Checking for vulnerabilities in the Smart Grid System
by Manuel Humberto Santander Pelaez (Version: 1)
SCADA systems are not composed the same way as regular IT systems. Therefore, the risk and vulnerability assessment cannot be performed as it is done for any other IT system. The most important differences are:
- SCADA Pentesting should not be done in production environment: SCADA devices are very fragile and some activities that could pose harmless to regular IT environments could be catastrophic to the process availability. Think of massive blackouts or no water supply for a city.
- SCADA devices have specific outputs for the industrial process they are controlling. The architecture and operating systems are not the same, so risks assessment approach is not performed in the same way. For electrical systems, we need to address devices belonging to the Advanced Metering Infrastructure (AMI), Demand Response (DR), Distributed Energy Resources (DER), Distributed Grid Management (DGM), Electric Transportation (ET) and Wide Area Monitong, Protection and Control (WAMPAC). This means we need to address devices like the following, instead of conventional network devices, services, laptops, desktop computers or mobile devices:
| AMI | Meters |
| Relays | |
| Aggregators | |
| Access points | |
| DR | Energy Resources |
| Digital Control Unit | |
| DER | DER Managed generation and storage devices |
| Customer Energy Management System | |
| DGM | Automated Reclosure |
| Remote Fault Indicators | |
| Capacitor Banks | |
| Automated Switches | |
| Load Monitor | |
| Substation Breakers | |
| WAMPAC | Phasor Measurement Units |
| Device which includes Phasor Measurement Unit capabilities | |
| Field Deployed Phasor Data Concentrator | |
| Field Deployed Phasor Gateways |
Table 1: Devices in the Smartgrid Network
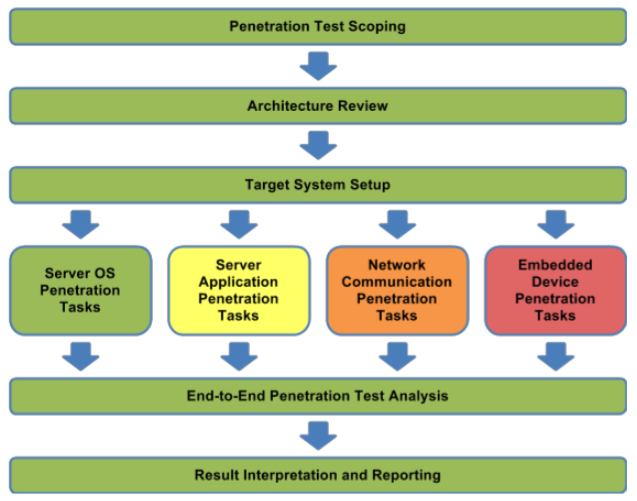
This means we need to considering a specific methodology for this type of infrastructure that leads to effective risk mitigation for proper detection of vulnerabilities in the smartgrid system. I want to recommend one today named Guide to Penetration Testing for Electric Uitilities created by the National Electric Sector Cybersecurity Organization Resource (NESCOR). This metodology is composed by the following steps:
Source: http://www.smartgrid.epri.com/doc/NESCORGuidetoPenetrationTestingforElectricUtilities-v3-Final.pdf
Let's explain the steps a little bit:
- Penetration Test Scoping: You need to decide which sector of the entire system will be the target of the assessment. Could be a substation, generation plant or any other device listed in table 1. The scope could even be the entire system.
- Architecture Review: You want to learn the context of the entire system. This is the first step of information acquisition. Can be done checking the documentation of the system and analyzing the configuration of the devices part of the scope.You can also check for information in the same way as it is done with conventional pentesting like google, shodan, maltego and social networks.
- Target System Setup: You don't want to perform a pentesting in a smartgrid live production environment. Instead, you need to setup an environment with the same configuration, as much as possible, to the live configuration of the smartgrid production environment. That's how we can get a full list of the vulnerabilities performing even dangerous test without affecting the availability of the electrical service.
- Server OS, Server application, Network Communication and Embedded device penetration tasks: Those are the specific pentest tasks within the target systems. You can use several tools like
- End to end penetration testing analysis: You need to ensure that all possible inputs from external systems to all systems in the scope have been tested and evaluated as possible vulnerable points for attacks.
- Result interpretation and reporting: As always, you need to develop a report including the vulnerabilities that could be exploited, the risks associated, the remediation steps and other recommendations that could be applied.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments