Malspam pushing Formbook info stealer
Introduction
On Monday 2017-10-02, I ran across malicious spam (malspam) pushing Formbook, an information stealer. Arbor Networks has a good article about Formbook here. Today's diary examines the associated email, traffic, malware, and infected Windows host.
The email
The email is disguised as a FedEx delivery notice. It has a link to a compromised website that's hosting malware. The link points to a supposed document for this fake delivery.
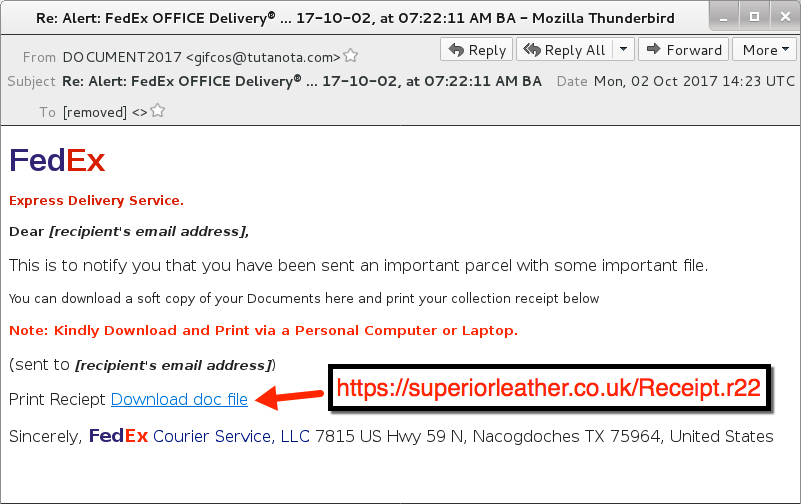
Shown above: Screenshot of the malspam.
Clicking on the link returned a RAR archive. The RAR archive contains a Windows executable that's poorly-disguised as some sort of receipt.
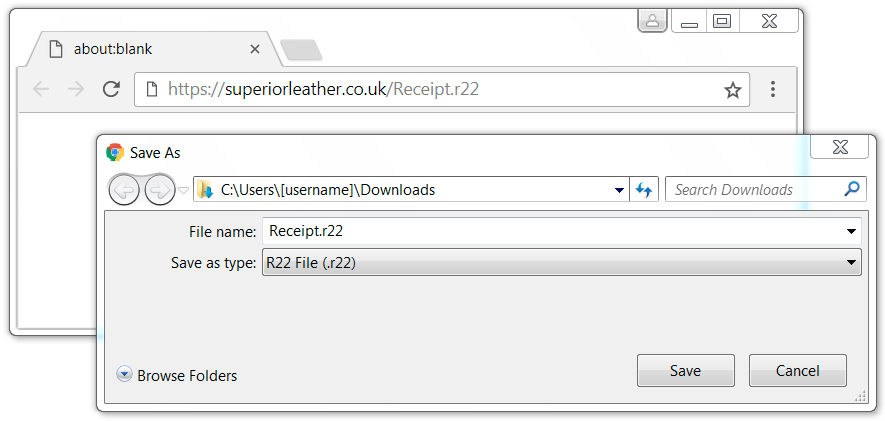
Shown above: Downloading malware from a link in the email.
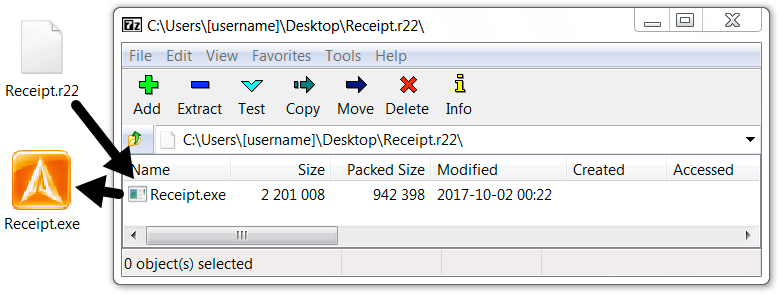
Shown above: Contents of the downloaded RAR archive.
The traffic
The malware was downloaded through an HTTPS link, so Wireshark only reveals the domain for that request. All post-infection traffic was HTTP, and it followed patterns already noted in Arbor Networks' write-up on Formbook. I saw plenty of alerts on the post-infection traffic. The Snort subscriber ruleset triggered on user-agent strings in the post-infection traffic, but that activity was identified as Win.Trojan.Punkey. Punkey is Point of Sale (POS) malware, and it's not associated with Formbook traffic. One alert from the EmergingThreats Pro ruleset identified several of the post-infection HTTP requests as Formbook check-in traffic.
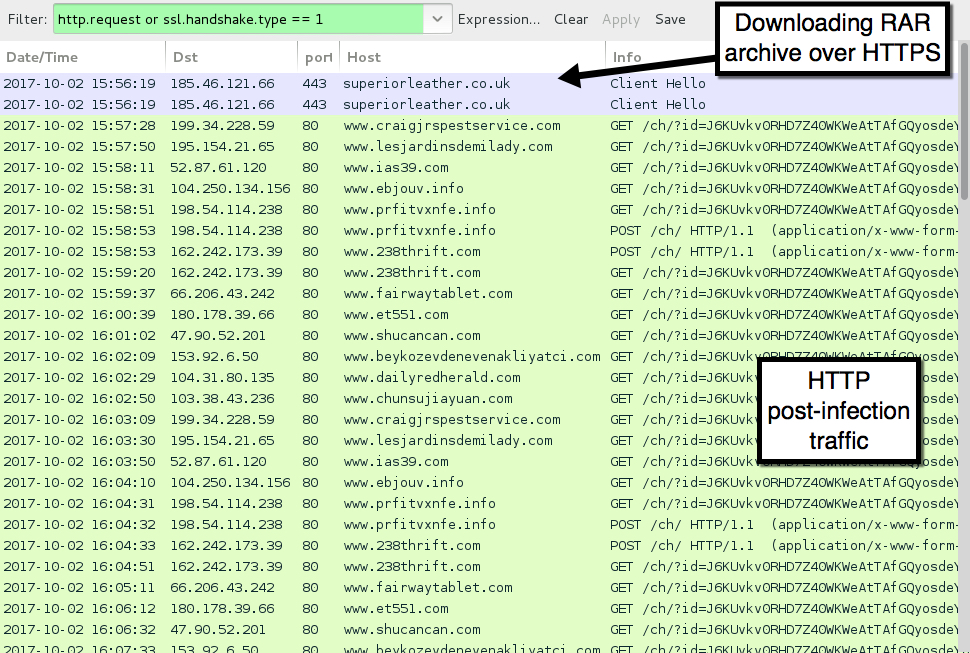
Shown above: Traffic from an infection filtered in Wireshark.
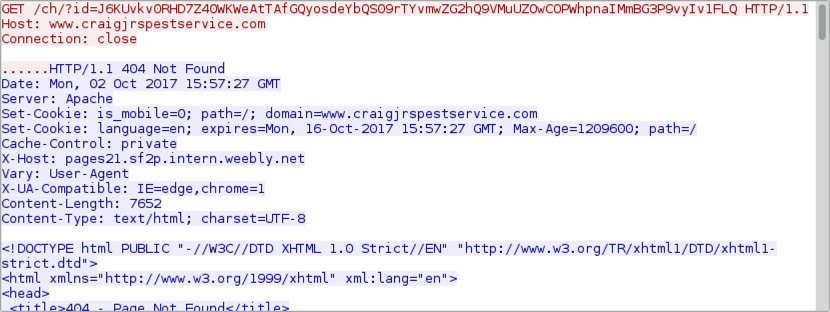
Shown above: Example of an HTTP GET request from the post-infection traffic.
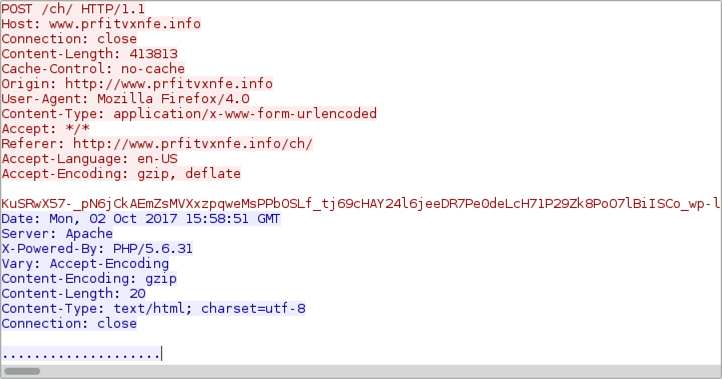
Shown above: Example of an HTTP POST request from the post-infection traffic.
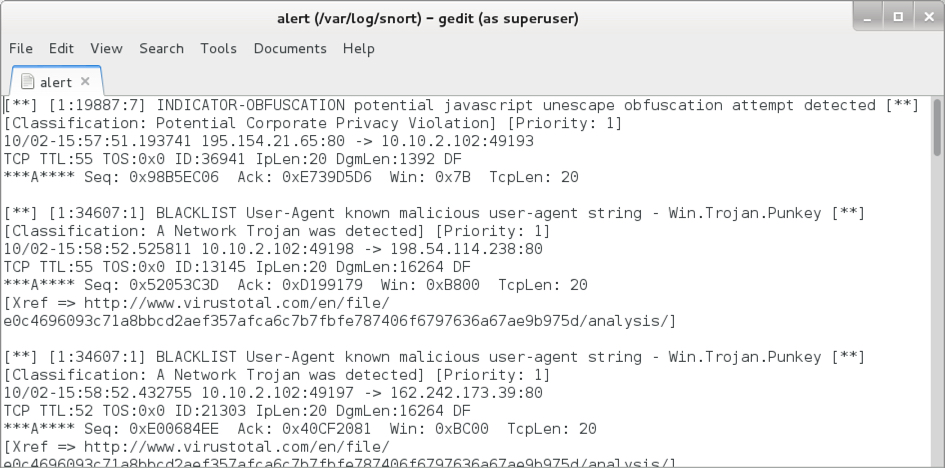
Shown above: Some alerts on the post-infection traffic using Snort and the Snort subscriber ruleset.
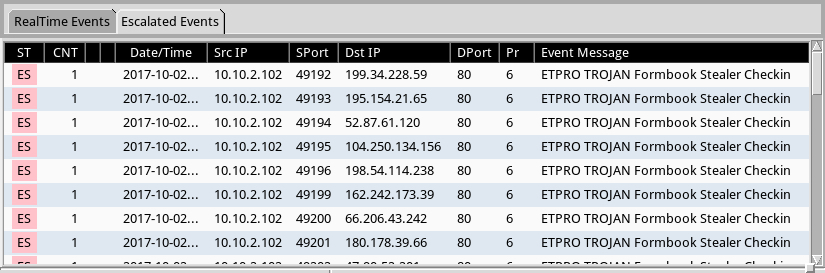
Shown above: Post-infection hits in Sguil using Security Onion running Suricata the EmergingThreats Pro ruleset.
Forensics on the infected host
On the infected Windows host, the malware copied itself to the user's AppData\Roaming directory as winz6j8.bat and made itself persistent through the Windows registry. Also under the user's AppData\Roaming directory was a randomly-named folder containing information sent through HTTP POST requests. These files included screenshots of the Windows desktop. They also stored other sensitive data.
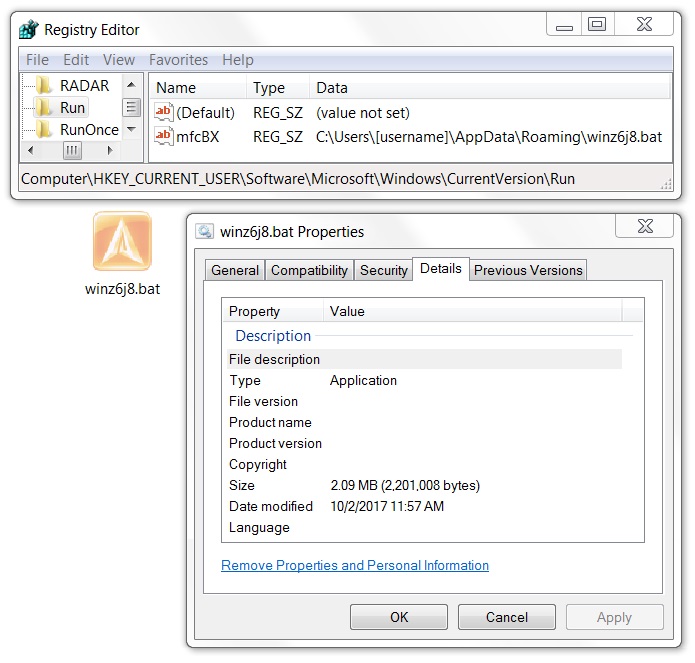
Shown above: Formbook malware persistent on the infected host.
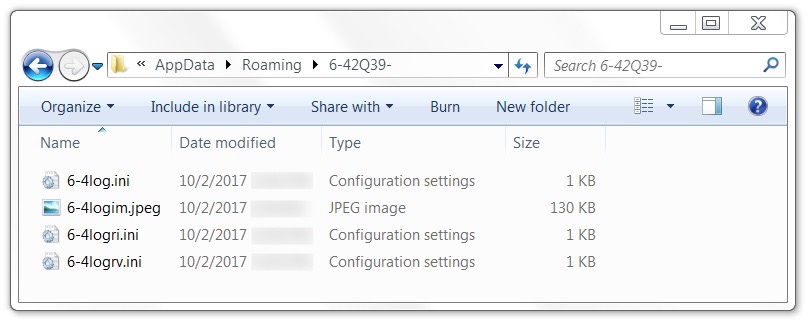
Shown above: Files from the infected host, to be sent over network traffic through HTTP POST requests.
Indicators
The following are indicators seen during the infection from Formbook malspam on Monday 2017-10-02.
Email:
- Date/Time: 2017-11-02 at 14:23 UTC
- Subject: Re: Alert: FedEx OFFICE Delivery® ... 17-10-02, at 07:22:11 AM BA
- From: "DOCUMENT2017" <gifcos@tutanota.com>
- Link from the email: hxxps://superiorleather.co.uk/Receipt.r22
Traffic seen when retrieving the RAR archive:
- 185.46.121.66 port 443 - superiorleather.co.uk - GET /Receipt.r22
Post-infection traffic:
- 47.90.52.201 port 80 - www.shucancan.com - GET /ch/?id=[80 character ID string]
- 52.87.61.120 port 80 - www.ias39.com - GET /ch/?id=[80 character ID string]
- 66.206.43.242 port 80 - www.fairwaytablet.com - GET /ch/?id=[80 character ID string]
- 103.38.43.236 port 80 - www.chunsujiayuan.com - GET /ch/?id=[80 character ID string]
- 104.250.134.156 port 80 - www.ebjouv.info - GET /ch/?id=[80 character ID string]
- 104.31.80.135 port 80 - www.dailyredherald.com - GET /ch/?id=[80 character ID string]
- 153.92.6.50 port 80 - www.beykozevdenevenakliyatci.com - GET /ch/?id=[80 character ID string]
- 162.242.173.39 port 80 - www.238thrift.com - GET /ch/?id=[80 character ID string]
- 180.178.39.66 port 80 - www.et551.com - GET /ch/?id=[80 character ID string]
- 195.154.21.65 port 80 - www.lesjardinsdemilady.com - GET /ch/?id=[80 character ID string]
- 198.54.114.238 port 80 - www.prfitvxnfe.info - GET /ch/?id=[80 character ID string]
- 199.34.228.59 port 80 - www.craigjrspestservice.com - GET /ch/?id=[80 character ID string]
- 162.242.173.39 port 80 - www.238thrift.com - POST /ch/
- 198.54.114.238 port 80 - www.prfitvxnfe.info - POST /ch/
SHA256 hash: c9acea81a8eaece1bea16dba774393907a6141ca260cc072ea9e2d0c0ae6aee4
- File name: Receipt.r22
- File description: RAR archive downloaded from link in the email
SHA256 hash: a341876e11f1a7e0bc370df8affccf52532ab95003bc83199522376eb51a5fa1
- File name: Receipt.exe
- File description: malware extracted from RAR archive - Formbook info stealer
- Post-infection location: C:\Users\[username]\AppData\Roaming\winz6j8.bat
Final words
I see more malspam on a daily basis than I did this time last year. Much of it is from fairly well-documented near-daily campaigns like the Necurs Botnet pushing Locky ransomware or Hancitor malspam. But I'm always happy to examine something relatively less-common like the Formbook information stealer.
As always, system administrators and the technically inclined can easily follow best security practices on their Windows computers. It's relatively easy to avoid these types of infections. Well-known techniques like Software Restriction Policies (SRP) or AppLocker can prevent most malspam-based activity.
A copy of the email, traffic, and associated malware for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments