BizCN gate actor update
Introduction
The actor using gates registered through BizCN (always with privacy protection) continues using the Nuclear exploit kit (EK) to deliver malware.
My previous diary on this actor documented the actor's switch from Fiesta EK to Nuclear EK in early July 2015 [1]. Since then, the BizCN gate actor briefly switched to Neutrino EK in September 2015 [2, 3]; however, it appears to be using Nuclear EK again.
Our thanks to Paul, who submitted a pcap of traffic by the BizCN gate actor to the ISC.
Details
Paul's pcap showed us a Google search leading to the compromised website. In the image below, you can also see Nuclear EK from zezetap.xyz.
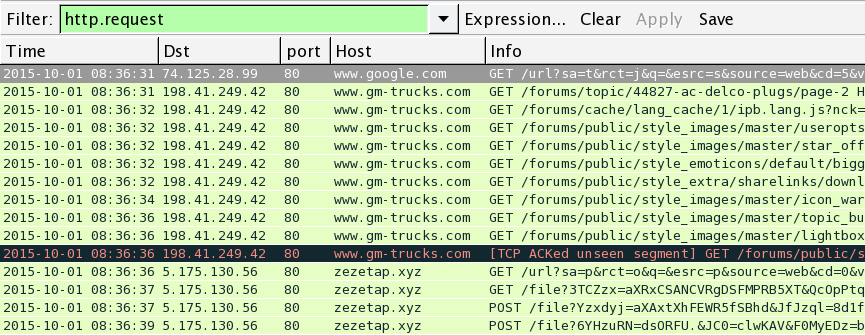
Shown above: A pcap of the traffic filtered by HTTP request.
No payload was found in this EK traffic, so the Windows host viewing the compromised website didn't get infected. The Windows host from this pcap was running IE 11, and URLs for the EK traffic stop after the last two HTTP POST requests. These URL patterns are what I've seen every time IE 11 crashes after getting hit with Nuclear EK.
A key thing to remember with the BizCN gate actor is the referer line from the landing page. This will always show the compromised website, and it won't indicate the BizCN-registered gate that gets you there. Paul's pcap didn't include traffic to the BizCN-registered gate, but I found a reference to it in the traffic. Remember, traffic from this actor always has a BizCN-registered gate.

Shown above: Flow chart for EK traffic associated with the BizCN gate actor.
How did I find the gate in this example? First, I checked the referer on the HTTP GET request to the EK's landing page.
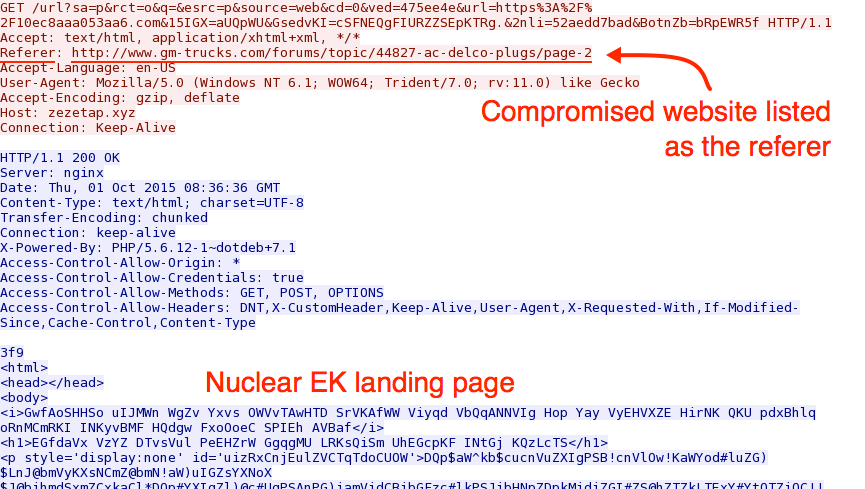
Shown above: TCP stream for the HTTP GET request to the Nuclear EK landing page.
That referer should have injected script pointing to the BizCN gate URL, so I exported that referer page from the pcap and save it as a text file.
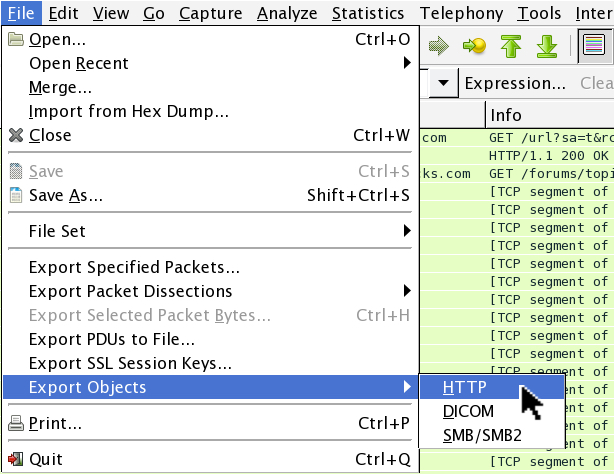
Shown above: How to export objects from HTTP traffic in Wireshark.
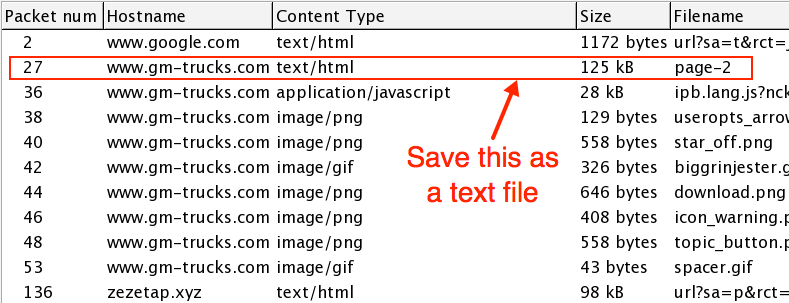
Shown above: The object I exported from the pcap.
I searched the HTML text from the compromised website and found the BizCN gate URL as shown below.
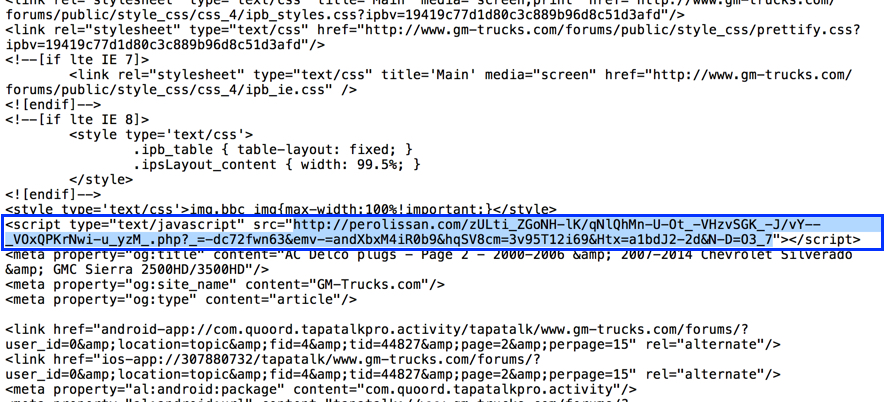
Shown above: Malicious script in page from the compromised website pointing to URL on the BizCN-registered gate domain.
The BizCN-registered domain was perolissan.com, and pinging to it showed 136.243.25.242 as the IP address. As usual, domains registered by this actor are privacy-protected.
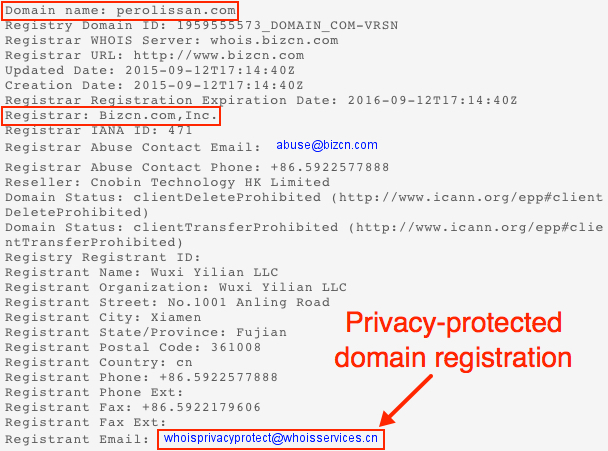
Shown above: Whois information on perolissan.com.
This completes my flow chart for the BizCN gate actor. The domains associated from Paul's pcap were:
- www.gm-trucks.com - Compromised website
- 136.243.25.242 - perolissan.com - BizCN-registered gate
- 5.175.130.56 - zezetap.xyz - Nuclear EK
Final words
Recently, I've had hard time getting a full chain of infection traffic from the BizCN gate actor. Paul's pcap also had this issue, because there was no payload. However the BizCN gate actor is still active, and many of the compromised websites I've noted in previous diaries [1, 4] are still compromised.
We continue to track the BizCN gate actor, and we'll let you know if we discover any significant changes.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://isc.sans.edu/forums/diary/BizCN+gate+actor+changes+from+Fiesta+to+Nuclear+exploit+kit/19875/
[2] http://malware-traffic-analysis.net/2015/09/11/index.html
[3] http://malware-traffic-analysis.net/2015/09/14/index.html
[4] https://isc.sans.edu/diary/Actor+using+Fiesta+exploit+kit/19631


Comments