Unpatched Exploit: Skype for Mac OS X
--- Update:
There has been an update to Skype for Mac OS X. It is recommended that you update. Latest version seems to be 5.1.0.922. It is not clear from the Skype website as to addressing the below issue but updating is a good idea.

According to a Pure Hacking Blog Entry = http : //www.purehacking.com/blogs/gordon-maddern/skype-0day-vulnerabilitiy-discovered-by-pure-hacking and The Register UK = http : //www.theregister.co.uk/2011/05/06/skype_for_mac_critical_vulnerability/
There is a 0 Day exploit that exists for Skype on MAC. Windows and Linux are unaffected. Some best practices for Skype include setting your messages to only allow from Contacts. This does not protect you from infected contacts but it might help.
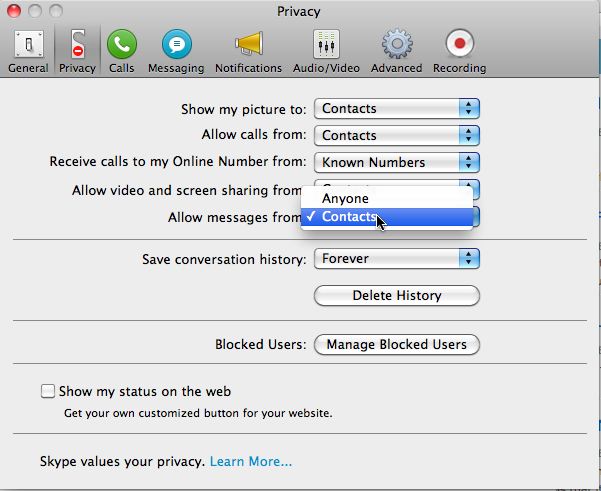
Please take measures to protect yourself. We are not aware of this being exploited in the wild and as most of us might use the operating system affected, we are both personally and professionally interested.
Richard Porter
--- ISC Handler on Duty
Updated Exploit Index for Microsoft
We have received early notification that Microsoft is updating the method of guidance for patching. In 2008 Microsoft published its first Exploit Index to better guide customers on likelihood of getting "Sploited." This new notification reflects a change in the index ratings.
| 1 | Consistent exploit code likely |
| 2 | Inconsistent exploit code likely |
| 3 | Functioning exploit code unlikely |
Reviewing the publication by Microsoft, I think they are saying:
1 - Code easy to create and or already created.
2 - Moderate to create or maybe a DoS and or that results are not consistent.
3 - They don't feel the risk is high.
As always, the Storm Center Handlers will continue to independently evaluate "Microsoft Patch Tuesday" for "Reboot Wednesday" and provide our guidance :) On their site, if you recall MS08-021 (Vulnerability in GDI Could (Did and does :) Allow Remote Code Execution)? MSFT rates that with an EIA of 1.
Also, in the notification they included early warning of a light patch month that includes a set of Office patches and 2003-2008 R2 set of server patches.
Finally, MSFT will be aggregating their Index into Current Software and older software.
"As of this month, we are making some changes to the rating system to make vulnerability assessment more clear and digestible for customers. Specifically, we will be publishing two Exploit-ability Index ratings per vulnerability- one for the most recent platform, the other as an aggregate rating for all older versions of the software. " -- technet.microsoft.com
Check out:
http : // technet.microsoft.com/en-us/security/cc998259.aspx <-- Index Definition
http : // tinyurl.com/6fygchn <-- Original Notice
http : / /www.microsoft.com/technet/security/bulletin/ms11-may.mspx <-- Advanced Notice
Richard Porter
--- ISC Handler on Duty


Comments