Checking out the new Petya variant
This is a follow-up from our previous diary about today's ransomware attacks using the new Petya variant. So far, we've noted:
- Several hundred more tweets about today's attack can be found on Twitter using #petya.
- The new Petya variant appears to be using the MS17-010 Eternal Blue exploit to propagate.
- Others claim the new variant uses WMIC to propagate
- Still no official word on the initial infection vector in today's attacks.
- People everywhere are saying today's activity is similar to last month's WannaCry ransomware attacks.
Samples of the new Petya variant are DLL files. So far, we've confirmed the following two SHA256 file hashes are the new variant:
- 027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745
- 64b0b58a2c030c77fdb2b537b2fcc4af432bc55ffb36599a31d418c7c69e94b1
Examining the new Petya variant
Petya is a ransomware family that works by modifying the infected Windows system's Master Boot Record (MBR). Using rundll32.exe with #1 as the DLL entry point, I was able to infect hosts in my lab with the above two DLL samples. The reboot didn't occur right away. However, when it did, my infected host did a CHKDSK after rebooting.
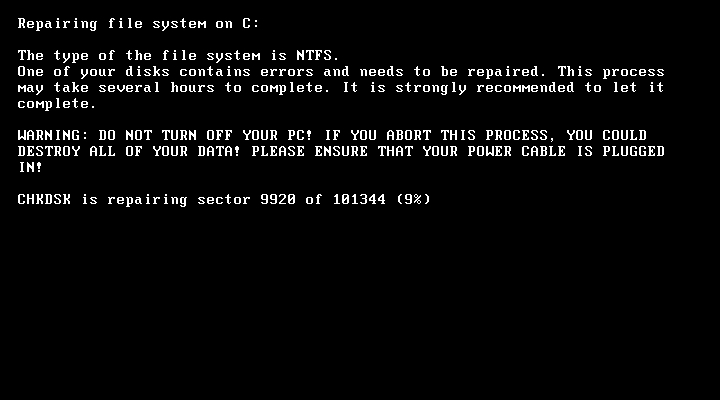
Shown above: An infected host immediately after rebooting.
After CHKDSK finished, the infected Windows host's modified MBR prevented Windows from loading. Instead, the infected host displayed a ransom message.
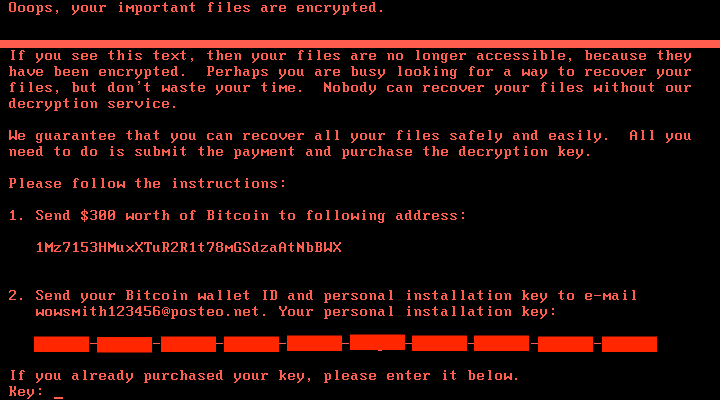
Shown above: The ransom note from a compromised system.
Samples of the new Petya variant appear to have WMI command-line (WMIC) functionality. Others have confirmed this variant spreads over Windows SMB and is reportedly using the EternalBlue exploit tool, which exploits CVE-2017-0144 and was originally released by the Shadow Brokers group in April 2017. My infected Windows hosts immediately generated TCP traffic on port 445 and did ARP requests for local network hosts.
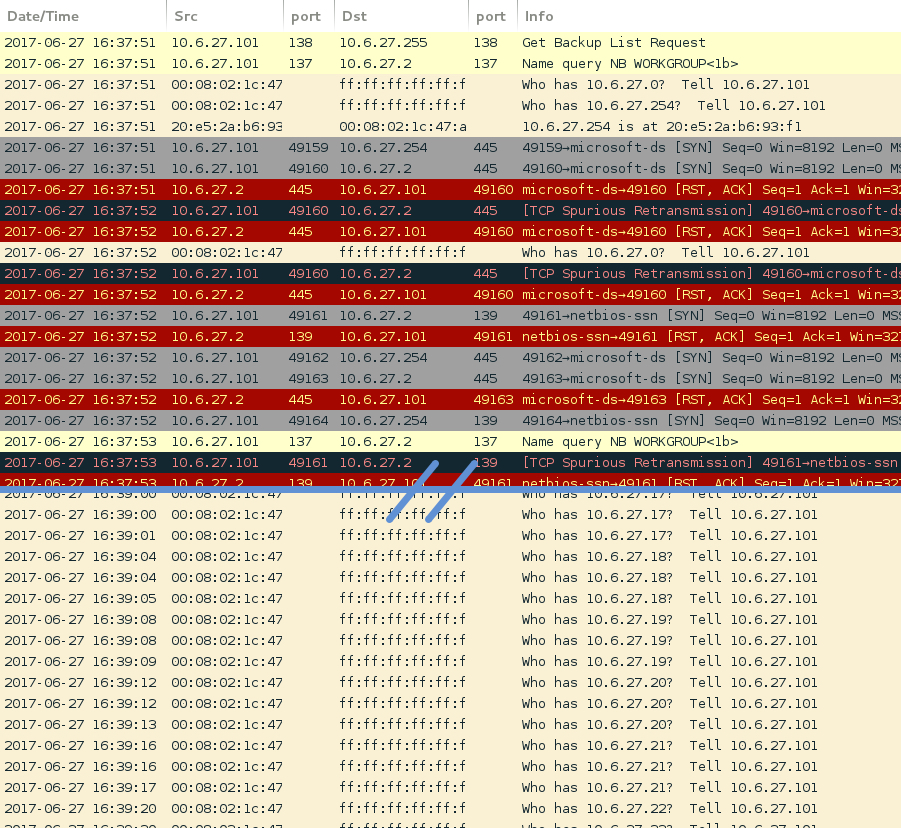
Shown above: Some of the traffic noted in my lab environment.
Keep in mind this is a new variant of Petya ransomware. I'm still seeing samples of the regular Petya ransomware submitted to places like VirusTotal and other locations. From what we can tell, those previous versions of Petya are not related to today's attacks.
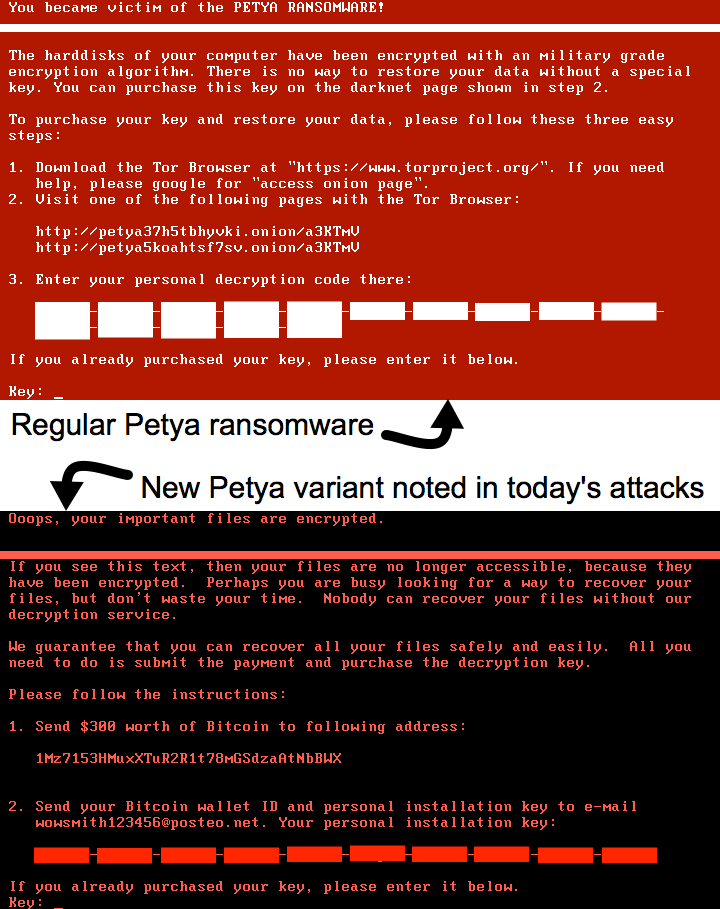
Shown above: Difference in ransomware notes between the old and new Petya variants.
New Petya variant ransom message
Ooops, your important files are encrypted.
If you see this text, then your files are no longer accessible, because they have been encrypted. Perhaps you are busy looking for a way to recover your files, but don't waste your time. Nobody can recover your files without our decryption service.
We guarantee that you can recover all your files safely and easily. All you need to do is submit the payment and purchase the decryption key.
Please follow the instructions:
1. Send $300 worth of Bitcoin to the following address:
1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX
2. Send your Bitcoin walled ID and personal installation key to e-mail wowsmith123456@posteo.net. Your personal installation key:
012345-6789ab-cdefgh-ijklmn-opqrst-uvwxyz-ABCDEF-GHIJKL-MNOPQR-STUVWX
If you already purchased your key, please enter it below.
Key:
More reports about the new Petya variant
- Bleeping Computer: WannaCry Déjà Vu: Petya Ransomware Outbreak Wreaking Havoc Across the Globe
- The Hacker News: Petya Ransomware Spreading Rapidly Worldwide, Just Like WannaCry
- Reuters: Petya ransomware virus is back amid cyber attack: Swiss agency
- Palo Alto Networks Blog: Threat Brief: Petya ransomware
Wide-scale Petya variant ransomware attack noted
Sent from a reader earlier today:
- Hearing some rumors that the company Merck is having a major virus outbreak with something new and their Europe networks are affected more than their US offices. Have you heard anything on this?
A quick check reveals that, apparently, another global ransomware attack is making the rounds today.
- Forbes: Another Massive Ransomware Outbreak Is Going Global Fast (2017-06-27 14:44 UTC)
- International Business Times: It's happening again: Huge ransomware attack on computer systems 'spreading worldwide' (updated 2017-06-27 14:23 UTC)
- The Verge: A new ransomware attack is devastating airlines, banks, and utilities across Europe (2017-06-27 14:01 UTC)
Initial reports indicate this is much like last month's WannaCry attack. According to the Verge article, today's ransomware appears to be a new Petya variant called Petyawrap. At this point, we see plenty of speculation on how the ransomware is spreading (everything from email to an EternalBlue-style SMB exploit), but nothing has been confirmed yet for the initial infection vector.
Alleged samples of this ransomware include the following SHA256 hashes:
- 027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745
- 8143d7d370015ccebcdaafce3f399156ffdf045ac8bedcc67bdffb1507be0b58
AlienVault Open Threat Exchange (OTX) is currently tracking this threat at:
We'll provide more information as it becomes available.
A Tale of Two Phishies
Introduction
Has anyone read A Tale of Two Cities, the 1859 novel by Charles Dickens? Or maybe seen one of the movie adaptations of it? It's set during the French Revolution, including the Reign of Terror, where revolutionary leaders used violence as an instrument of the government.
In the previous sentence, substitute "violence" with "email." Then substitute "government" with "criminals." Now what do you have? Email being used as an instrument of the criminals!
I know, I know... No real ties to Dickens' novel here. A pun for the title is, quite literarily, the best I could do.

Shown above: That's all I got--a somewhat clever title for this diary.
This diary briefly investigates two phishing emails. It's a "Tale of Two Phishies" I ran across on Monday 2017-06-26.
First example: an unsophisticated phish
The first example went to my blog's admin email address. It came from the mail server of an educational institution in Paraguay, possibly used as a relay from an IP address in South Africa. For email headers, you can only rely on the "Received:" header right before the message hits your mail server. Anything before that can be spoofed.
It's a pretty poor attempt, because this phishing message is very generic. I'm educated enough to realize this didn't come from my email provider. And the login page was obviously fake. Unfortunately, some people might actually be fooled by this.
The compromised website hosting a fake login page was quickly taken off line. You won't be able to replicate the traffic by the time you read this. It's already been submitted to PhishTank.
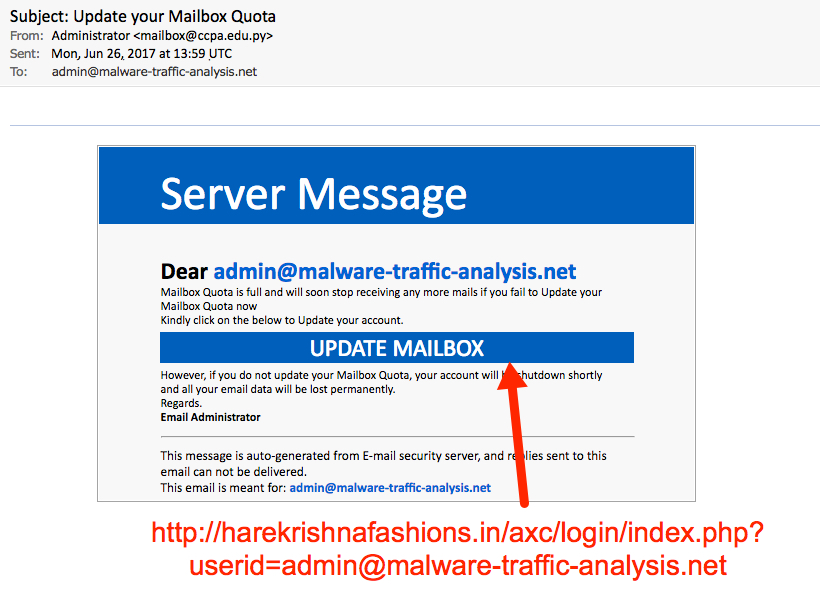
Shown above: The first phishing email.
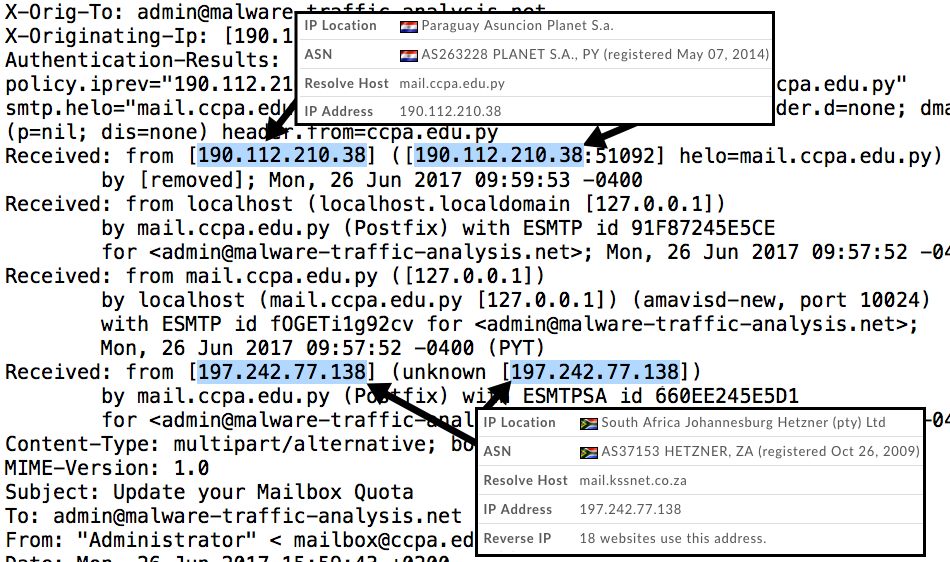
Shown above: Email headers from the first phishing email.
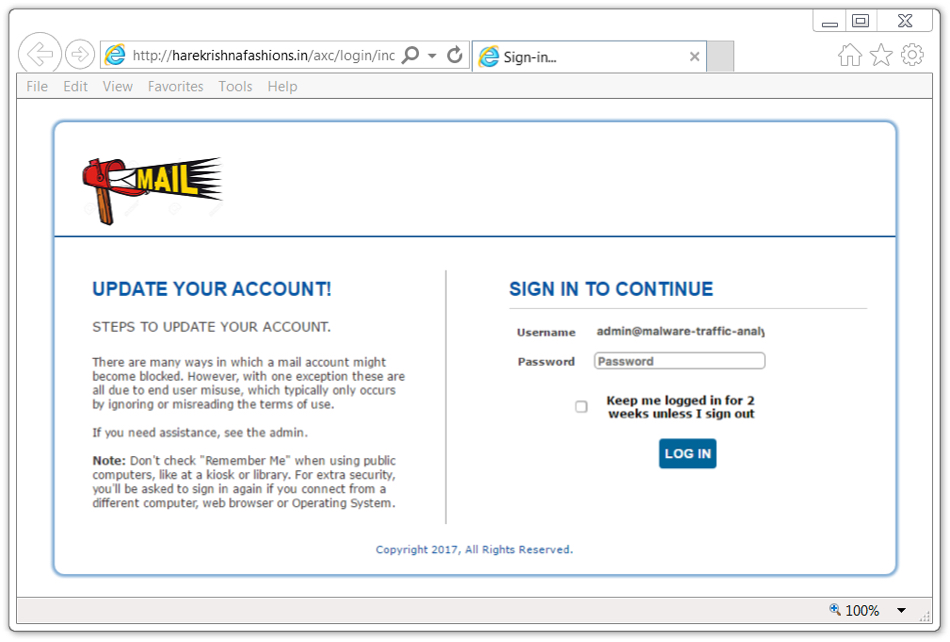
Shown above: The fake login page from link in the phishing email.
Second example: a slightly more complex phish
Every time I see a phishing message like this second example, I hope there's malware involved. But in this case, the email has a PDF attachment with a link to a fake Adobe login page.
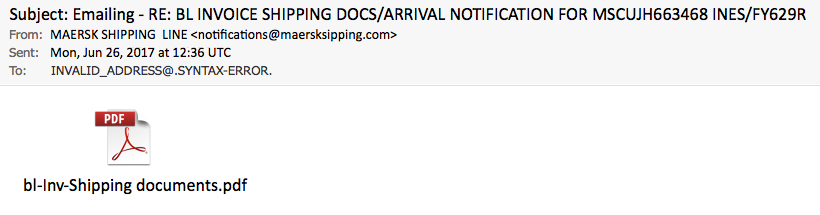
Shown above: The second phishing email.
Examining the PDF attachment, I quickly realized the criminals had made a mistake. They forgot to put .com at the end of the domain name in the URL from the PDF file. lillyforklifts should be lillyforklifts.com. I'd checked the URL early Monday morning with .com at the end of the domain name, and it worked. When I later checked again for this diary, it had already been taken down.
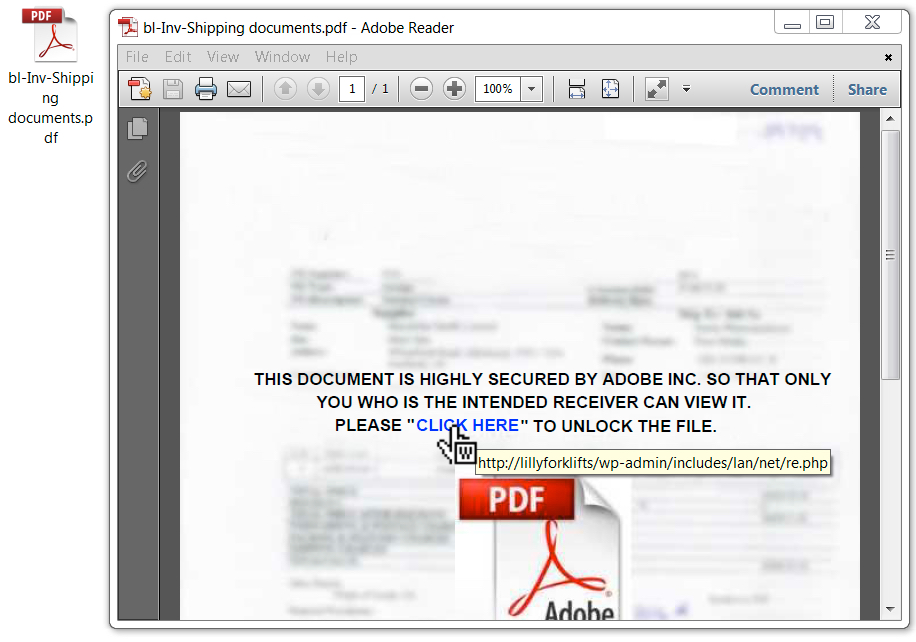
Shown above: PDF attachment from the second phishing email.
An elephant in the room
These types of phishes are what I call an "elephant in the room." That's an English-language metaphor. "Elephant in the room" represents an obvious issue that no one discusses or challenges. These types of phishing emails are very much an elephant in the room for a lot of security professionals. Why? Because we see far more serious issues during day-to-day operations in our networks. Many people (including me) feel we have better things to worry about.
But these types of phishing emails are constantly sent. They represent an on-going threat, however small they might be in comparison to other issues.
Messages with fake login pages for Netflix, Apple, email accounts, banks, and other organizations occur on a daily basis. For example, on Phishtank.com, the stats page indicates an average of 1,000 to 1,500 unique URLs were submitted on a daily basis during the past month. Stats for specific months show 58,556 unique URLs submitted in May 2017 alone.
Fortunately, various individuals on Twitter occasionally tweet about the fake login pages they find. Of course, many people also notify sites like PhishTank, scumware.org, and many other resources to fight this never-ending battle.
So today, it's open discussion on these phishing emails. Do you know anyone that's been fooled by these messages? Are there any good resources covering these phishing emails I forgot to mention? If so, please share your stories or information in the comments section below.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments