Extracting pcap from memory
I have talked many times about memory forensics and how useful its. In this diary I am going to talk about how to extract a pcap file from a memory image using bulk_extractor.
Of course when we are extracting a pcap file from a memory image we are going to not have everything but there will be some remanence that can help in our investigation
“bulk_extractor is a computer forensics tool that scans a disk image, a file, or a directory of files and extracts useful information without parsing the file system or file system structures. The results can be easily inspected, parsed, or processed with automated tools. bulk_extractor also creates a histograms of features that it finds, as features that are more common tend to be more important. The program can be used for law enforcement, defense, intelligence, and cyber-investigation applications.”[1]
Bulk_extractor can be obtained from http://digitalcorpora.org/downloads/bulk_extractor/
For this diary I have run netcat on my linux vm
|
nc -l –p 80 |
Then I used telnet client from my window machine to communicate to netcat over port 80.
|
telnet 192.168.8.101 80 |
Then I captured the memory of my windows machine using Dumpit[2].
since I am interested in extracting the pcap from the memory image only ,I will disable all the scanners using –x all option and enable the net scanner only using –e net.
|
bulk_extractor -x all -e net -o Win8bulk/ Win8-64bit.raw |
-o specifies output directory.
Now let’s check the Win8bul directory
|
ls Win8bulk/ alerts.txt ether.txt ip.txt report.xml ether_histogram.txt ip_histogram.txt packets.pcap |
Here is a brief explanations of the above files
ether.txt -- Ethernet MAC addresses found through IP packet carving of swap files and compressed system hibernation files and file fragments.
ip.txt -- IP addresses found through IP packet carving.
ether_histogram. witll show the histogram of Ethernet Mac addresses
ip_histogram will show the histogram of the ip addresses.
packet.pcap is The file packets.pcap is a pcap file made from carved packet
now let check the pcap file to see if it contain the sessions the I have tested
|
tcpdump -nn -r Win8bulk/packets.pcap 'ip host 192.168.8.101 and tcp' |
And here is the output
|
00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [.], ack 422809692, win 64, length 0 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 0:1, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 1:2, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 2:3, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 3:4, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 4:5, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 5:6, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 6:7, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 7:8, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [S], seq 2574360603, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 |
As we can see the pcap is missing at least the three way handshaking packets.
But let see what we can get from these packets in Wireshark
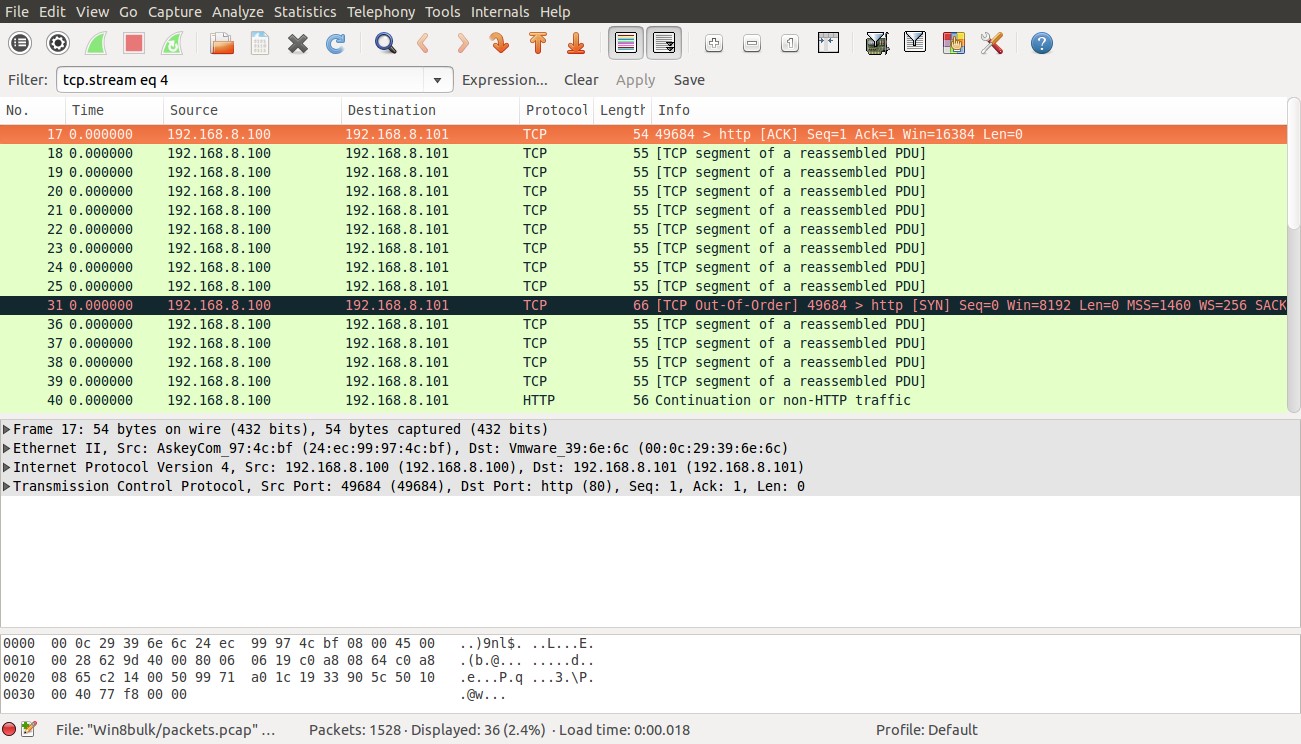
Now let’s check what we can get with “follow tcp stream”
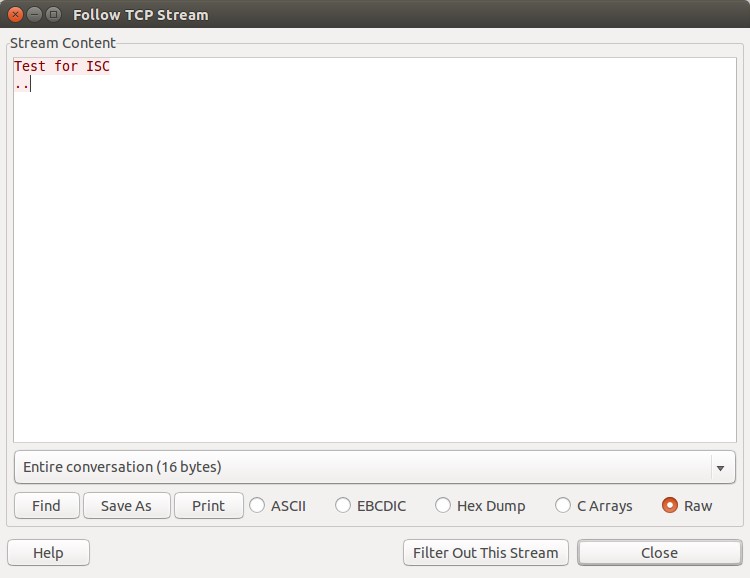
And that’s what I have typed during the test connection


Comments