You Have Got a New Audio Message - Guest Diary by Pasquale Stirparo
[Guest Diary by Pasquale Stirparo]
Few weeks ago we witnessed a quite significant wave of email carrying with them a zip file containing an executable.
The only common thing among all the emails was that the sender name (not the sender email address) appeared to be "Whatsapp" or "Facebook" all the times, while the subject was always referring, in different languages (and sometimes terms), that "You got a new audio (or video) message". Some of the subjects I saw are:
- Subject: Sie haben einen Videohinweis erhalten!
- Subject: Ein Hörbeleg ist versäumt worden!
- Subject: Di recente, hai raccolto un avviso video
- Subject: Du hast eine Hörakte.
- Subject: You recently got an audible message!
- Subject: Ein akustisches Dokument wurde bloß übergetragen
- …
On the sample side, the extracted exe has usually the name of a person like jack.exe or brent.exe and the malware seems to be a variant of Nivdort [1](also named Bayrob in some reports), which once installed it allows backdoor access. This malware family is not new (it has been around since April 2013 [2]), but anti-virus tools were apparently lagging behind this last Nidvort email wave, and most did not provide realtime protection. However, once installed it should be still relatively easy to detect, here some indicators:
- Once executed, it creates a random folder under C:\, where it drops several executables, also them with random alphanumeric names, e.g.:
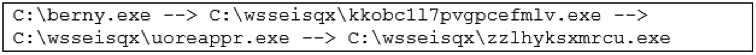
- It then tries to resolve about 40/50 domain names (on average), >90% of which appeared to be not registered. If not yet done, you may want to have in place some alerts when one of your clients fails so many DNS requests in a row
- When connecting to the C2, it performs HTTP requests to /index.php
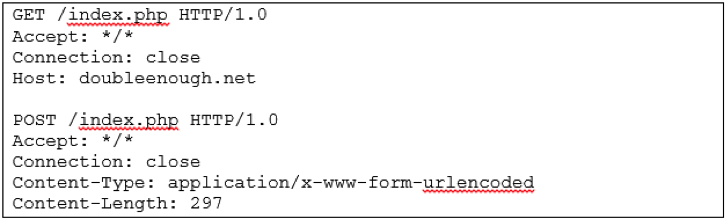
- Do not get fooled by the eventual "404" reply you may see in your logs. The 404 reply comes with a body, which turns out to be in json format and containing Base64 encoded instructions on where to connect for the next stage
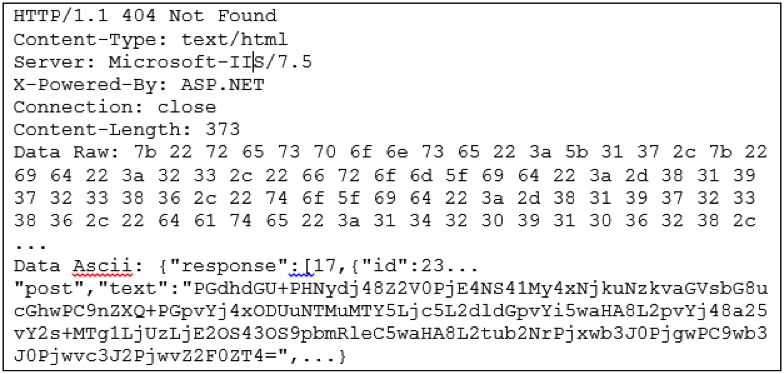
the Base64 encoded value contains the information for the next address to contact via POST request, in the previous case we can easily decode it
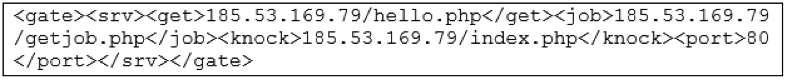
Incidentally this very same response, as well as the server IP to contact, appears also in the report of "f0xy" malware, a CPU miner uncovered last year by WebSense [3]. However, the two samples are completely different.
- The malware will later upload some information about the files dropped and the email address of the victim, again base64 encoded.
In case any of you may want to try to analyze the sample, be aware that the binary will also implement some anti-debugging techniques as detected also by running Yara against the Yara Rules from the official repository [4]
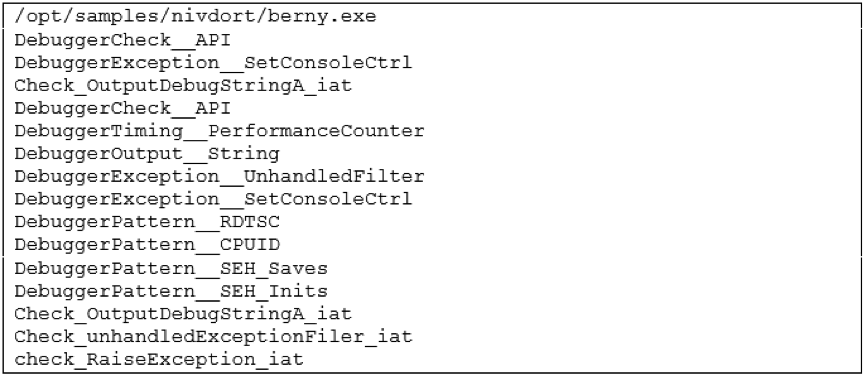
I'm not sharing MD5 of the samples collected since all of them are different and would not be a much actionable information. However, you can find below a list of C2 domains which the samples tried to contact. Looking at them one may think that Nivdort does not use any DGA, instead it does use a particular DGA based on a dictionary, which makes the domains not looking random and able to bypass many DGA checks used by some filters. If you are interested to know more about it, there is a nice write up by NeutralizeThreat [5] who reverse engineered the sample and described its functionalities in details.
Happy Hunting,
Pasquale
C2 Domains:
againstangry.net againstarticle.net againstdried.net againstfifteen.net betterbehind.net betterbroad.net betterbutter.net betterunderstand.net breadbehind.net breadbroad.net breadbutter.net breadunderstand.net captainangry.net captainarticle.net captainbehind.net captaindried.net captainfifteen.net decideangry.net decidearticle.net decidedried.net decidefifteen.net doubtangry.net doubtarticle.net doubtdried.net doubtfifteen.net electricbehind.net electricbroad.net electricbutter.net electricdried.net electricunderstand.net flierbehind.net flierbroad.net flierbutter.net flierunderstand.net gatherbehind.net gatherbroad.net gatherbutter.net gatherunderstand.net largeangry.net largearticle.net largebutter.net largedried.net largefifteen.net nightangry.net nightarticle.net nightdried.net nightfifteen.net quietbehind.net quietbroad.net quietbutter.net quietunderstand.net recordbehind.net recordbroad.net recordbutter.net recorddried.net recordunderstand.net seasonbehind.net seasonbroad.net seasonbutter.net seasondried.net seasonunderstand.net streetbehind.net streetbroad.net streetbutter.net streetunderstand.net tradebehind.net tradebroad.net tradebutter.net Reference: [1] https://www.microsoft.com/security/portal/threat/encyclopedia/Entry.aspx?Name=TrojanSpy:Win32/Nivdort.AL#tab-link-3 [2] https://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=TrojanSpy:Win32/Nivdort.A [3] http://community.websense.com/blogs/securitylabs/archive/2015/01/30/new-f0xy-malware-employs-cunning-stealth-amp-trickery.aspx [4] https://github.com/Yara-Rules/rules/ [5] http://www.neutralizethreat.com/2015/12/nivdort-code-obfuscation-and-dga.html
--
Alex Stanford - GIAC GWEB & GSEC,
Research Operations Manager,
SANS Internet Storm Center
/in/alexstanford


Comments