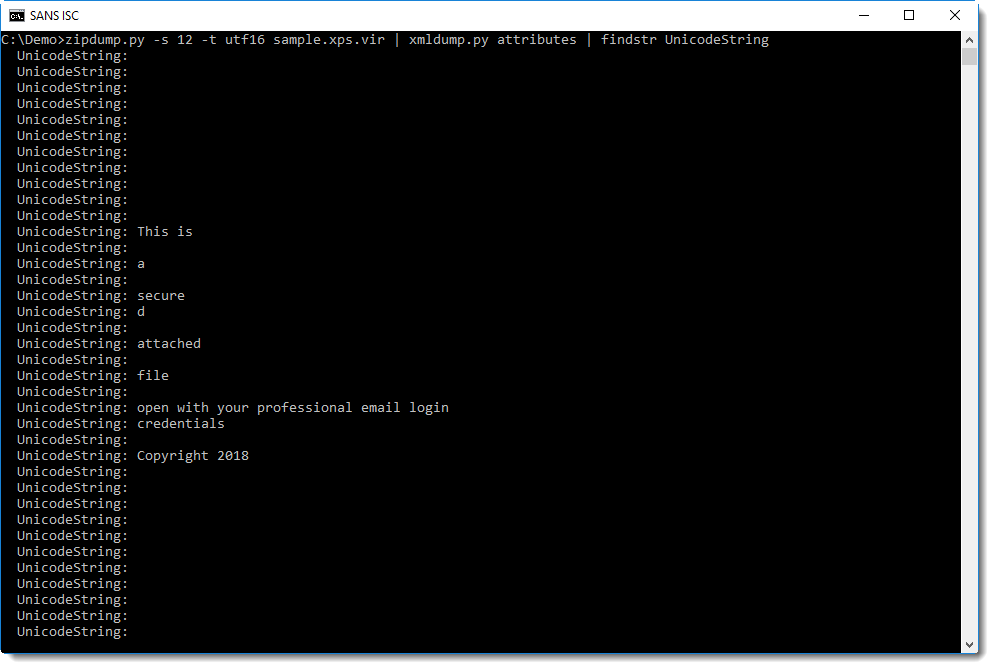
We can see it's UNICODE, so let's decode it:
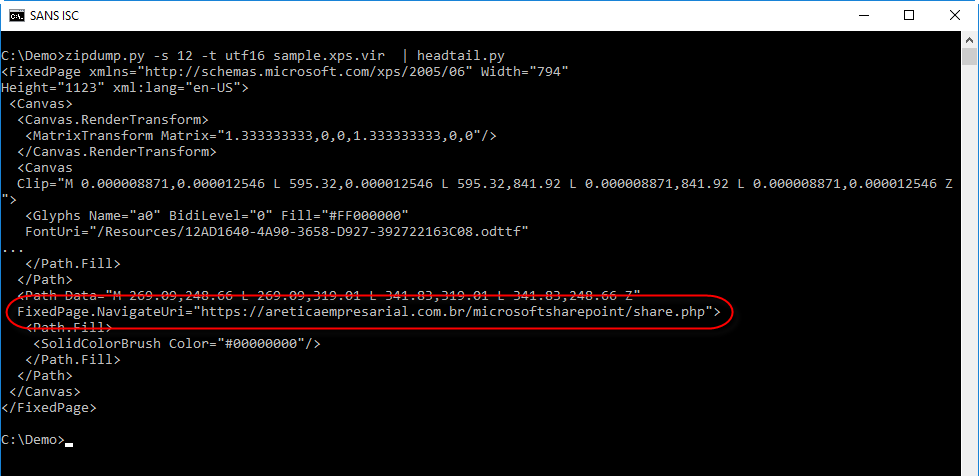
The phishing URL Lorna analyzed is visible in this output. We can also use re-search.py to extract all URLs found in this file:
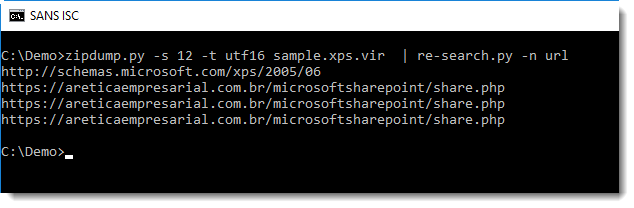
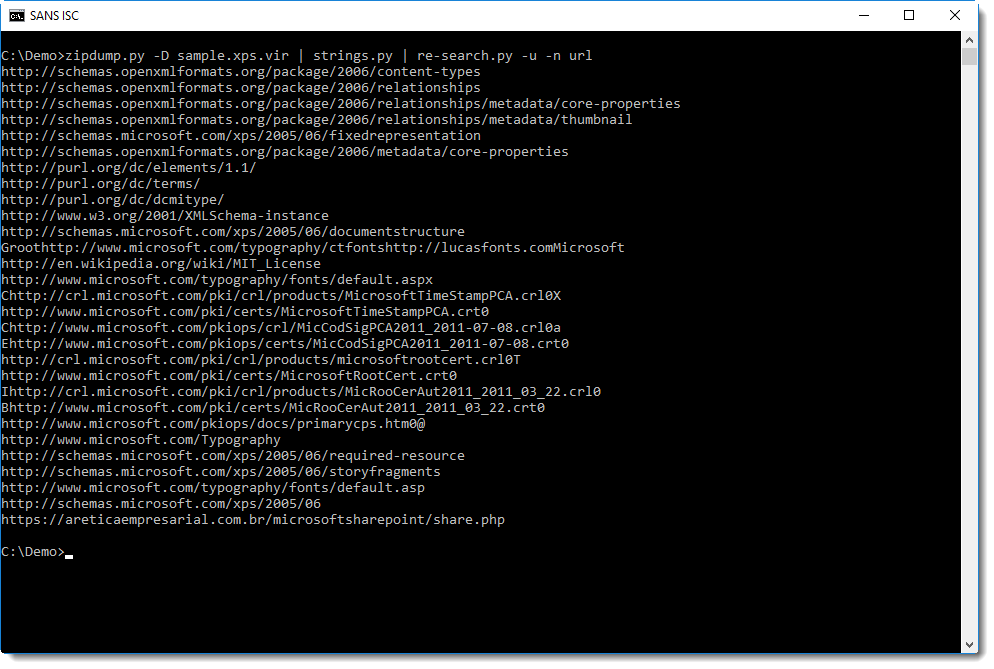
Or even the URLs from all files, but this will give a long list with legitimate URLs, so I use option -u (unique) to print each URL only once:
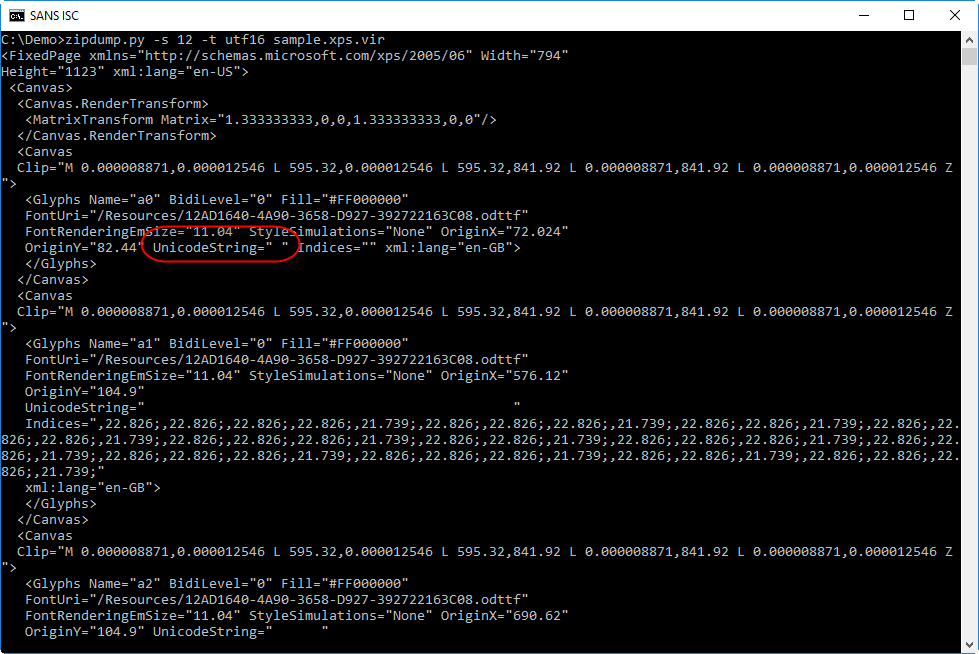
It's also possible to extract the text rendered by the page file. It can be found in attributes UnicodeString:
If you have encountered XPS files used for phishing or other malicious activities, please post a comment.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments