VBA Shellcode and Windows 10
I tested the process replacement maldoc (Hancitor Maldoc Bypasses Application Whitelisting) on Windows 10 and Word 2016. It's not blocked.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
NVISO
2016-11-18 example of KaiXin EK activity
Introduction
KaiXin exploit kit (EK) was first identified in August 2012 by Kahu Security [1], and it received some press from security-related blogs later that year [2, 3, 4]. Within the past year or so, Jack at malwarefor.me and I have posted our analysis of a few KaiXin EK traffic examples [5, 6, 7, 8, 9], and in March 2016 I wrote an ISC diary about this EK [10]. A May 2016 blog from Palo Alto Networks associated some instances of KaiXin EK with a KRBanker trojan that targeted online banking users [11].
Since that time, I've rarely found KaiXin EK. Every once in a while, I'd sometimes find indicators, but I was never able to generate any traffic. Fortunately, someone recently informed me of an active URL, and I retrieved some good examples of KaiXin EK.
Of note, I had to use an older Windows 7 host with Internet Explorer (IE) 8 as the web browser. I was unable to generate any EK traffic from the initial URL if I used Windows 7 with IE 9 or newer.
Today's diary examines these examples of KaiXin EK infection traffic.
The EK infection
I tried a variety of configurations (all using IE 8) in order to get as many exploits as possible. An older Windows host with Java 6 runtime environment update 22 gave me a Java exploit. Newer Windows hosts generated different Flash exploits. The below images show 3 examples of the traffic from the initial URL.
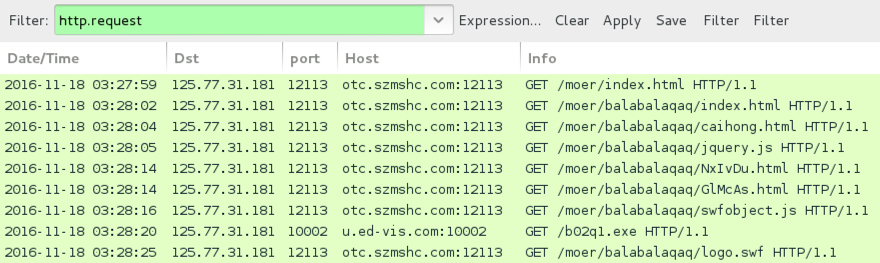
Shown above: First run for the KaiXin EK infection traffic in Wireshark.
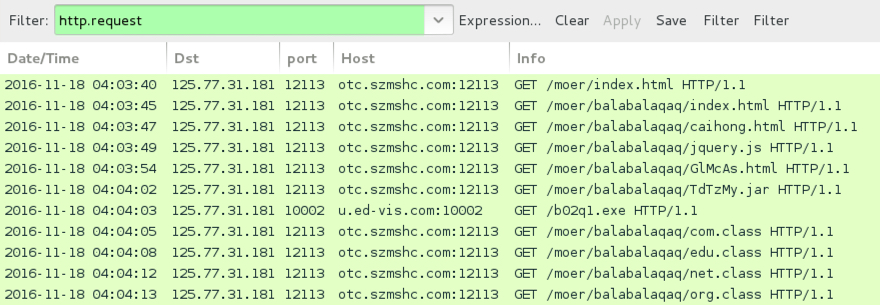
Shown above: Second run for the KaiXin EK infection traffic in Wireshark.
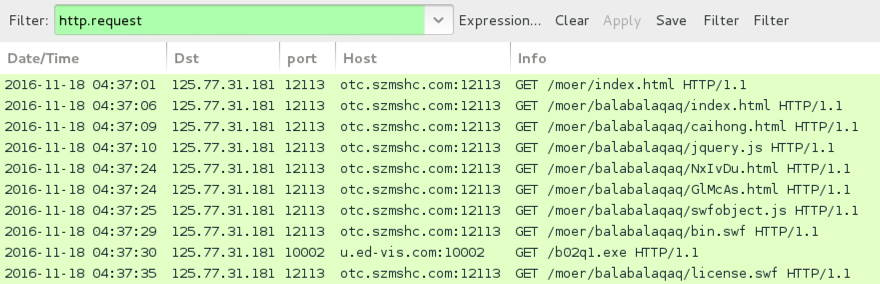
Shown above: Third run for the KaiXin EK infection traffic in Wireshark.
The initial URL appears to be a gate. This gate checks for security products from Chinese-based companies like Kingsoft, 360 and Tencent.
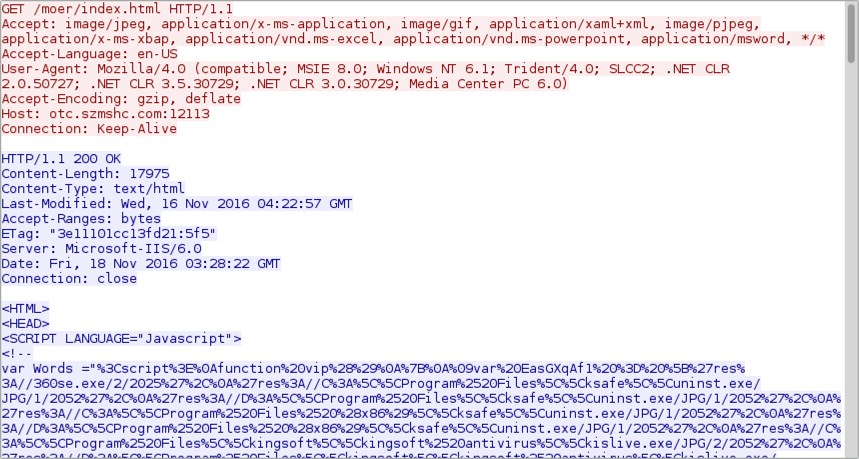
Shown above: HTTP request and response for the initial URL.
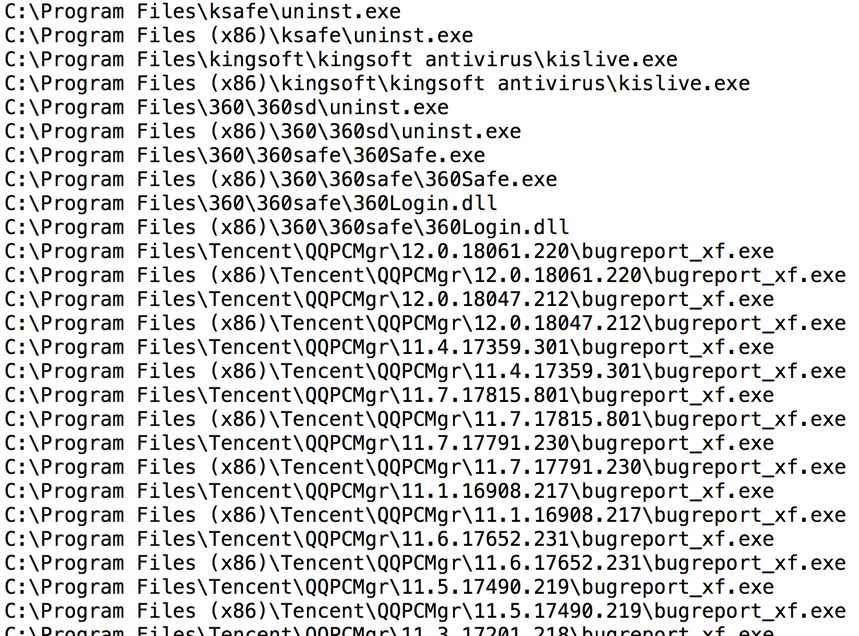
Shown above: Some security products referenced in HTML from the first HTTP response.
Using tcpreplay on Security Onion, I found several alerts related to KaiXin EK if I tried Suricata with the Emerging Threats signature set.
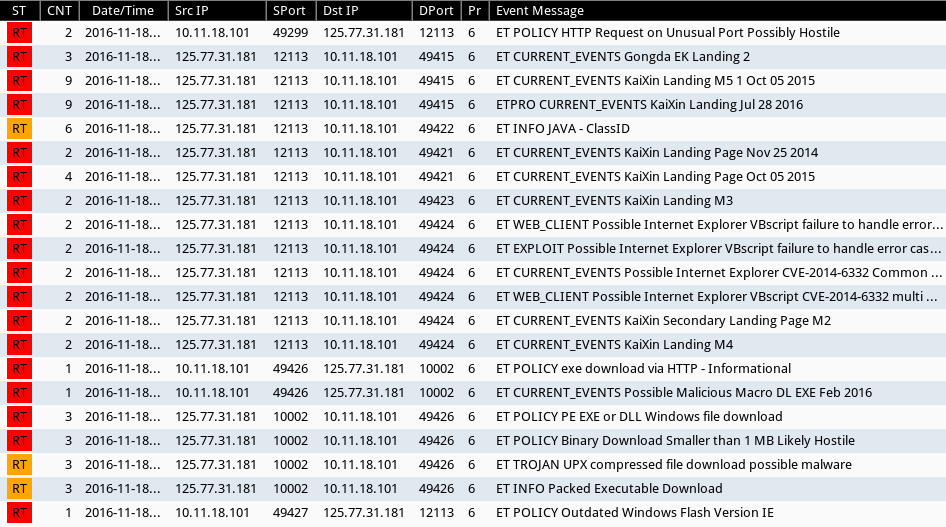
Shown above: Alerts on the traffic from the first run.
The payload didn't execute properly for any of my infections. During each infection, a VBS file appeared in the user's AppData\Local\Temp directory with a random name of 5 alphabetic characters. An example of the file name and path on a Windows 7 host follows:
- C:\Users\[username]\AppData\Local\Temp\CZGYO.vbs
I ran the payload through publicly-available sandboxes at malwr.com and hybrid-analysis.com to get the post-infection traffic.
The payload
Today's KaiXin EK payload is a 8,192 byte executable that acts as a file downloader. It appears to download another piece of malware about 2 MB in size. I was unable to identify the follow-up malware based on the HTTP traffic it generated. The follow-up malware calls back to a domain registered to a Chinese individual or organization.
All activity for KaiXin EK and the post-infection traffic was on 125.77.31.181, a Chinese IP address.
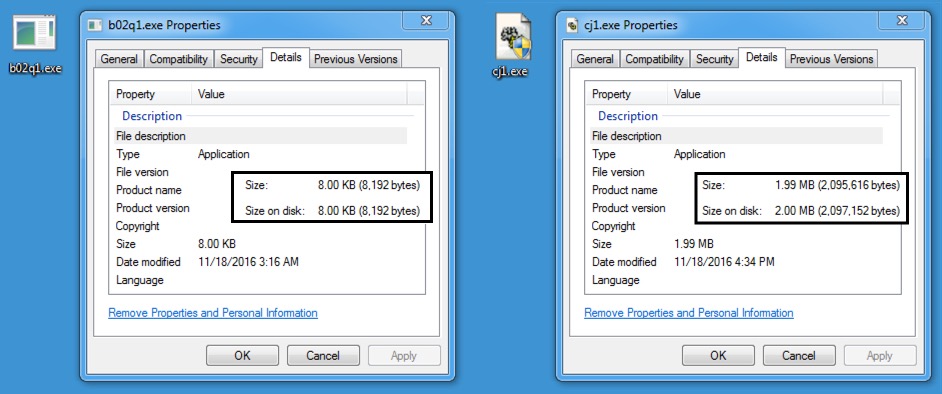
Shown above: The malware payload and follow-up malware.
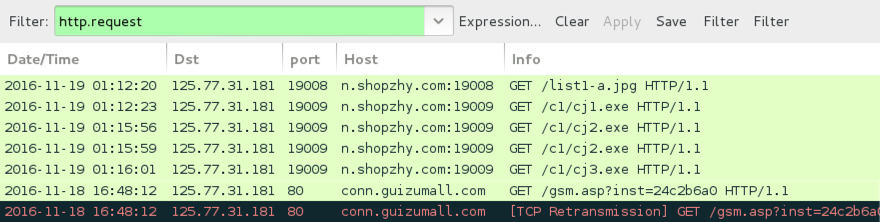
Show above: Traffic generated by the KaiXin EK payload and follow-up malware in a public sandbox.
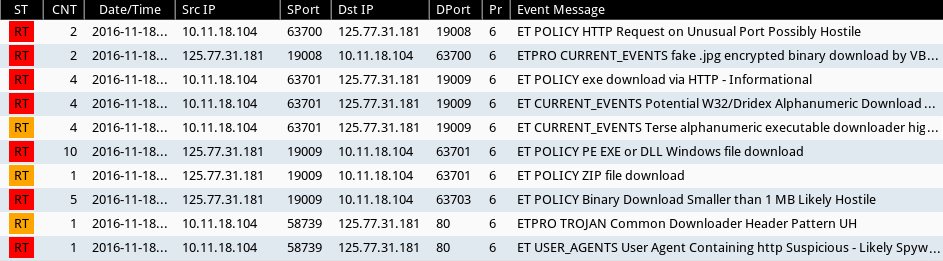
Shown above: Alerts for the post-infection traffic on Security Onion using Sguil with Suricata and the Emerging Threats Pro signature set.
Indicators of Compromise (IOCs)
The following are IP addresses, TCP ports, and domain names associated with today's infection:
- 125.77.31.181 port 12113 - otc.szmshc.com:12113 - KaiXin EK
- 125.77.31.181 port 10002 - u.ed-vis.com:10002 - KaiXin EK sends payload (file downloader)
- 125.77.31.181 port 19008 - n.shopzhy.com:19008 - Post-infection traffic from KaiXin EK payload
- 125.77.31.181 port 80 - conn.guizumall.com - Post-infection traffic from follow-up malware
The following are SHA256 hashes, file names, and descriptions of the EK payload and follow-up malware:
- SHA256 hash: 21bfb09e9c67c69ff3041b48494b093bce8acb57ee0e9e0fe5da737561064a7b
- File name: b02q1.exe
- File description: Payload (a downloader) sent by KaiXin EK (8,192 bytes)
- SHA256 hash: e4d9c9b5400436204bbd1510f73e6e76cc970b844605f4b1918bac5c2b74b384
- File name: cj1.exe
- File description: Follow-up malware retrieved by the KaiXin EK payload (2,095,616 bytes)
Final words
From the beginning, KaiXin EK has been described as a Chinese EK. I've seen it in traffic associated with China, Japan, Korea, and possibly some nations in Southeast Asia. It usually doesn't make the list with other more advanced EKs, and the exploits used in KaiXin EK seem awfully outdated.
However, the actors and campaigns using KaiXin EK remain a threat.
People can protect themselves by following best security practices like keeping their computers up-to-date with the latest version of Windows, web browsers, and browser-associated applications (like Java, Flash, etc.).
Pcaps, malware, and artifacts associated with this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References
[1] http://www.kahusecurity.com/2012/new-chinese-exploit-pack/
[2] http://eromang.zataz.com/2012/12/05/kaixin-exploit-kit-evolutions/
[3] https://websiteanalystsresource.wordpress.com/2012/08/10/exploring-the-kaixin-exploit-kit/
[4] http://ondailybasis.com/blog/2012/11/01/kaixin-exploit-pack-is-back-part-1/
[5] http://www.malware-traffic-analysis.net/2015/01/03/index.html
[6] http://www.malware-traffic-analysis.net/2015/01/31/index.html
[7] http://malwarefor.me/2015-09-20-kaixin-ek-from-korean-news-website/
[8] http://www.malware-traffic-analysis.net/2016/03/22/index.html
[9] http://www.malware-traffic-analysis.net/2016/05/31/index2.html
[10] https://isc.sans.edu/forums/diary/Recent+example+of+KaiXin+exploit+kit/20827/
[11] http://researchcenter.paloaltonetworks.com/2016/05/unit42-krbanker-targets-south-korea-through-adware-and-exploit-kits-2/


Comments