Comment your Packet Captures!
When you are investigating a security incident, a key element is to take notes and to document as much as possible. There is no “best” way to take notes, some people use electronic solutions while others are using good old paper and pencil. Just keep in mind: it must be properly performed if your notes will be used as evidence later… With investigations, there are also chances to you will have to deal with packet captures. Many security tools can record samples of network traffic or you can maybe need a full-packet capture[1]. Some tools, like Moloch, allow you to “tag” some conversations. Later, you can search for them to find back interesting traffic:
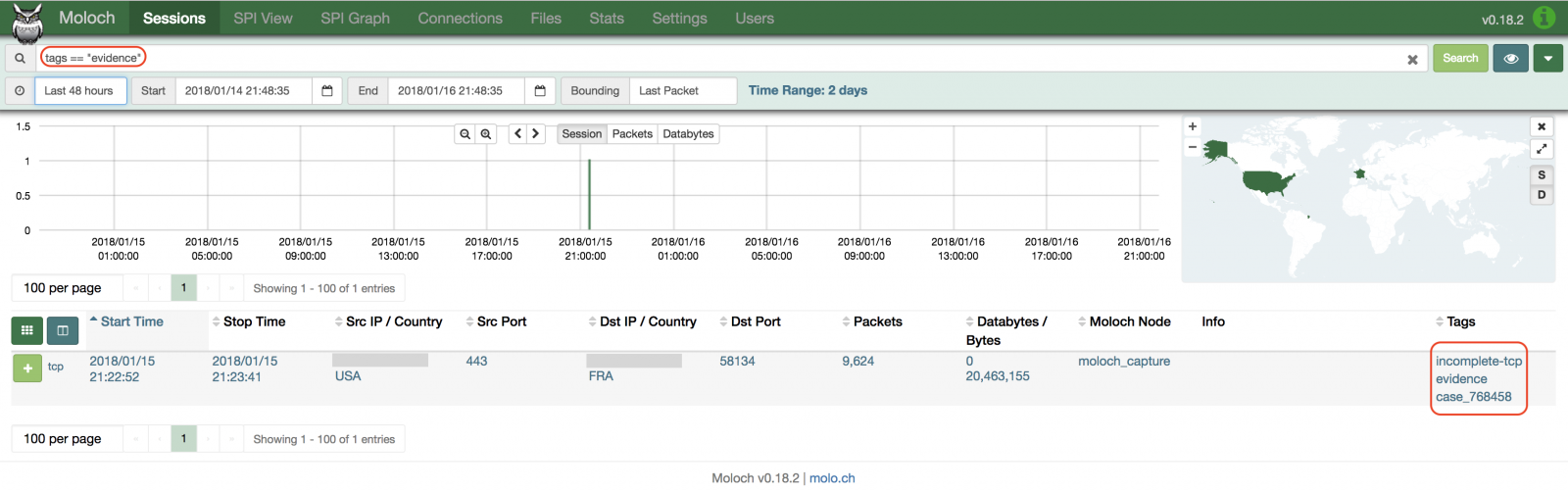
Tags are helpful to assign some flows to a case being investigated or to categorize them (“suspicious”, “exfiltration”, “exploitation”, etc). I’m a big fan of Moloch but, with this kind of tools, added tags are stored in the ElasticSearch database. If you export the data in PCAP format, you will lose your tags. How to add them to the PCAP itself? To achieve this, let’s have a look at the PCAP-ng format[2]. It extends the simple PCAP format features with more options like:
- to store more capture related information
- extended time stamp precision
- capture interface information
- capture statistics
- mixed link layer types
- name resolution information
- user comments
The latest information is definitively a nice feature. Wireshark supports PCAP-ng natively. While reviewing traffic, it’s easy to add a comment: Select the packet, right click and select “Packet Comment”. You can now enter your comment in a small editor window. To display the existing comments when you open an existing PCAP-ng file (or to see yours), you can add an extra column to the main Wireshark windows:
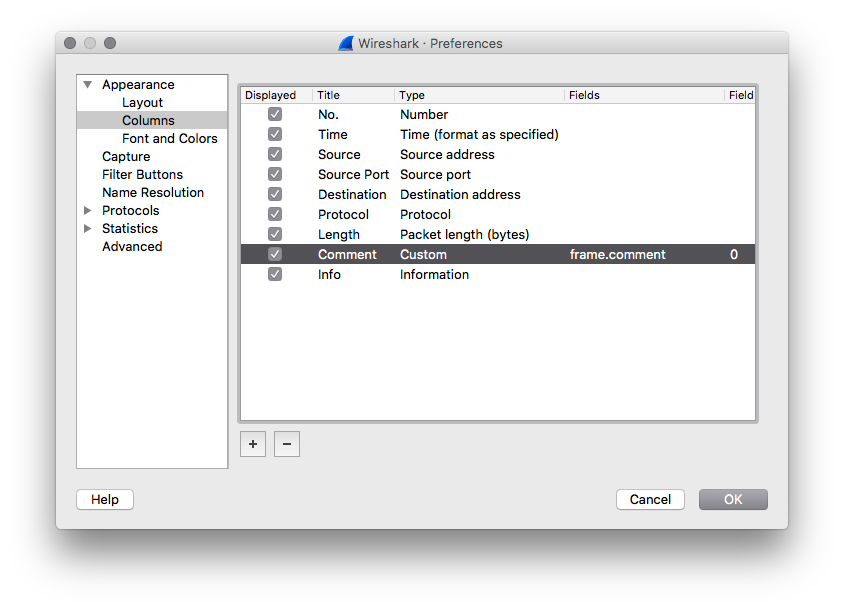
And of course, you can search for comments. This filter displays all packets that belong to the incident “1234”:
frame.comment contains “1234”
If you need to save the PCAP to share it with other handlers or colleagues, Wireshark will automatically select the PCAP-ng format (because extra metadata have been added - comments in this case).
What’s nice, you can also search/display comments with command line tools:
$ tshark -r test.pcapng -Y frame.comment 916 177.563553 Cisco_5a:fa:30 CDP/VTP/DTP/PAgP/UDLD CDP 370 This is Cisco CDP packet. Case ID #1234 Device ID: cisco-ap.xxxx Port ID: Dot11Radio0.1 3314 540.372018 192.168.254.212 59920 104.199.42.108 TCP 129 TCP Error? [TCP Retransmission] 59920 → 443 [PSH, ACK] Seq=3988 Ack=5698 Win=4096 Len=63 TSval=1092967452 TSecr=898909663
On Mac OSX, the native tcpdump command can also handle comments:
$ tcpdump -r test.pcapng -n -k C | grep -v ' () ' reading from PCAP-NG file test.pcapng 17:47:58.181178 (This is Cisco CDP packet. Case ID #1234) CDPv2, ttl: 180s, Device-ID 'cisco-ap.xxxx', length 348 17:54:00.989643 (TCP Error?) IP 192.168.254.212.59920 > 104.199.42.108.443: Flags [P.], seq 3987:4050, ack 5698, win 4096, options [nop,nop,TS val 1092967452 ecr 898909663], length 63
Finally, if you use cloud services to handle your capture files, most of them support pcap-ng and comments, like CloudShark[3]. From now, you don't have any valid excuse for not commenting your PCAP files!
[1] https://isc.sans.edu/forums/diary/The+easy+way+to+analyze+huge+amounts+of+PCAP+data/22876/
[2] https://wiki.wireshark.org/Development/LibpcapFileFormat
[3] https://support.cloudshark.org/user-guide/#comments
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key


Comments