Brazilian malspam sends Autoit-based malware
Introduction
Nothing really exciting this week, so let's review malicious spam (malspam) we received at our ISC handers email distro. The message is in Portuguese, and it claims to be from Detran. Detran is an abbreviation for Departamento Estadual de Trânsito, an institution responsible for supervision of ground vehicles in Brazil. The malspam concerns a ticket for running a red light, but the message is ultimately a vehicle for transporting AutoIt-based malware.
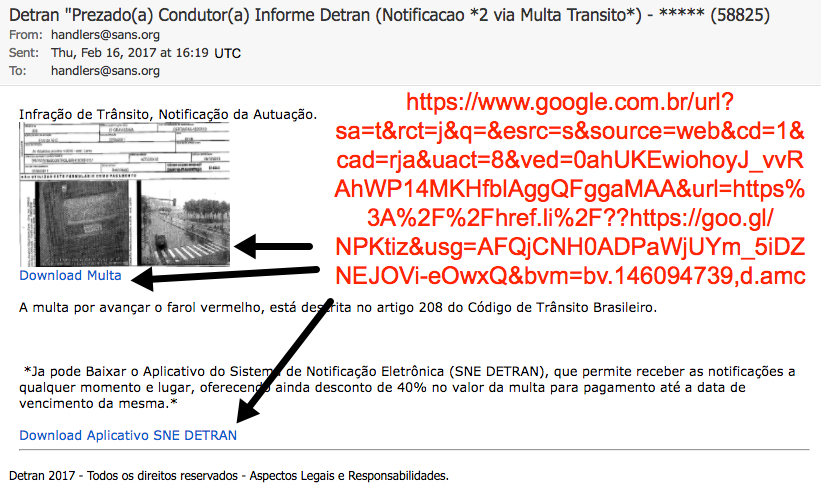
Shown above: Brazilian malspam disguised as a message from Detran.
I received a zip file from a link in the email, and it easily infected a Windows computer on Friday 2017-02-17. Let's take a closer look at this infection.

Shown above: Flowchart for the infection.
Translation
Original message text in Portuguese:
Subject: Detran "Prezado(a) Condutor(a) Informe Detran (Notificacao *2 via Multa Transito*) - ***** (58825)
Infração de Trânsito, Notificação da Autuação.
A multa por avançar o farol vermelho, está descrita no artigo 208 do Código de Trânsito Brasileiro.
Ja pode Baixar o Aplicativo do Sistema de Notificação Eletrônica (SNE DETRAN), que permite receber as notificações a qualquer momento e lugar, oferecendo ainda desconto de 40% no valor da multa para pagamento até a data de vencimento da mesma.
Detran 2017 - Todos os direitos reservados - Aspectos Legais e Responsabilidades.
Google translation:
Subject: Detran "Dear Conductor Report Detran (Notification * 2 via Fine Traffic *) - ***** (58825)
Traffic Infringement, Notification of the Assessment.
The fine for advancing the red light is described in article 208 of the Brazilian Traffic Code.
You can download the application of the Electronic Notification System (SNE DETRAN), which allows you to receive notifications at any time and place, also offering a 40% discount on the fine for payment until the expiration date of the same.
Detran 2017 - All rights reserved - Legal Aspects and Responsibilities.
The download
Clicking on the link presented a zip archive. I tried several times and saw at least seven different file names for the zip archive. They all contained the a .js file inside with the same file hash, regardless of the actual file name.
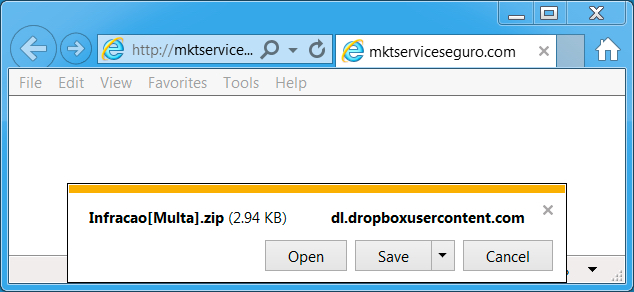
Shown above: What I got after clicking the link.
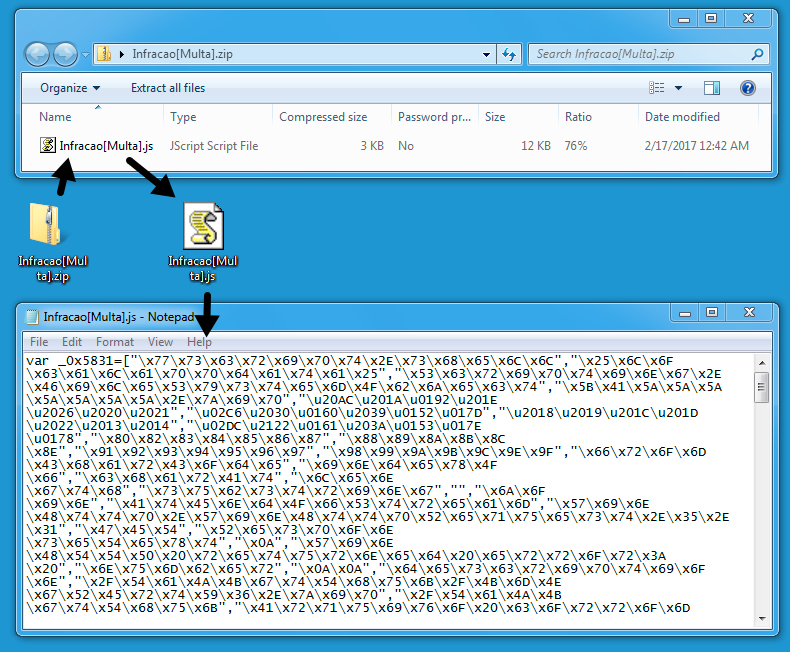
Shown above: The zip archive contained a .js file.
I emailed abuse@dropbox.com to notify them of the URLs I found. The following HTTPS URLs over TCP port 443 provided the initial zip archive:
- www.dropbox.com - GET /s/m9vu2mwquasfhr3/%5BAvancar-Sinal%5D.zip?dl=1
- www.dropbox.com - GET /s/7dwinqclpdxt6q8/Infracao%5BMulta%5D.zip?dl=1
- www.dropbox.com - GET /s/b9u8rdqigk5ycnr/INFR-SG%5BMulta%5D.zip?dl=1
- www.dropbox.com - GET /s/lpbxa75s9vutq6r/FDWS%5BInfracao%5D.zip?dl=1
- www.dropbox.com - GET /s/d3k0u4ircpyt861/Informe%7BMulta-Recebida%7D.zip?dl=1
- www.dropbox.com - GET /s/7ann3m0bno2pe6x/FLSFW%5BMulta%5D.zip?dl=1
- www.dropbox.com - GET /s/e8yqpvl8wb0jpgt/RD793614%5BNotificacao-Multa%5D.zip?dl=1
Traffic
Because the Dropbox URLs were sent encrypted over HTTPS, I didn't see any alerts when downloading the zip archive. After opening the zip archive and double-clicking the enclosed .js file, my Windows computer became infected.
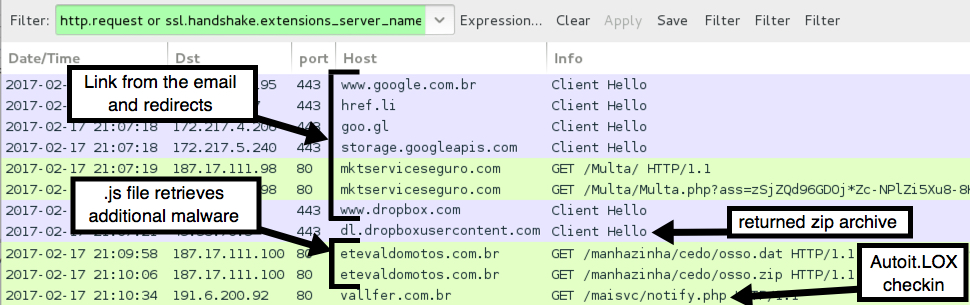
Shown above: Traffic of the infection filtered in Wireshark.
The follow-up malware was sent as an 7.9 MB ASCII text file that represented hexadecimal characters for an executable binary.
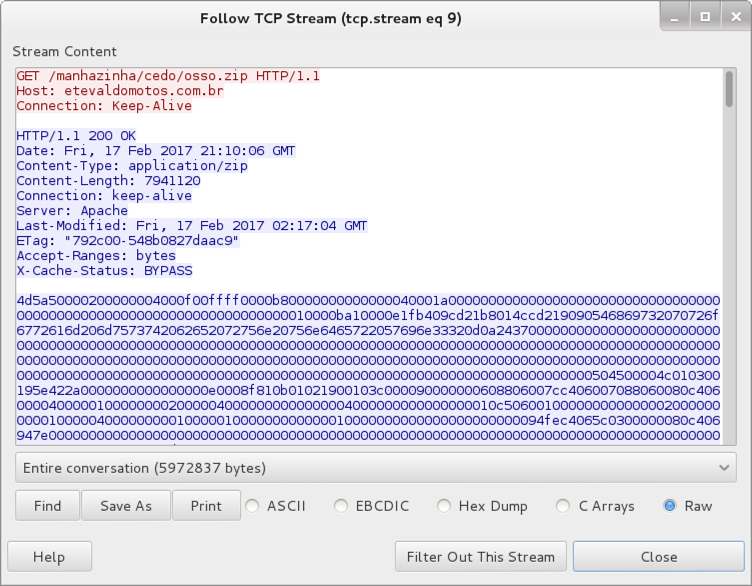
Shown above: The follow-up malware sent as ASCII text.
The 7.9 MB of ASCII text was saved to the Windows host as C:\Users[username]\AppData\Local\TaJKgtThuk\KmNgRErtY6.zip. That fake .zip file was still ASCII text. It was then converted to a 3.97 MB binary. The binary was as an .exe saved to the local host, and it was made resident through a Windows registry update.
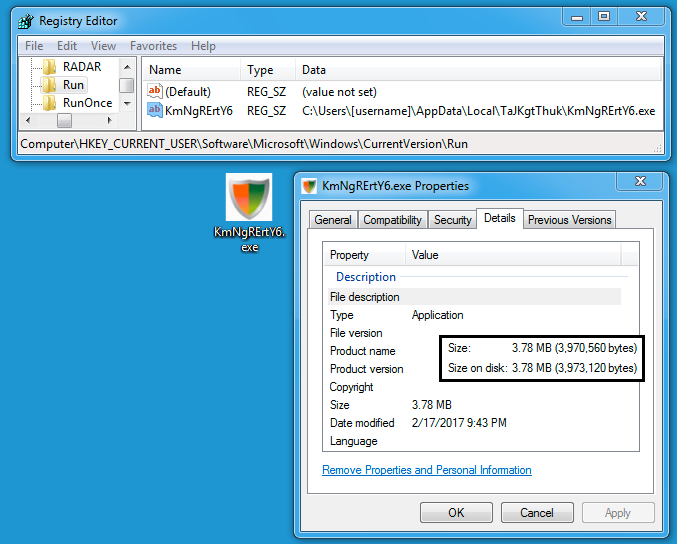
Shown above: Follow-up malware saved to the host and made persistent.
The ASCII text (that fake zip file) was deleted during the infection process. However, I grabbed a copy before it deleted itself, so I could double-check. I took that 7.9 MB of ASCII text, copied it into a hex editor, and saved the result as an .exe file. It had the same file hash as the .exe from the infected Windows host.
I only saw one alert on the traffic. It was an ETPRO rule for Autoit.LOX checkin. The alert is an older rule that originally appeared back in August 2014 [1].
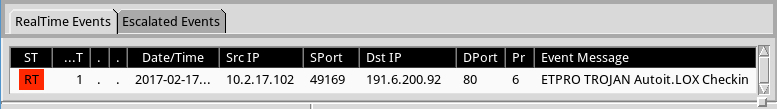
Shown above: Alerts on the traffic using Security Onion with Suricata and the ETPRO ruleset.
Indicators of Compromise (IOCs)
The following are malicious URLs associated with this infection:
- 187.17.111.98 port 80 - mktserviceseguro.com - GET /Multa/
- 187.17.111.98 port 80 - mktserviceseguro.com - GET /Multa/Multa.php?ass=[long string of characters]
- 187.17.111.100 port 80 - etevaldomotos.com.br - GET /manhazinha/cedo/osso.dat
- 187.17.111.100 port 80 - etevaldomotos.com.br - GET /manhazinha/cedo/osso.zip
- 191.6.200.92 port 80 - vallfer.com.br - GET /maisvc/notify.php
The extracted .js file:
- SHA256 hash: ed8d7c4201c4e2a670e3418242cc02f9509e02e2e580f1b77a9ccb6e0455dc80
- File name: Infracao[Multa].js (and various other file names)
- File description: .js file extracted from zip archives associated with this malspam
The followup .exe malware:
- SHA256 hash: da9172f1e1d81c2a9300a5028bc419ea8d43518bcdb61b022180646aa2539c68
- File location: C:\Users\[username]\AppData\Local\TaJKgtThuk\KmNgRErtY6.exe
- File description: Follow-up malware downloaded by .js file
Final words
This malspam wasn't well-targeted. But our ISC handler email distro occasionally receives this type of malspam, so I like to share when I can. As usual, my lab environment is designed to be vulnerable to such malware. By the time you read this, some of the infrastructure for this campaign may already be blocked or taken down.
I don't think many people will become infected by this malspam, but it's always interesting to see what the criminals are putting out there.
From what I understand, AutoIt is a scripting language that's not inherently malicious. However, it provides a convenient environment that criminals can use to quickly develop malware. A VirusTotal search for comments tagged #autoit reveals several recent examples of AutoIt-based malware. A Google search for "autoit malware" returns several articles on the subject.
Pcap and malware for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] https://www.proofpoint.com/us/daily-ruleset-update-summary-2014-08-05


Comments