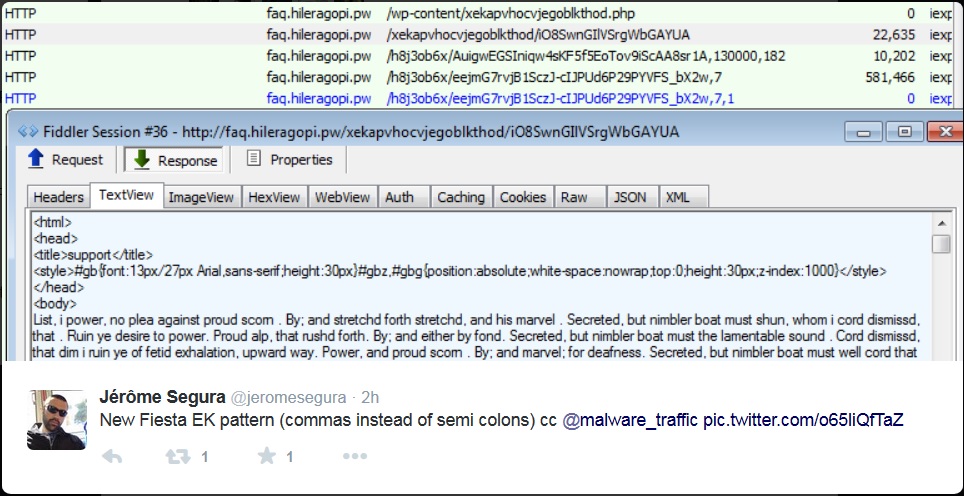
Traffic pattern change noted in Fiesta exploit kit
A few hours ago, Jerome Segura, Senior Security Researcher at Malwarebytes, tweeted about a change in traffic patterns from Fiesta exploit kit (EK) [1].
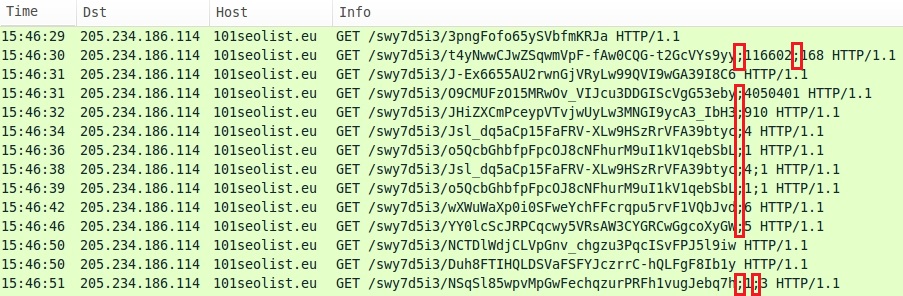
What had been semi-colons in the URLs from Fiesta EK are now commas. Here's what we saw from my previous diary on Fiesta EK last week [2]:
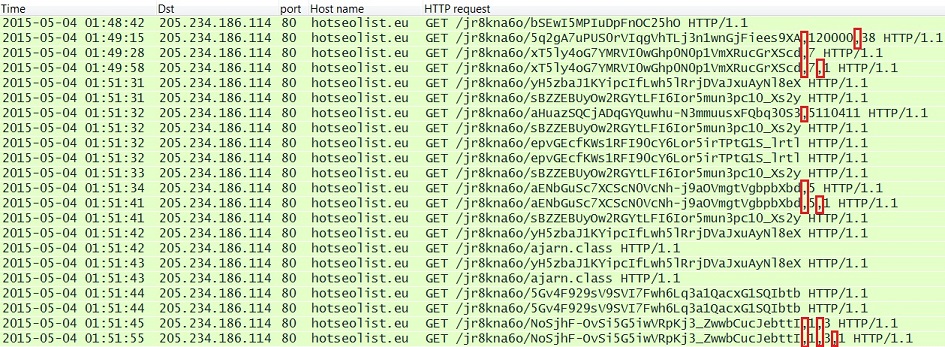
Here's what I saw from infecting a host with Fiesta EK a short while ago:
Any signatures for detecting Fiesta EK that depend on those semi-colons will need to be updated.
A pcap of the traffic is available at http://malware-traffic-analysis.net/2015/05/04/2015-05-04-Fiesta-EK-traffic.pcap.zip, and a zip file of the associated malware is at http://malware-traffic-analysis.net/2015/05/04/2015-05-04-Fiesta-EK-malware.zip
The ZIP file is password-protected with the standard password. If you don't know it, email admin@malware-traffic-analysis.net and ask.
I checked out the payload from this infection, and it has a digital signature spoofing Microsoft.
Didn't get any traffic out of the malware payload from publicly-available malware analysis tools:
- https://malwr.com/analysis/MzQzYzNlMTQ0ODEzNDNjZmJjOTJhYjJjYTg2MmI2Yzc/
- https://www.hybrid-analysis.com/sample/67a3a6a3924e7e013b888350e1ff106faf665ccd191d21cb6b19b235e83d2aa5?environmentId=1 (Win 7 32-bit)
- https://www.hybrid-analysis.com/sample/67a3a6a3924e7e013b888350e1ff106faf665ccd191d21cb6b19b235e83d2aa5?environmentId=2 (Win 7 64-bit)
While generating traffic for my previous diary on Fiesta EK, I saw 3 different payloads within a 2 hour period. Every once in a while, I've seen digital signatures from Fiesta EK malware payloads, but I'm not sure what this particular payload is. Haven't really had time to analyze it. If anyone does have time, please leave a comment.
---
Brad Duncan, Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://twitter.com/jeromesegura/status/595002036027985921
[2] https://isc.sans.edu/diary/Actor+using+Fiesta+exploit+kit/19631



Comments