CRA Maldoc Analysis
I took a look at Guy's diary entry from yesterday. This malicious document contains macros that launch a PowerShell command.
Like it is often the case with such documents, the PowerShell command will download and execute an executable: MD5 e2d5d1bf5d69a942d99c8ea45fe28ac2.
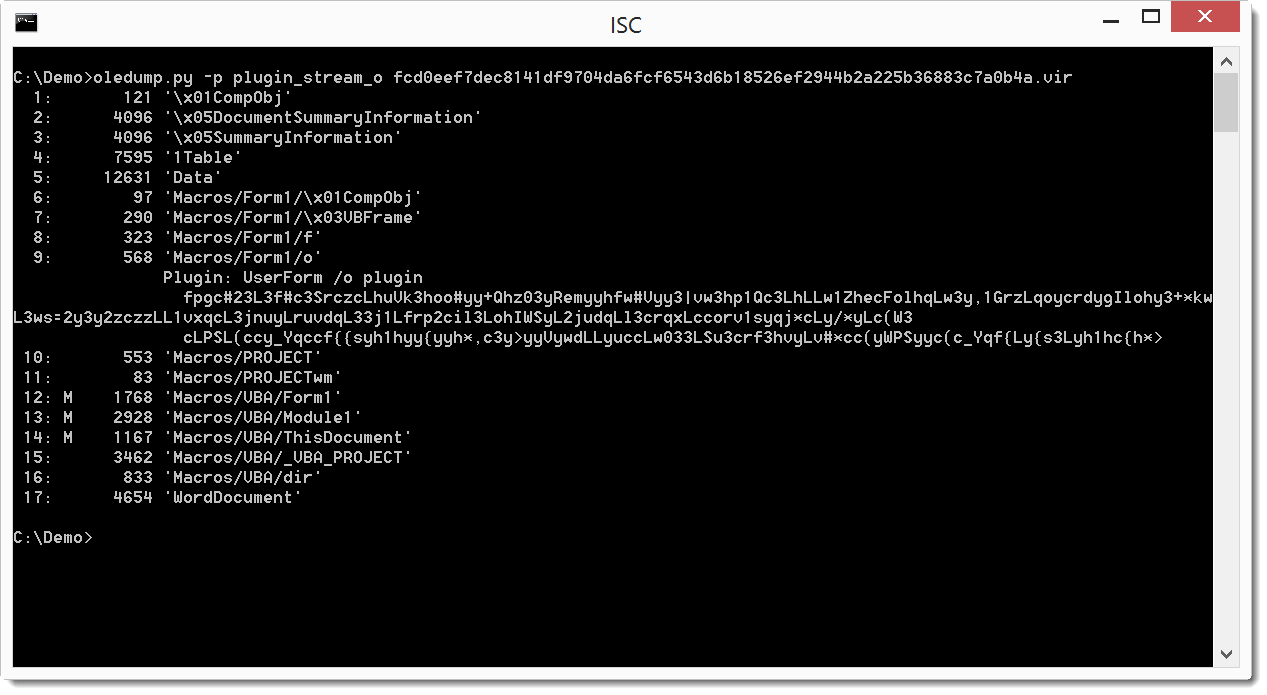
The PowerShell command is encoded and stored in Form1 objects:
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
It is Tax Season - Watch out for Suspicious Attachment
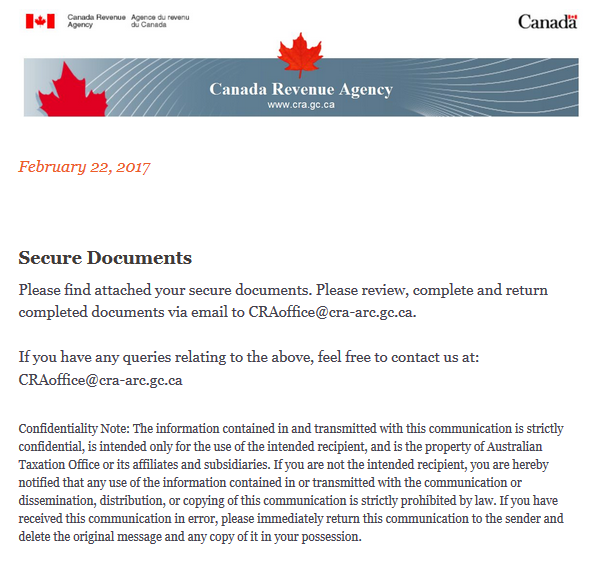
This week I received an email looking very realistic with a Word document that made it through the AV gateway from the Canadian Revenue Agency, it is tax season after all and everyone must be extra vigilant. The Word document got me curious since it is from CRA and named SecureDoc.doc, after all, when you hear SecureDoc you think of WinMagic[1], in this case, it has no relation.
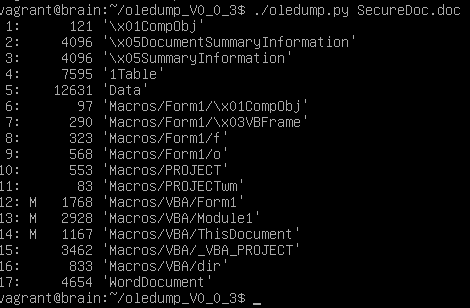
I examined a copy of the file using Didier Stevens oledump.py[2] to find out if there was anything I could get from this file. I dumped the content and saw it contains 3 macros (identified by the M).
I checked each of the macro sections 12, 13 & 14 and 13 displayed strange results similar that the results of this sandbox[3].
And last I check for and PE files in the document with no avail. The file is malicious and is detect by 23/55 AV engine on Virustotal.
[1] https://www.winmagic.com
[2] https://blog.didierstevens.com/2014/12/17/introducing-oledump-py/
[3] https://www.hybrid-analysis.com/sample/caec8c4e5cfbc59b34bd64b87cec0f10bcfecee11a79f05d9a2e37c26230ca9d?environmentId=100
[4] https://www.virustotal.com/en/file/fcd0eef7dec8141df9704da6fcf6543d6b18526ef2944b2a225b36883c7a0b4a/analysis/1487945938/
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu

.PNG)


Comments