McAfee DAT troubles
Thanks to reader Dan for sharing the following information:
McAfee has confirmed that incremental DAT 6682 may trigger message scan failures and a system crash in GroupShield Exchange (MSME), GroupShield Domino, and McAfee Email Gateway 7 (MEG). McAfee recommends that customers do NOT upload DAT 6682.
More information will be available on the McAfee KnowledgeBase (https://mysupport.mcafee.com) in article KB70380 (https://kc.mcafee.com/
Challenge: What can you do with Funky Directory Names (Part 2)
Following up on last weeks challenge I'd like to add a new element to the challenge, then review some of the EXCELLENT comments we received from our readers. First lets add a new element to the challenge and see how you can creatively make use of symbolic links on Windows. I'll throw a few things out there to get the ball rolling.
1) Using Infinitely recursive directories to defeat directory searching scripts: As described in this excellent presentation on "Offensive Countermeasures" by my friends John Strand and Paul Asodoorian, you can create symbolic links to the current working directory to cause directory searches to get stuck in an infinite loop. They begin talking about it at the 25 minute mark in this video ::http://www.youtube.com/watch?v=p0gWAbMjg1U In short you can create symbilic link directories to the current directory and cause anyone searching your hard drive (including malware and antivirus scans) to get caught in an infinite loop.
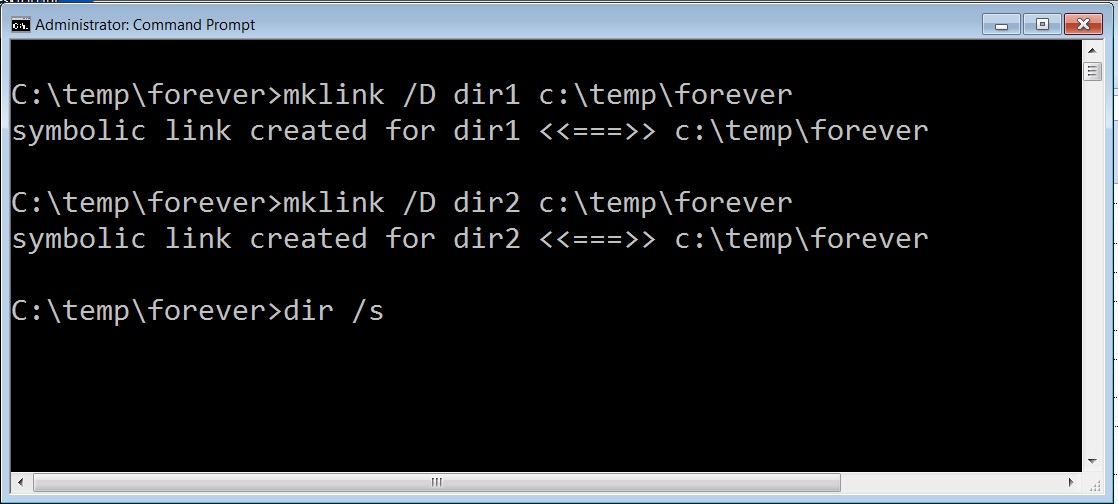
2) Create links to devices such as boot sector and to alternate data streams:
You can use symbolic links to access items in alternate data streams and items in disk partitions that are normally not easily accessed. For example, if you have a separate boot partition you can use symbolic links to access it and even hide files in It.
http://pauldotcom.com/2010/10/windows-7-symbolic-links-and-h.html
3) Symbolic links to Volume Shadow Copies:
Windows Volume shadows copies automatically maintain backups of the last 5-15 percent of all changes on your computer. It is a bit like Apple's time machine without the fancy GUI or the offline storage. This link shows you how to step back in time and see exactly what was on your systems a few days ago. Oh, You thought you deleted those files? You might want to check this out.
http://computer-forensics.sans.org/blog/2011/06/09/vscs-logparser
Interesting, you can also stage malware in volume shadow copes and then execute the malware directly from the shadow copy.
So there you go. What can you do with Symbolic links? We still don't have an explanation for the error message or strange behavior noted in the last challenge. What can you tell us about them? POST A COMMENT or SEND ME AN EMAIL! If you missed them here are some of the great comments we got from readers of the last challenge:
Original Comments and challenge are here: https://isc.sans.edu/diary/Challenge+What+can+you+do+with+funky+directory+names+/12958
Readers comments: Add space to filename to bypass Digital signatures on Microsoft policies.
This was a very interesting comment from reader Aaron. It seems that Aaron had some success bypassing digital signature checks. He reports that the process that checks a digital signature may ignore spaces at the end of the file causing windows to check the actual file with a good signature. The result is that malware named "svchost.exe " (svchost.exe with a space at the end) may appear to be digitally signed to some apps. That's all I'll say about that one.
Reader comments: Creating Extended character directory names with the alt key/numeric keypads.
As you probably know, we can use the ALT key and the Numeric keypad to type extended ASCII characters. Combine that with the ability to create files and directories with normally prohibited characters and you've got some PRETTY directories on your hands. Create smiley fact, hearts, diamonds and other interesting directories on your windows systems.
http://alt-codes.org/laptop/
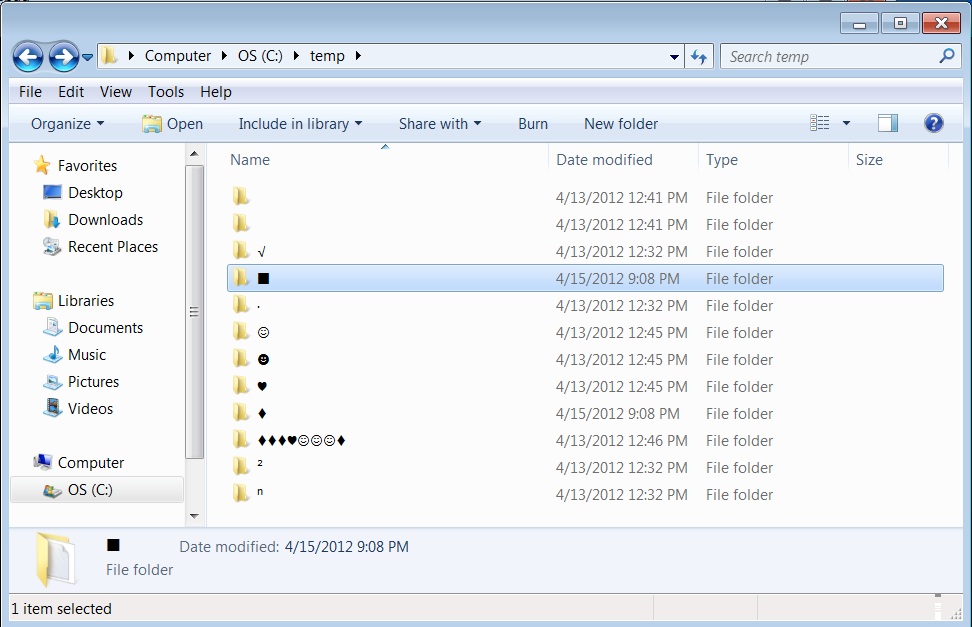
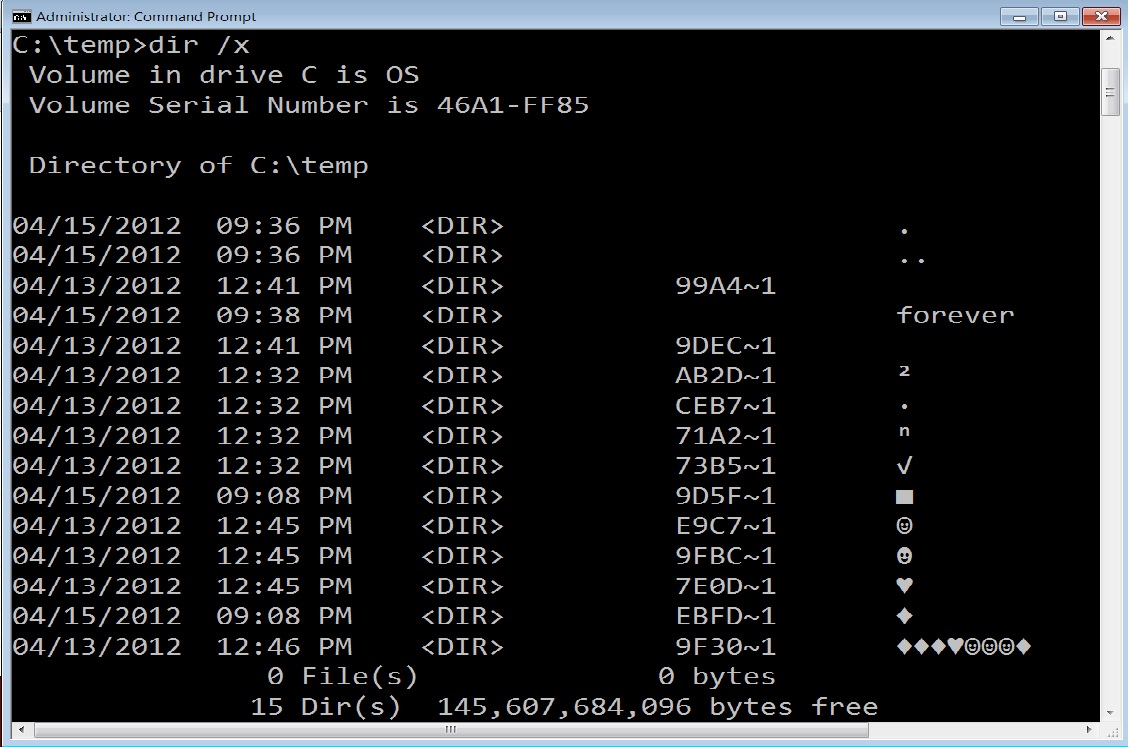
Reader comments: Still no answer for the strange 8.3 names given to files/directories
We had several excellent comments and emails on the strange 8.3 directory names created when you create a directory or file with a character in its name that is prohibited by the normal file/directory creation process. Normally 8.3 shortnames are only given to files or directories that are longer than 8 characters in length. In this case, the 8.3 names are assigned seemingly at random to these files event though they are not more than 8 characters long.
HEY! I'm teaching SANS SEC560 BOOTCAMP Style in Augusta GA June 11th - 16th. Sign up today! http://www.sans.org/community/event/sec560-augusta-jun-2012


Comments