More malspam pushing Lokibot
Introduction
A tweet last week by @malwareunicorn reminded me I haven't searched out any Loki-Bot malspam in a while.
Shown above: This tweet gave me a good chuckle.
Loki-Bot (also spelled "Loki Bot" or "LokiBot") is an information stealer that sends login credentials and other sensitive data from an infected Windows host to a server established for each malware sample. It's commonly distributed through malicious spam (malspam), and I usually run across samples of Loki-Bot every day. More information can be found in a SANS Reading Room paper written by Rob Pantazopoulos here.
I've already written two ISC diaries on Loki-Bot since October 2017 (here and here). Today's diary is a reminder that Loki-Bot is very much alive and actively distributed through malspam on a daily basis. You'll frequently find tweets tagged #Lokibot on Twitter.
Details
I often find examples of Loki-Bot malspam through VirusTotal Intelligence. A quick search revealed one such email in the early hours of Monday 2018-06-11 (UTC time). It was heavily sanitized, so there's little information other than the date, sender, subject line, and attachment.
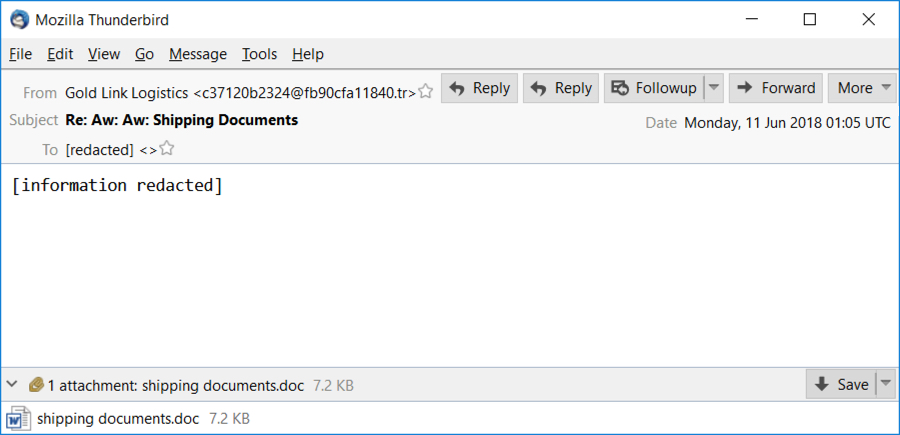
Shown above: The email I pulled from VirusTotal Intelligence.
The email has an RTF attachment disguised as a Word document. When opened with a vulnerable version of Microsoft Office, an exploit for CVE-2017-11882 will download and install Loki-Bot malware on a vulnerable Windows host. In this case, a request for the Loki-Bot executable was done over HTTPS. Approximately two minutes later, the infected Windows host began generating post-infection HTTP traffic associated with Loki-Bot.
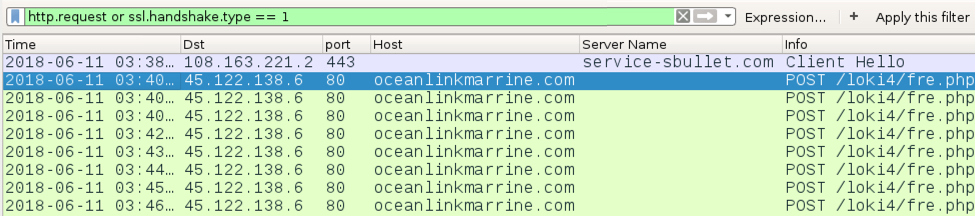
Shown above: Traffic from the infection filtered in Wireshark.
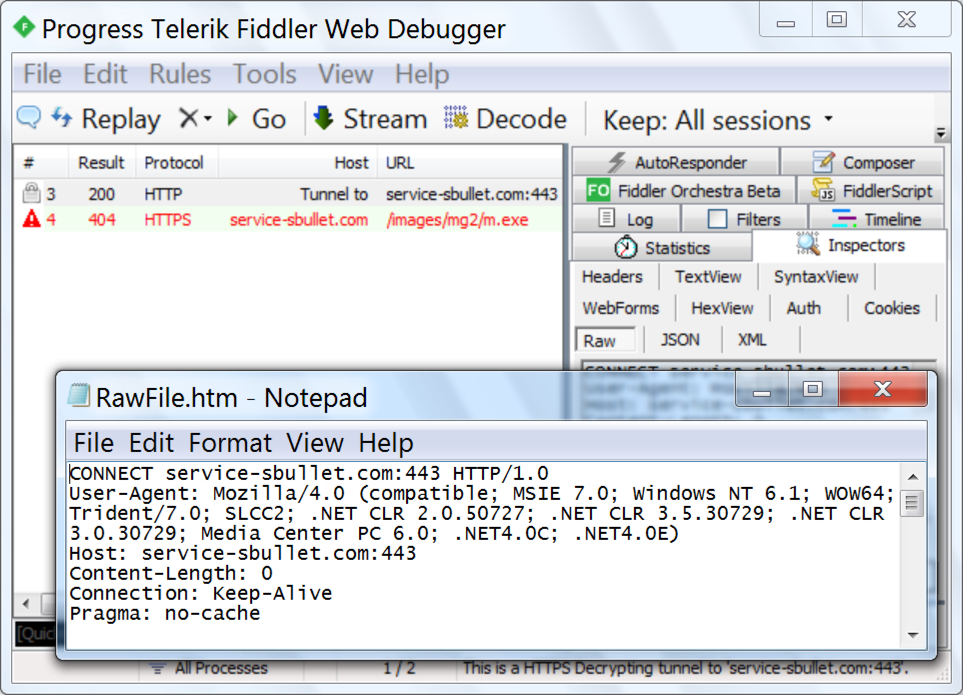
Shown above: HTTPS request for the Loki-Bot binary shown in Fiddler.
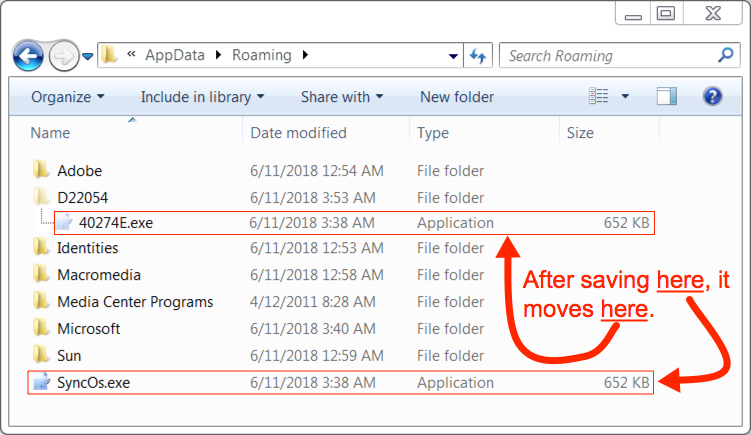
Shown above: Loki-Bot executable on my infected Windows host.
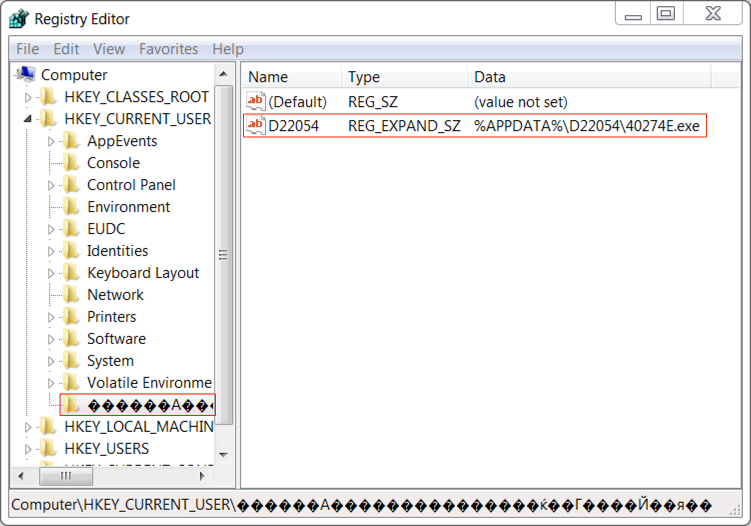
Shown above: Windows registry entry to keep Loki-Bot persistent on my infected host.
Indicators
Indicators are not the same as a block list. If you need to block the associated web traffic, block anything going to these two domains:
- oceanlinkmarrine.com
- service-sbullet.com
Information from the malicious spam:
- Date: Sunday, 11 Jun 2018 01:05 UTC
- From: "Gold Link Logistics" <c37120b2324@fb90cfa11840.tr>
- Subject: Re: Aw: Aw: Shipping Documents
- Attachment Name: shipping documents.doc
Traffic from an infected Windows host:
- 108.163.221.2 TCP port 443 (HTTPS) - service-sbullet.com - GET /images/mg2/m.exe
- 45.122.138.6 TCP port 80 (HTTP) - oceanlinkmarrine.com - POST /loki4/fre.php
Associated malware:
SHA256 hash: b66d5b28c57517b8b7d2751e30e5175149479e5fde086b293a016aac11cdd546
- File size: 7,347 bytes
- File name: shipping documents.doc
- File description: RTF exploiting CVE-2017-11882 disguised as a Word document
SHA256 hash: a747eeac9ae8ee9317871dfaa2a368f2e82894f601a90614da5818f8f91d1d78
- File size: 667,648 bytes
- File location: hxxp://service-sbullet.com/images/mg2/m.exe
- File description: Windows executable file for Lokibot
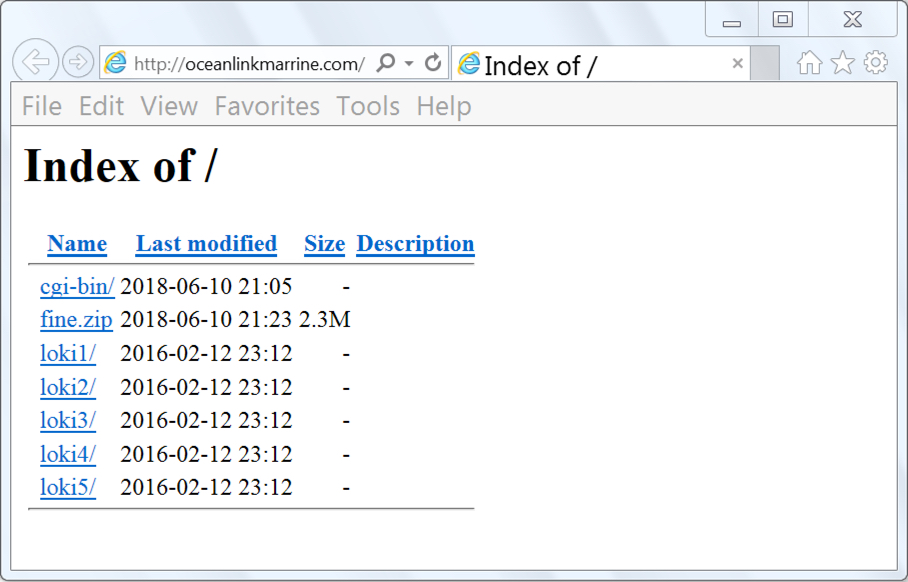
Shown above: Try searching both oceanlinkmarrine.com and service-sbullet.com for more info.
Final words
As usual, properly-administered and up-to-date Windows hosts are not likely to get infected. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments