FreeBSD Denial of Service advisory (CVE-2004-0230)
A vulnerability has been discovered by Johnathan Looney at the Juniper SIRT in FreeBSD (base for Junos and many other products) in the way that FreeBSD processes certain TCP packets (https://www.freebsd.org/security/advisories/FreeBSD-SA-14:19.tcp.asc) If you send TCP SYN packets for an existing connection (i.e. the correct source IP, source port, destination IP, destination port combination) the operating system will tear down the connection.
The attack is similar to the "slipping in the TCP window" attack described back in 2004 by Paul Watson (http://packetstormsecurity.com/files/author/3245/), but using SYN packets instead of RST. One of the Handlers has successfully reproduced the attack in their lab.
For those of you that don't have FreeBSD in your environment, you probably do. There are a number of products that utilise FreeBSD as their base operating system. A few that spring to mind are OSX, Bluecoats, CheckPoint, Netscaler and more (A partial list is here http://en.wikipedia.org/wiki/List_of_products_based_on_FreeBSD).
Keep an eye out for updates from your vendors, Juniper's is here --> http://kb.juniper.net/InfoCenter/index?page=content&id=JSA10638&cat=SIRT_1&actp=LIST
M
https://yourfakebank.support -- TLD confusion starts!
Pretty much ever since the new top level domain (TLD) ".biz" went online a couple years ago, and the only ones buying domains in this space were the scammers, we kinda knew what would happen when ICANN's latest folly and money-grab went live. It looks like a number of the "new" top level domains, like ".support", ".club", etc have now come online. And again, it seems like only the crooks are buying.
We are currently investigating a wave of phishing emails that try to lure the user to a copy of the Bank of America website. The main difference, of course, is that any login credentials entered do not end up with Bank of America, but rather with some crooks, who then help themselves to the savings.
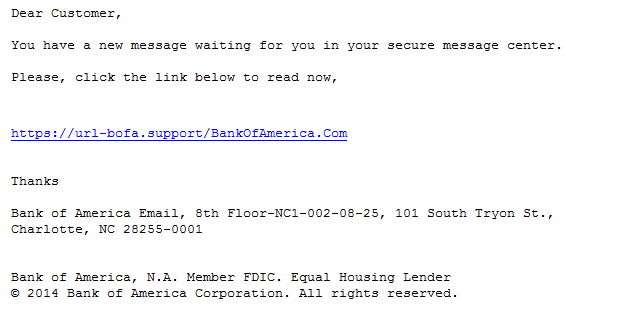
Phishing emails per se are nothing new. But it appears that URLs like the one shown in the phishing email above have a higher success rate with users. I suspect this is due to the fact that the shown URL "looks different", but actually matches the linked URL, so the old common "wisdom" of hovering the mouse pointer over the link to look for links pointing to odd places .. won't help here.
But wait, there's more! Since the crooks in this case own the domain, and obviously trivially can pass the so-called "domain control validation" employed by some CA's, they actually managed to obtain a real, valid SSL certificate!
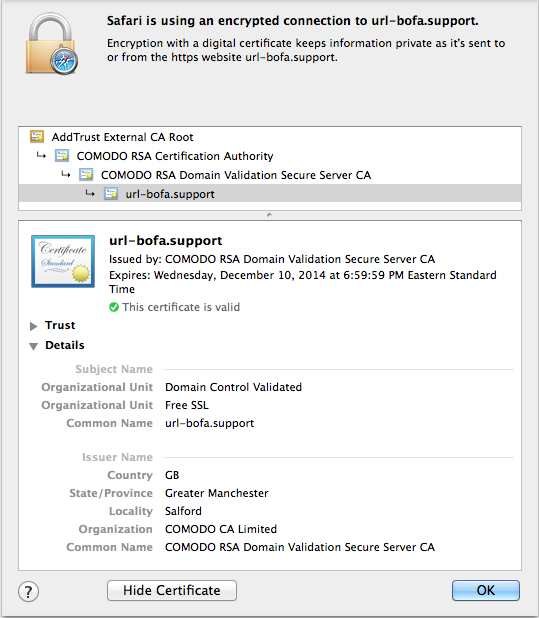
Quoting from the Certificate Authority's web site:
Comodo Free SSL is a fully functional Digital Certificate, recognized and trusted by 99.9% of browsers. Your visitors will see the golden padlock and won't see security warnings. What will you get:
- Ninety day free SSL Certificate (other CAs offer 30 days maximum.)
- Issued online in minutes with no paperwork or delays
- Highest strength 2048 bit signatures / 256 bit encryption
- Signed from the same trusted root as our paid certificates
- Recognized by all major browsers and devices
They don't mention why they think any of this is a good idea.
Addition of SSL to the phish means that another "scam indicator" that we once taught our users is also no longer valid. When a user clicks on the link in the phishing email, the browser will actually show the "padlock" icon of a "secure site". See the screenshot below.
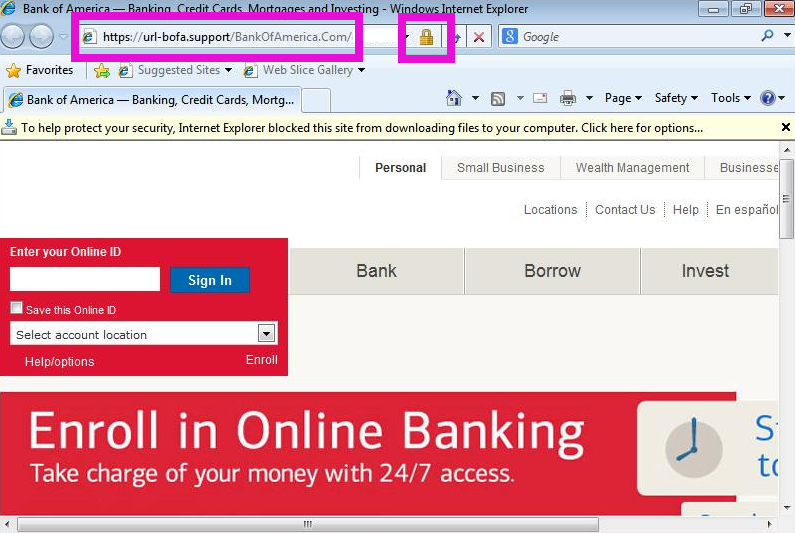
If you have seen other recent banking phishes that use new top level domains and/or valid SSL certificates, please let us know via the contact form, or the comments below!


Comments