A look through the spam filters - examining waves of Upatre malspam
Introduction
Any email filtering worth its cost should block numerous messages every day. Most people are content to ignore these blocked messages; however, I'm always interested to see what exactly is being blocked. Perhaps the most common type of malicious spam (malspam) I see from the spam filters is Upatre-based malspam.
I've written diaries before about specific waves of Upatre malspam sending the Dyre banking Trojan [1, 2]. I've only noticed emails with .zip file attachments from this type of malspam. I recently looked through my organization's spam filters and found the same thing again. In this case, we found three different themes of malspam sent in a three-hour window, and all had Upatre malware sending Dyre. Let's take a closer look at these samples of Upatre/Dyre malspam from Wednesday, 2015-09-09.
A three-hour window of malspam
Below is an image of blocked malspam with malicious attachments on Wednesday 2015-09-09 from 05:00 to approximately 08:00 CDT. Some of the information has been redacted so I could share.
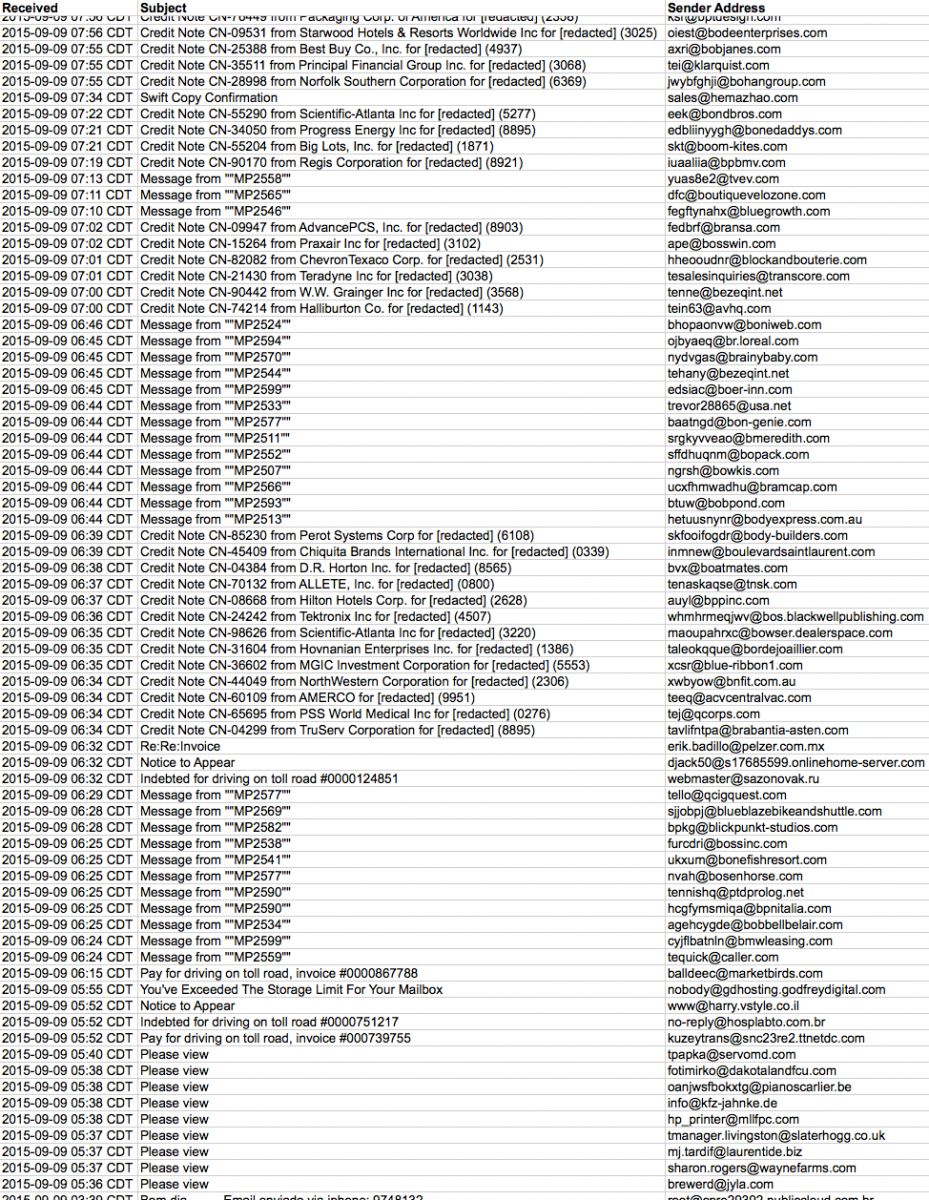
Shown above: A three-hour windows of blocked malspam from Wednesday, 2015-09-09.
In this three-hour window, we see several different types of subject lines. Let's concentrate on the top three:
- Subject lines that start with: Credit Note CN-
- Subject lines that start with: Message from "
- Subject line: Please view
Each of the above waves is botnet-based Upatre malspam. A random check of the email headers shows almost every message came from a different IP address.
Malware from the first and second waves has the same file hash
The first wave is credit note-themed malspam. Other sources have reported about this particular theme in recent days [3, 4]. The subject line for each message contains the domain name of the recipient's email address. The subject lines, message text, and attachment names are different for each message. The attachment is a .zip archive that contains an executable with an .scr file extension.

Shown above: Credit note-themed malspam from Wednesday, 2015-09-09.
The second wave is OMP-themed malspam. At least one other organization saw this malspam today [5]. This type of malspam has the same spoofed sender, and the attachments all have the same name: omp cheque.zip. Each message also has a spoofed sending address ending with the recipient's domain. The attachment is a .zip archive that contains an executable named omp cheque.scr.
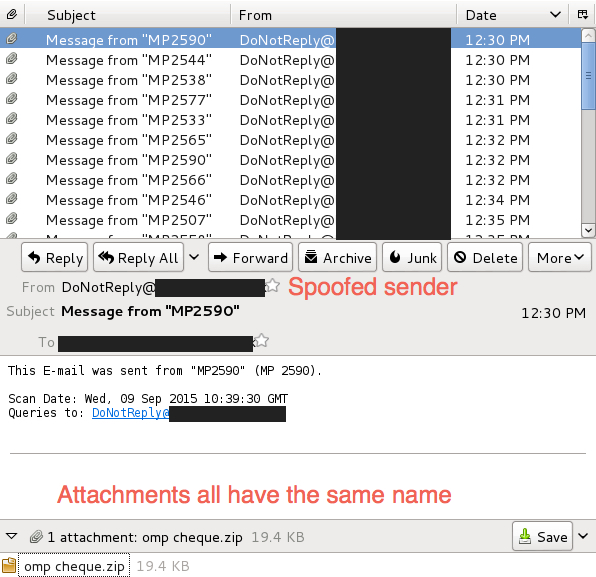
Shown above: OMP-themed malspam from Wednesday, 2015-09-09.
Examine the attachments, and you'll find the same file hash for the .scr file from both waves of malspam. The extracted malware is the same for all these emails.
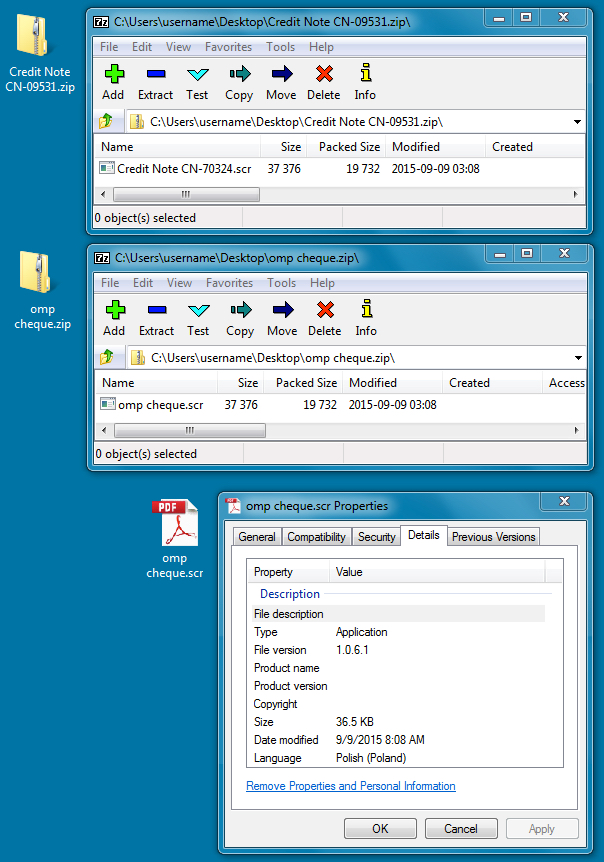
Shown above: Malware from the credit note and OMP-themed malspam.
The third wave is fax-themed malspam discussing a new contract. The message text is the same for each email, but the attachments all have different file names. The attachment is a .zip archive that contains an executable with an .exe file extension.
Malware from the third wave is similar to the first two
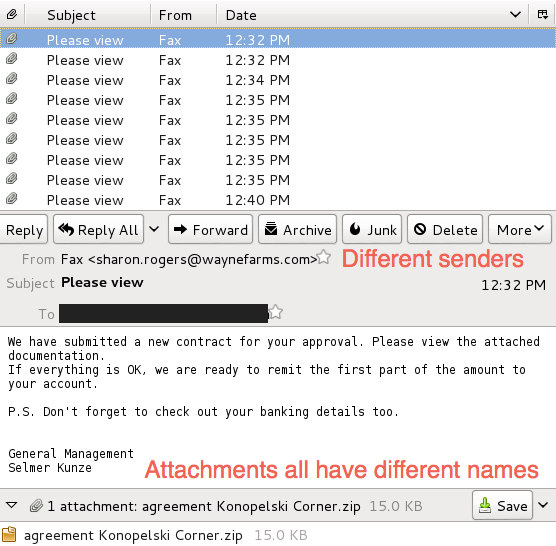
Shown above: Fax-themed malspam from Wednesday, 2015-09-09.
The file attachment is similar in size to the other two waves of emails.
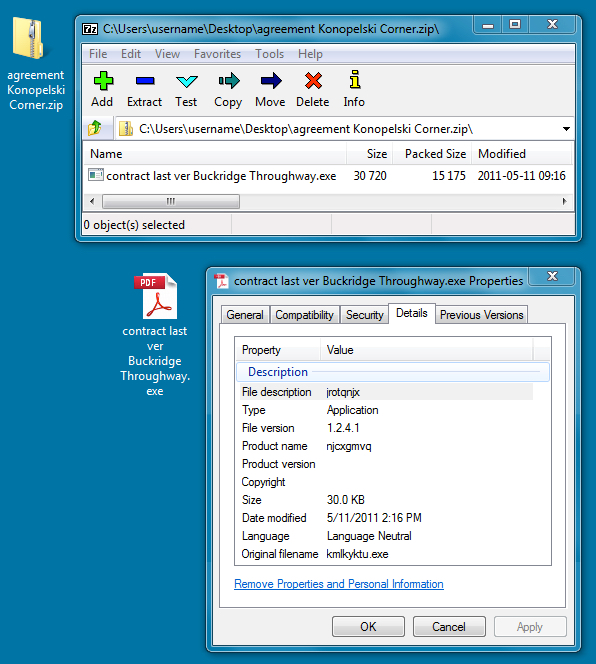
Shown above: Malware from the fax-themed malspam.
Malware analysis from the first and second waves
Below is data on the extracted Upatre malware from the first and second waves of malspam:
File name: contract last ver Buckridge Throughway.exe and various other names
File size: 30.0 KB ( 30720 bytes )
MD5 hash: 287b713e0dade68b08b036de0118dad9
SHA1 hash: 72ae7232261f243043126f7749604ed985c8808e
SHA256 hash: b7578820f1369a3f0b620c8a6365fd7613e3d6b4cc9916c6fb32a2e6e2a346fb
First submission to Virus Total: 2015-09-09 10:44:24 UTC
Detection ratio: 9 / 56
https://www.virustotal.com/en/file/b7578820f1369a3f0b620c8a6365fd7613e3d6b4cc9916c6fb32a2e6e2a346fb/analysis/
https://www.hybrid-analysis.com/sample/b7578820f1369a3f0b620c8a6365fd7613e3d6b4cc9916c6fb32a2e6e2a346fb?environmentId=4
Traffic from an infected host:
197.149.90.166 port 12125 - Upatre callback, campaign identifier 09-GB77
85.248.2.228 port 443 - encrypted traffic
217.168.210.122 port 443 - https://217.168.210.122/img917.png
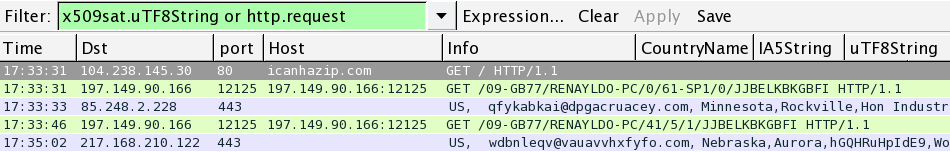
Shown above: Creative filtering of the traffic in Wireshark. Picture is edited--click on the image to see what it actually looks like.
Dyre malware found on an infected host:
File name: C:\Users\username\AppData\Local\lpCXRrcEpmnPjnb.exe
File size: 605.5 KB ( 620032 bytes )
MD5 hash: 051eeea32bd66d207838f1ac640bd4f8
SHA1 hash: f17655c2bf62572e4db84de2b8473cb4941baceb
SHA256 hash: 010e4d5c4668a04274c30a144021d56981da5991a3f7e26379db0782ef1632af
First submission to Virus Total: 2015-09-09 11:32:49 UTC
Detection ratio: 7 / 57
https://www.virustotal.com/en/file/010e4d5c4668a04274c30a144021d56981da5991a3f7e26379db0782ef1632af/analysis/
https://www.hybrid-analysis.com/sample/010e4d5c4668a04274c30a144021d56981da5991a3f7e26379db0782ef1632af?environmentId=5
Malware analysis from the third wave
Extracted Upatre malware from the third wave of malspam:
File name: omp cheque.scr and various other names
File size: 36.5 KB ( 37376 bytes )
MD5 hash: 4c0915119ca00a67b1fb59de3ae08592
SHA1 hash: 14d5e5efcc06be76944cf3036fe880c785489e0b
SHA256 hash: a61b06f03909b05e8130c7347cd66af6757280a7182880963f2f27c9071c8e51
First submission to Virus Total: 2015-09-09 11:46:07 UTC
Detection ratio: 17 / 57
https://www.virustotal.com/en/file/a61b06f03909b05e8130c7347cd66af6757280a7182880963f2f27c9071c8e51/analysis/
https://www.hybrid-analysis.com/sample/a61b06f03909b05e8130c7347cd66af6757280a7182880963f2f27c9071c8e51?environmentId=4
Traffic from an infected host:
197.149.90.166 port 12127 - Upatre callback, campaign identifier 09-GB22
82.160.64.45 port 443 - https://82.160.64.45/img922.png
85.248.2.228 port 443 - encrypted traffic
45.46.50.225 port 443 - encrypted traffic
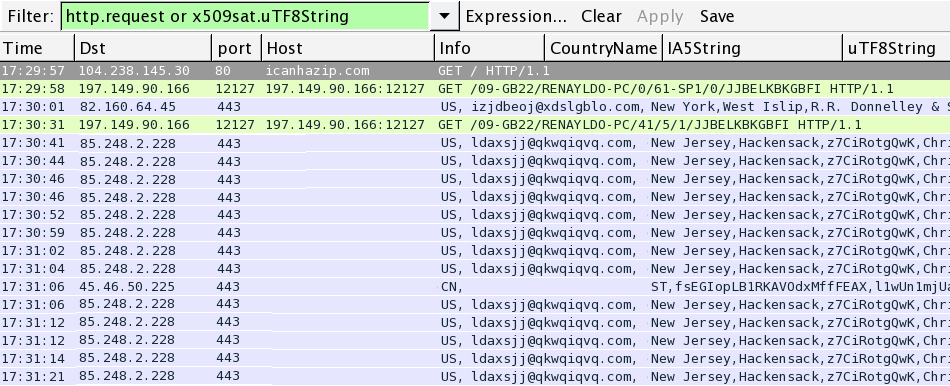
Shown above: Creative filtering of the traffic in Wireshark. Picture is edited--click on the image to see what it actually looks like.
Dyre malware found on infected host:
File name: C:\Users\username\AppData\Local\bitTUngcmhShQVQ.exe
File size: 610.0 KB ( 624640 bytes )
MD5 hash: abea26ae7faf459012faa965d5bc6332
SHA1 hash: 9de25f25ab67e78e3abaca0811f4330c3e2f80a1
SHA256 hash: 4e07c2d3dd01e9553215a9afa02a513e95ad629ffc21c638bc191b42eca7d3ce
First submission to Virus Total: 2015-09-09 12:34:00 UTC
Detection ratio: 5 / 56
https://www.virustotal.com/en/file/4e07c2d3dd01e9553215a9afa02a513e95ad629ffc21c638bc191b42eca7d3ce/analysis/
https://www.hybrid-analysis.com/sample/4e07c2d3dd01e9553215a9afa02a513e95ad629ffc21c638bc191b42eca7d3ce?environmentId=1
Network alerts from the infection traffic
The image below shows some of the alerts I saw when playing back one of the pcaps of my infection traffic on Security Onion.
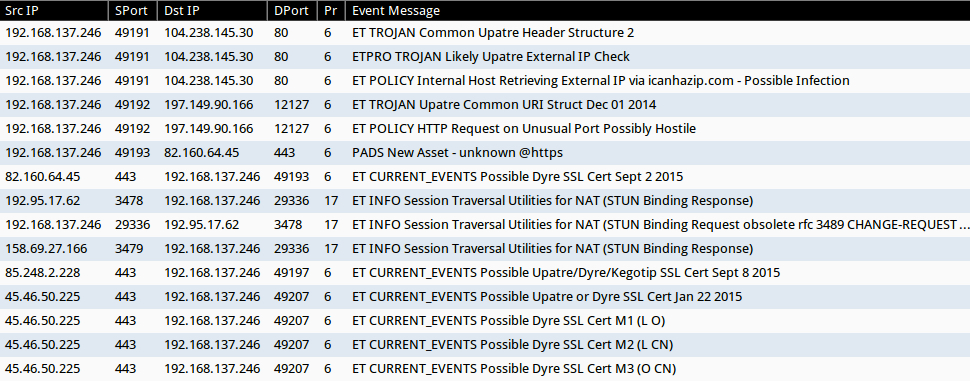
Shown above: Events from Squil on Security Onion using Suricata with the Emerging Threats (ET) and ET Pro rulesets.
Final words
Much like Liam Neeson's character in the Taken movie series, botnets serving Upatre malspam are relatively mature and relentless in their pursuit (the pursuit of continually spewing this sort of malspam). Also, like the Taken movie series, the whole thing is getting kind of old. In the security field, most of us are likely to ignore this malspam, because there's very little chance we'll ever be infected ourselves.
However, we see Upatre malspam almost every day, so it must somehow make a profit for criminals behind this operation. With that in mind, some of us will continue searching the spam filters to see if anything changes.
Malware samples and pcap files for this diary are available from hybrid-analysis.com links above.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://isc.sans.edu/forums/diary/UpatreDyre+the+daily+grind+of+botnetbased+malspam/19657/
[2] https://isc.sans.edu/forums/diary/UpatreDyre+malspam+Subject+eFax+message+from+unknown/19713/
[3] http://blog.dynamoo.com/2015/09/malware-spam-credit-note-cn-60938-from.html
[4] http://myonlinesecurity.co.uk/invoice-or-credit-note-from-random-companies-fake-pdf-malware/
[5] http://myonlinesecurity.co.uk/message-from-mp2541-fake-pdf-malware/


Comments