Yet Another Apple Phish and Some DNS Lessons Learned From It
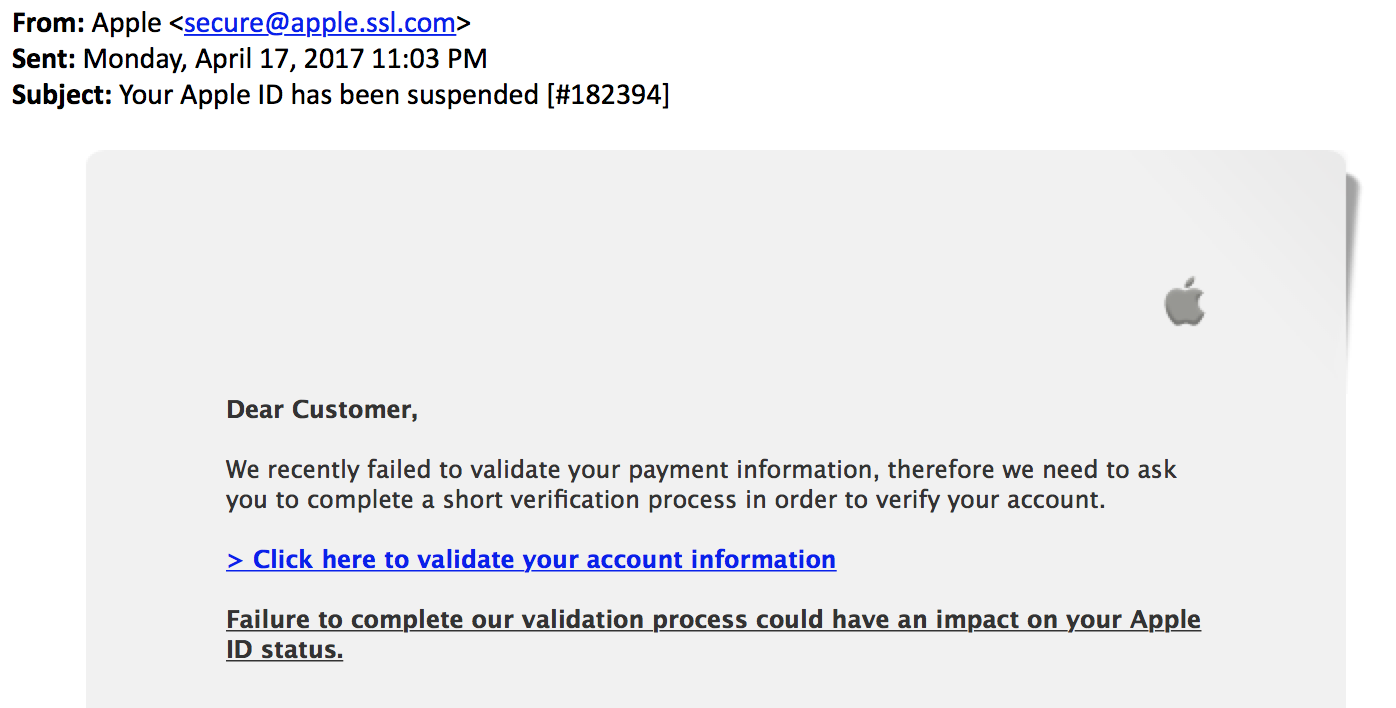
Our reader Charlie forwarded us a somewhat interesting Apple phish. Apple is a big phishing target, and the phish itself wasn't all that special. It does a reasonable good job emulating real Apple e-mails, but what is more interesting are the "From" address and the URL of the link:
The "From" address was set to apple.ssl.com . For the uninitiated, this may look like a valid Apple domain. But instead, it is a subdomain of "ssl.com". SSL.com is of course not the valid source of the e-mail. But why did this e-mail make it past SPF filters? ssl.com does define an SPF record:
v=spf1 ip4:144.76.245.218 ip4:199.102.137.146 include:amazonses.com include:mailanyone.net include:fusemail.net ~all
The record contains a common error: In the end, the "~" ahead of "all" indicates a "soft fail". In essence, this may short-out the SPF definition. There is also no DMARC record for this domain. The "~" is often added to prevent false positives, for example, if companies are afraid that they didn't capture all the mail servers sending e-mail on their behalf. While this may be a good idea initially, it should be removed later.
Next, the link leads to apple1-id.com. The domain is not associated with Apple. The web page is still up (but blocklisted), and provides a good copy of the genuine Apple login page.
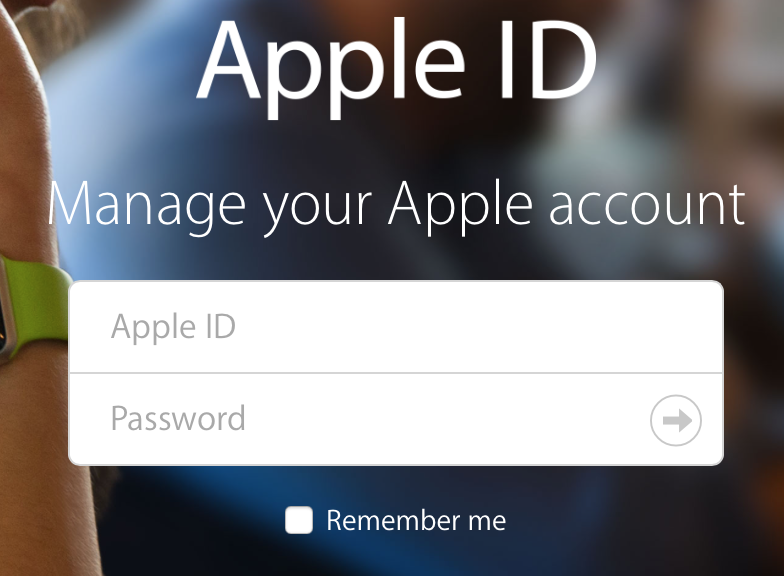
Interesting about this domain: It was registered back in January. So the bad guy put some work into this to avoid some "recently registered domain" filters.
So lessons learned:
- Make sure your SPF record ends with -all not ~all (subtle but important)
- When hunting for bad domains, details matter and the registration date may not be enough to find malicious domains.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
STI|Twitter|


Comments