Critical Cisco ASA IKEv1/v2 Vulnerability. Active Scanning Detected
Cisco released an advisory revealing a critical vulnerability in Cisco's ASA software. Devices are vulnerable if they are configured to terminate IKEv1 or IKEv2 VPN sessions. (CVE-2016-1287)
[Update] Also see this writeup with LOTS of details https://blog.exodusintel.com/2016/02/10/firewall-hacking/
The vulnerability can lead to a complete compromise of the system. A single UDP packet may suffice to exploit the vulnerability, but no details about the nature of the vulnerability have been made public yet, but it is recommended to patch SOON. The exploit would likely arrive over UDP port 500 or possibly 4500.
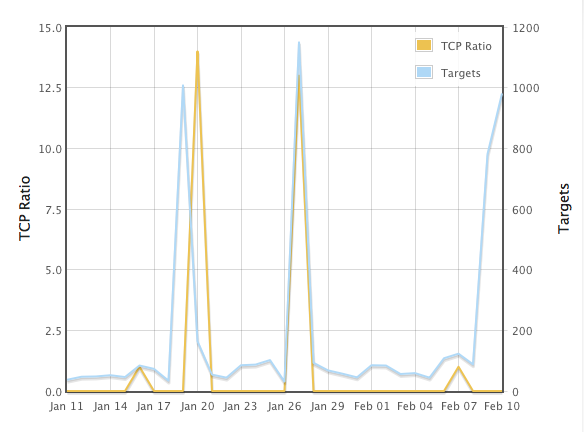
We are seeing a LARGE INCREASE in port 500/UDP traffic (see https://isc.sans.edu/port.html?port=500 and select TCP Ratio for the left Y axis. earlier spikes affecting this port were mostly TCP)
To test if your device is vulnerable, check the running crypto maps:
ciscoasa# show running-config crypto map | include interface
A product is vulnerable if a crypto map is returned.
There is no workaround, but Cisco has released patched firmware for affected devices.
[1] https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160210-asa-ike
Beta Testers Wanted: Use a Raspberry Pi as a DShield Sensor
I am currently working on an easy way to turn a Raspberry Pi into a DShield sensor. If you would like to, you can try the current "beta version" of the software. Feedback is very much appreciated. To get started:
- Install Raspbian Jessie on your Pi https://www.raspberrypi.org/downloads/raspbian/
- change the default password (VERY IMPORTANT!!!)
- claim the entire SD card for Raspbian (by default, you only use 4GB, and space may be tight). the easiest way to do this is to run sudo raspi-config and select "expand roofs"
- you will need the e-mail address, the numeric userid and the "authkey" for your ISC/DShield account. You can retrieve it here: https://isc.sans.edu/myaccount.html
- Download the software from github: git clone https://github.com/DShield-ISC/dshield.git
- run the install script sudo dshield/bin/install.sh
- enjoy (hopefully... and please let me know what works/doesn't work, if possible by entering an "issue" with github https://github.com/DShield-ISC/dshield/issues ) .
Important: The install script will move the SSH server to port 12222. So the next time you connect after a reboot, you will need to connect to that port (ssh -p 12222 pi@[your pi IP]) . The reason we do this is to keep port 22 free for an ssh honeypot.
In order to make the Raspberry Pi a useful sensor, you need to expose it to network traffic. For example, you could use your router's "DMZ" feature to expose the system. Other Raspbian versions may work, and if you do have one, by all means test it and let me know how it goes.


Comments